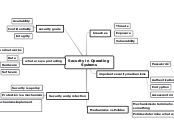
Security in Operating
Systems
breaches
Threats
Exposure
Vulnerability
impotant security mechanisms
Passwords
Password Selection Criteria
Attacks on Passwords
Use of Passwords
Authentication
Encryption
Access control mechanisms
Mechanisms vs Policies
Mechanisms determine how to do something
Policies determine what will be done
security goals
Availability
Confidentiality
Integrity
what are we protecting
Communications lines and networks
Data
Hardware
Software
Security and protection
Security is a policy
Protection is a mechanism
Protection mechanisms implement security
policies