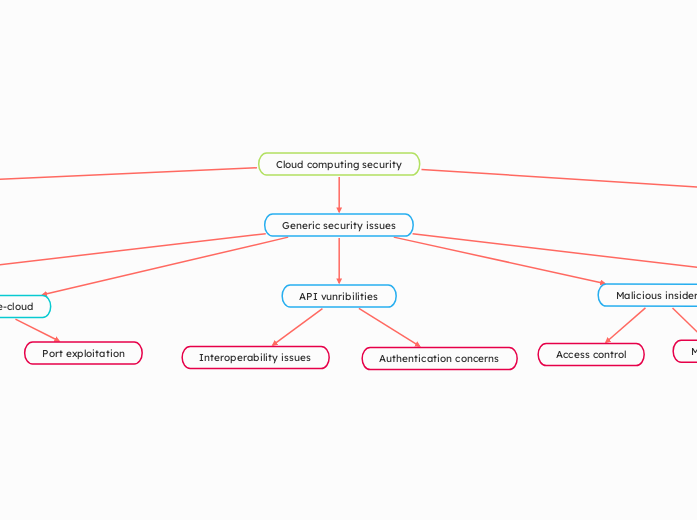
Cloud computing security
Generic security issues
API vunribilities
Interoperability issues
Authentication concerns
Access control
Malicious insiders
Monitoring
Authentication
Secure communication
credential theft
Authorization
Instrusion detection
Best practices
SLA compliance
Account Hijacking
Access control
Security policies
Monitoring
Counter measures
SYN analysis
Connection limits
Information collection
Port exploitation
Dos/DDos attacks
Man-in-the-cloud
Data security
Transit security
SSL/TLS
HTTP examination
Storage protection
Back up