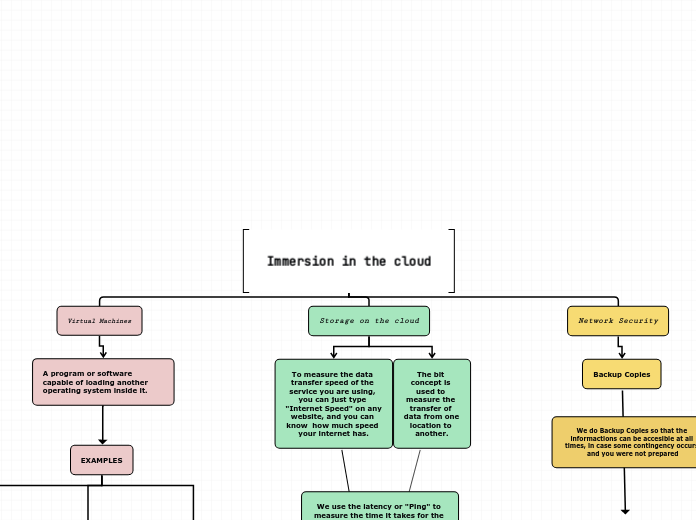
Immersion in the cloud
Virtual Machines
A program or software capable of loading another operating system inside it.
EXAMPLES
Virtualbox
Hyper-V
Xen
VMWare Workstation
Windows SandBox
Boot Camp
Parallels Desktop
Quemu
Veertu
Storage on the cloud
To measure the data transfer speed of the service you are using, you can just type "Internet Speed" on any website, and you can know how much speed your internet has.
Internet
An IP(Internet Protocol) is a set of numbers that is used to identify and logically locate a computer equipment.
Identifies the computer equipment or mobile service, web page or network server, also Redirects Internet traffic and send e-mails to email imbox .
The most common nomenclatures used to define storage are USB sticks, RAM memory and Storage in the Cloud.
What is RAM memory? this memory stores data and programs that the user is using at the moment and is known as volatile memory.
One of the great advantages of One Drive is that if your computer or electronic device breaks down or loses the USB memory it will be safe and your information won't be losed.
One drive is a cloud storage tool
The bit concept is used to measure the transfer of data from one location to another.
Network Security
Backup Copies
There are several Methods to store a backup of the information:
Compression
Redundancy
Reduplication
Encryption
We use the latency or "Ping" to measure the time it takes for the connection to communicate with the IP network.
We do Backup Copies so that the informactions can be accesible at all times, in case some contingency occurs and you were not prepared
Security
Virus
Spam
Phising
But there are some others dangers on the web:
Created by programmers to infect a system
Email that has not been requested and the purpose is to advertise
Crime of tricking people into sharing confidence information
All your personal data need to be protected like Age, address, phone number, personal email,etc. Because someone can easily access to it,but Firewall is a security mechanism that can help.
Here are some functions of firewall:
Establishes a barrier that prevents unauthorized access to the computer or network.
Blocks applications that may pose a risk to the computer or network.
Prevents unauthorized users from accessing the equipment and networks that connect the Internet.
This is important because we can experience something like a virtual attack. Or not even have an attack...but we can share by our own risk our information because of a cyberaddiction.
These are some kinds of dangers that we can experience on the internet:
Grooming
Cyberbullying
Cyberaddiction