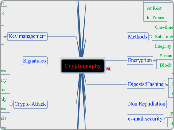
Cryptography
Uses
Confidentiality
Integrity
Availability
At Rest
In Transit
Methods
One-time pads
Substitution
Integrity
Encryption
Stream
Block
Initialisation Vector
Crypto systems
Symmetric
Asymmetric
Hybrid
Message digest
Hashing
Key management
Creation/distribution
Storage/destruction
Recovery
Key escrow
Digests/Hashing
MD5
SHA
HMAC
Signatures
Crypto Attack
Chosen plain text
Social engineering for key discovery
Brute force
Cipher-text only
Known plaintext
Frequency analysis
Chosen Cipher text
Implementation Attacks
Non Repudiation
e--mail security
PGP
S/MIME
PKI
Certificate Authority
Alternatives
Steganography
Watermarking
Network Security
SSL
VPN
IPSEC