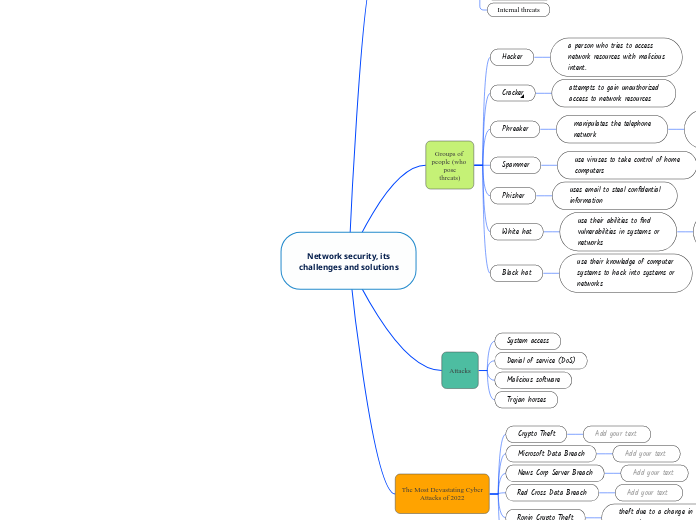
Network security, its
challenges and solutions
Threats to Network Security
Vulnerability
various devices (servers, PCs,
routers)
Threats
Unstructured threats
Structured threats
External threats
Internal threats
Groups of people (who pose
threats)
Hacker
a person who tries to access
network resources with malicious
intent.
attempts to gain unauthorized
access to network resources
Phreaker
manipulates the telephone
network
the goal is to penetrate the
telephone network to make free
long-distance calls.
Spammer
use viruses to take control of home
computers
Phisher
uses email to steal confidential
information
White hat
use their abilities to find
vulnerabilities in systems or
networks
report these vulnerabilities to
system owners so that they can be
fixed
Black hat
use their knowledge of computer
systems to hack into systems or
networks
Attacks
System access
Denial of service (DoS)
Malicious software
Trojan horses
The Most Devastating Cyber
Attacks of 2022
Crypto Theft
Add your text
Microsoft Data Breach
Add your text
News Corp Server Breach
Add your text
Red Cross Data Breach
Add your text
Ronin Crypto Theft
theft due to a change in security
protocol
Cash App Data Breach
A lot of sensitive financial
information was stolen in the hack.