por dr inż. Michał Malinowski hace 5 meses
99
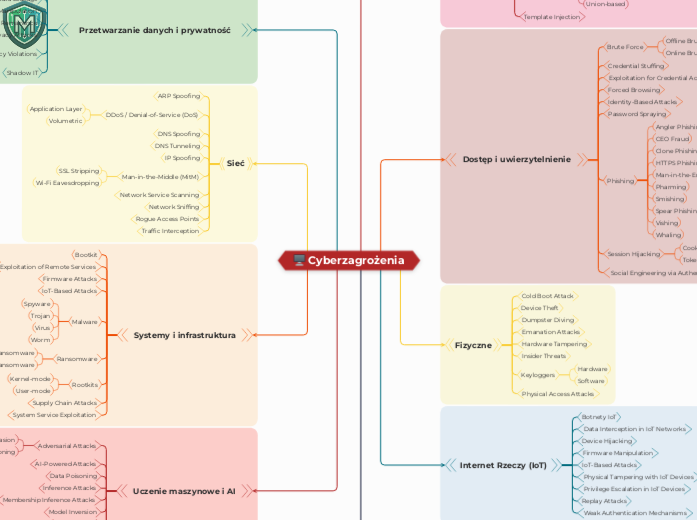
Cyberzagrożenia
The landscape of digital threats is vast and continually evolving, encompassing a wide array of attack vectors and vulnerabilities. Cybersecurity professionals must be vigilant against various forms of malware such as viruses, worms, spyware, and ransomware.