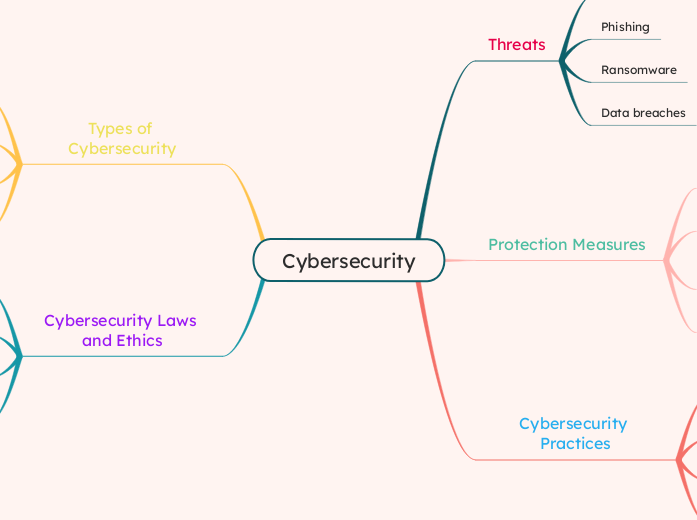
Cybersecurity
Threats
Malware
Phishing
Ransomware
Data breaches
Protection Measures
Firewalls
Encryption
Multi-Factor authentication MFA
Antivirus Software
Cybersecurity Practices
Strong Passwords
Regular Software updates
Employee training
Secure networks
Types of Cybersecurity
Network security
Cloud security
Application security
Information security
Cybersecurity Laws and Ethics
GDPR
CCPA
Ethical hacking
Digital forensics