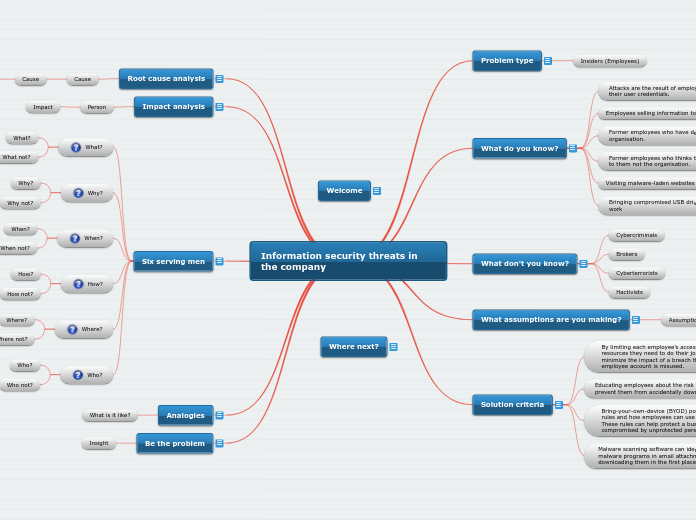
Information security threats in the company
Problem type
Insiders (Employees)
What do you know?
Attacks are the result of employees intentionally misusing their user credentials.
Employees selling information to Media or outsiders.
Former employees who have demoted to fired within the organisation.
Former employees who thinks that accumulated data belongs to them not the organisation.
Visiting malware-laden websites
Bringing compromised USB drives or other personal devices to work
What don't you know?
Cybercriminals
Brokers
Cyberterrorists
Hactivists
What assumptions are you making?
Assumption
Solution criteria
By limiting each employee’s access to only the specific resources they need to do their job, organizations can minimize the impact of a breach that occurs when an employee account is misused.
Educating employees about the risk of malware can do a lot to prevent them from accidentally downloading ransomware.
Bring-your-own-device (BYOD) policies help set the ground rules and how employees can use personal devices at work. These rules can help protect a business from being compromised by unprotected personal devices.
Malware scanning software can identify potentially dangerous malware programs in email attachments and block users from downloading them in the first place.
Root cause analysis
Cause
Cause
Cause
Cause
Cause
Impact analysis
Person
Impact
Six serving men
What?
What?
What not?
What not?
Why?
Why?
Why not?
Why not?
When?
When?
When not?
When not?
How?
How?
How not?
How not?
Where?
Where?
Where not?
Where not?
Who?
Who?
Who not?
Who not?
Analogies
What is it like?
Be the problem
Insight