von Gerson Varela Vor 1 Jahr
143
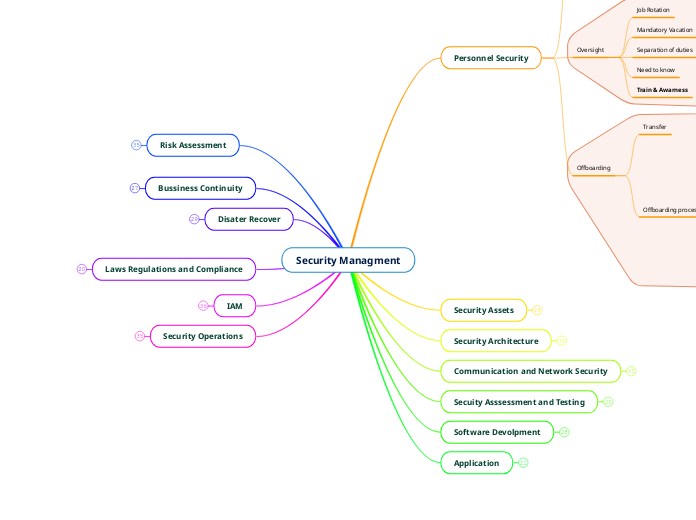
Security Managment
In the realm of organizational preparedness, several critical areas demand attention. Security management encompasses the safeguarding of assets through various models and principles, ensuring the confidentiality, integrity, and availability of data.