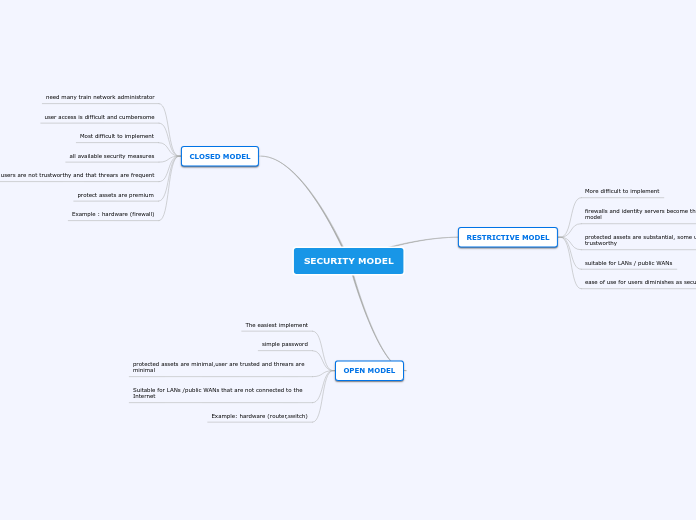
SECURITY MODEL
RESTRICTIVE MODEL
More difficult to implement
firewalls and identity servers become the foundation of this model
protected assets are substantial, some users are not trustworthy
suitable for LANs / public WANs
ease of use for users diminishes as security tightens
CLOSED MODEL
need many train network administrator
user access is difficult and cumbersome
Most difficult to implement
all available security measures
all users are not trustworthy and that threars are frequent
protect assets are premium
Example : hardware (firewall)
OPEN MODEL
The easiest implement
simple password
protected assets are minimal,user are trusted and threars are minimal
Suitable for LANs /public WANs that are not connected to the Internet
Example: hardware (router,switch)