por FRINE PEÑA OLMEDO hace 1 año
257
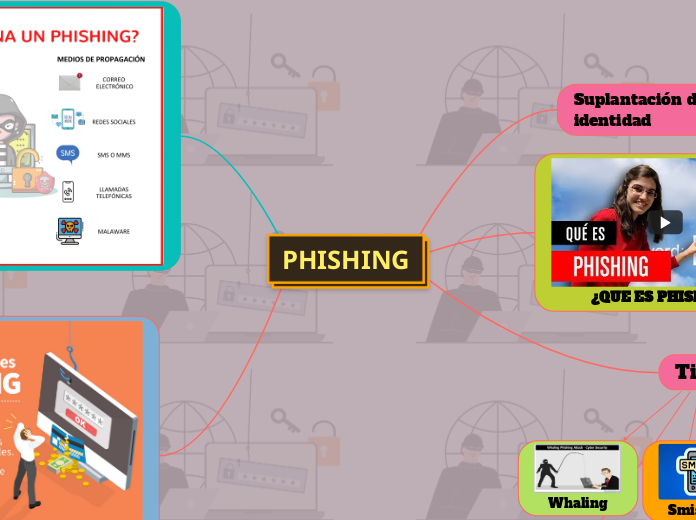
PHISHING
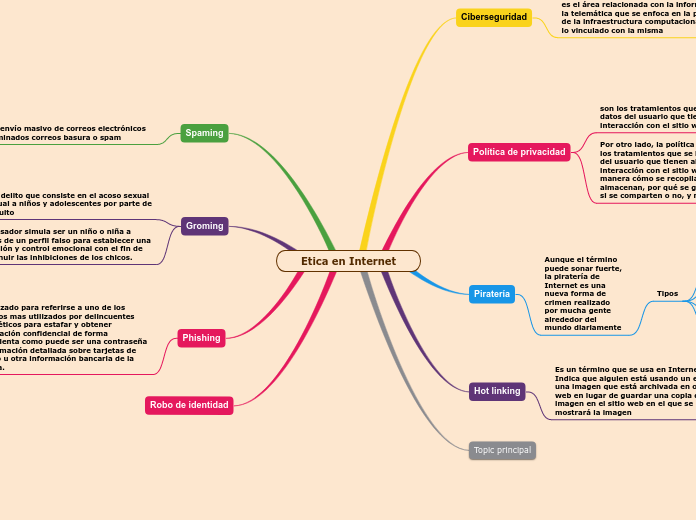
El phishing es una técnica utilizada por ciberdelincuentes para obtener información personal y confidencial de manera fraudulenta. Existen diferentes tipos de ataques de phishing, cada uno con sus propias características y métodos.