por miao charles hace 6 años
321
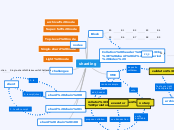
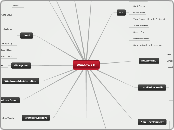
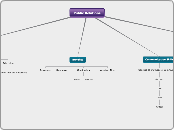
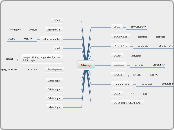
shard
A blockchain system focuses on improving security and scalability while maintaining decentralization. It employs a sharding mechanism, dividing the network into multiple shard chains to process transactions concurrently, thus enhancing efficiency.