af Matthew Le 1 år siden
97
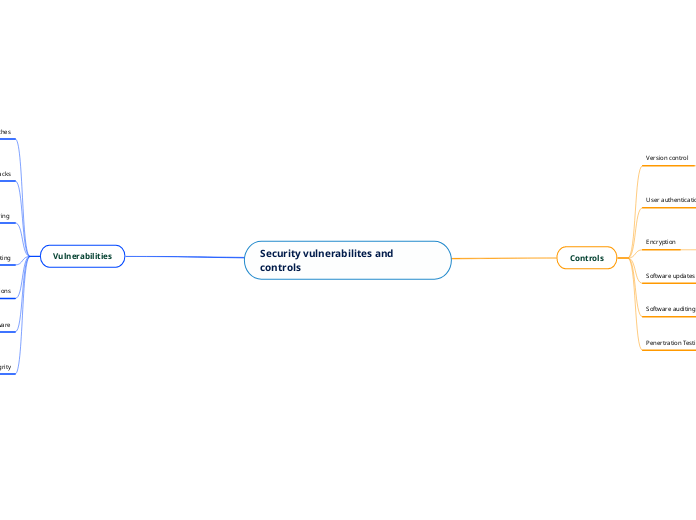
Security vulnerabilites and controls
Many security vulnerabilities threaten the integrity and confidentiality of data. Cross-site scripting allows hackers to inject code into user-input fields, granting unauthorized access.