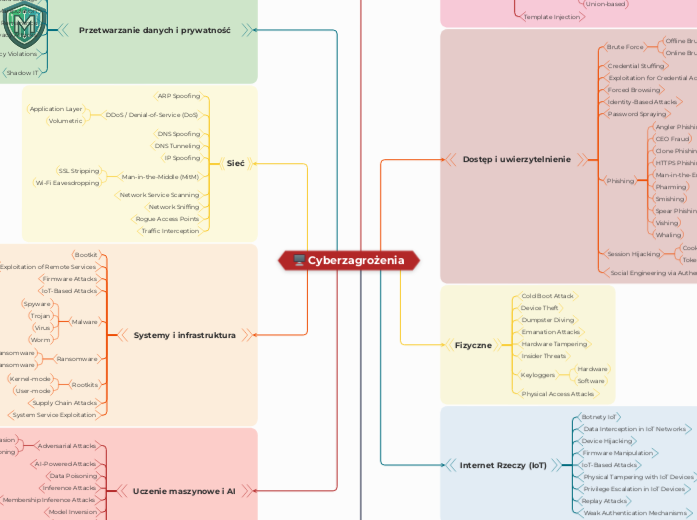
Cyberzagrożenia
Aplikacje
Code Injection Attacks
Cross-Site Request Forgery (CSRF)
Cross-Site Scripting (XSS)
DOM-based
Reflected
Stored
Deserialization of Untrusted Data
File Upload Vulnerabilities
Insecure Deserialization
Remote Code Execution (RCE)
Command Injection
File Inclusion
Server-Side Request Forgery (SSRF)
SQL Injection
Blind
Error-based
Union-based
Template Injection
Dostęp i uwierzytelnienie
Brute Force
Offline Brute Force
Online Brute Force
Credential Stuffing
Exploitation for Credential Access
Forced Browsing
Identity-Based Attacks
Password Spraying
Phishing
Angler Phishing
CEO Fraud
Clone Phishing
HTTPS Phishing
Man-in-the-Email (MitE)
Pharming
Smishing
Spear Phishing
Vishing
Whaling
Session Hijacking
Cookie Hijacking
Token Theft
Social Engineering via Authentication Systems
Fizyczne
Cold Boot Attack
Device Theft
Dumpster Diving
Emanation Attacks
Hardware Tampering
Insider Threats
Keyloggers
Hardware
Software
Physical Access Attacks
Internet Rzeczy (IoT)
Botnety IoT
Data Interception in IoT Networks
Device Hijacking
Firmware Manipulation
IoT-Based Attacks
Physical Tampering with IoT Devices
Privilege Escalation in IoT Devices
Replay Attacks
Weak Authentication Mechanisms
Inżynieria społeczna
Baiting
Business Email Compromise (BEC)
Impersonation
Pretexting
Quizzing
Smishing
Social Engineering Attacks
Tailgating
Vishing
Watering Hole Attack
Przetwarzanie danych i prywatność
Data Destruction
Data Leakage
Data Manipulation
Data Remanence
Differential Privacy Attacks
Privacy Violations
Data Breaches
Unauthorized Sharing
Shadow IT
Sieć
ARP Spoofing
DDoS / Denial-of-Service (DoS)
Application Layer
Volumetric
DNS Spoofing
DNS Tunneling
IP Spoofing
Man-in-the-Middle (MitM)
SSL Stripping
Wi-Fi Eavesdropping
Network Service Scanning
Network Sniffing
Rogue Access Points
Traffic Interception
Systemy i infrastruktura
Bootkit
Exploitation of Remote Services
Firmware Attacks
IoT-Based Attacks
Malware
Spyware
Trojan
Virus
Worm
Ransomware
Crypto Ransomware
Locker Ransomware
Rootkits
Kernel-mode
User-mode
Supply Chain Attacks
System Service Exploitation
Uczenie maszynowe i AI
Adversarial Attacks
Evasion
Poisoning
AI-Powered Attacks
Data Poisoning
Inference Attacks
Membership Inference Attacks
Model Inversion
Model Stealing
Trojaning Attacks