jonka Richard Falcon 6 vuotta sitten
3249
CompTIA CySA+

jonka Richard Falcon 6 vuotta sitten
3249

Lisää tämän kaltaisia
Important Phase.
No technical work is performed.
Timing, Scope, and Authorization is gained during this phase.
NEVER conduct a Pen Test without authorization.
What is a Cyber Incident Response?
Actions taken in response to a security incident or event.
An organized apporach to understanding the incident, mitigating its negative effects, planning the recovery, and investigating the root cause.
NIST SP 800-61
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Forensics are used to determine any changes, activities, or actions that have occurred on a host/server/computer.
Allows incident responders to determine what occurred by putting together various pieces of information.
Similar techniques are used by incident response teams and law enforcement.
7 Step Process:
Determine what you want to find out.
Determine location to find the info.
Document your plan.
Acquire/preserve the evidence.
Perform initial analysis (log actions).
Conduct deeper analysis (log actions).
Report on your findings.
Eradication/Recovery
Remove any artifacts of the incident by removing the malware and any changes it made.
Restore the network back to full functionality.
Correct any security deficiencies.
Remove malicious code, sanitize compromised media, and fix any of the affected user accounts.
Recovery is NOT:
Rebuilding the entire network.
Fully redesigning of the system.
Not a reason to buy all new equipment.
Finishing the Response
Change Management Process:
Emergency Change Management Board may have authorized numerous actions during the incident response.
Follow-up to ensure all changes have been documented properly.
Need to ensure that network diagrams and vulnerability scan profiles are updated.
Lessons-Learned:
Document the details, the root cause, and the solution to a security incident.
Fact-finding meetings should be conducted as close to the end of an incident response as possible
Needed changes identified during the lessons-learned process should be fed into the resourcing and Change Mgmt process.
Final Report:
Every incident should finish with a compiled written report.
Establish organizational "memory".
Can serve as documentation in case further legal action occurs in the future.
Can identify other deficiencies in the incident response that need to be addressed by mgmt.
Final Report
Every incident should finish with a compiled written report.
Establish organizational "memory".
Can serve as documentation in case further legal action occurs in the future.
Can identify other deficiencies in the incident response that need to be addressed by mgmt.
Should Include:
Timeline of incident and response events
Root cause
Location and description of evidence
Actions taken to contain, eradicate, and recover
Estimated impact to organization
Post-recovery validation effort results
Documentation of lessons-learned
Lessons-Learned
Document the details, the root cause, and the solution to a security incident.
Fact-finding meetings should be conducted as close to the end of an incident response as possible
Needed changes identified during the lessons-learned process should be fed into the resourcing and Change Mgmt process.
Change Management Process
Emergency Change Management Board may have authorized numerous actions during the incident response.
Follow-up to ensure all changes have been documented properly.
Need to ensure that network diagrams and vulnerability scan profiles are updated.
Validation Effort
Only authorized user accounts exist on each system in the network.
Verify permissions assigned to each user.
Verify all systems are logging correctly.
Verify vulnerability scans on all systems are routinely conducted.
Sanitization and Disposal
Clear:
Logical techniques used to sanitize data (reset to factory state or overwriting a disk with all 0s).
Purge:
Physical or logical techniques to make data recovery from a disk infeasible using newest techniques (degaussing or or overwrite 0s 35x)
Destroy:
Date recovery infeasible and disk drive unusable for storage (melting, incinerating, destroying) PII, secret stuff
Patching
Patching any system that may be vulnerable to the same attack vector.
This is a good time to re-scan and patch ALL of your systems......
Reconstruct and Reimaging
Once an attacker touches your system, consider it compromised.
Reconstruct or reimage the system from a known good backup.
Consider the root cause of the incident so that the system isn't susceptible to the same attack vector.
ID Attacker
Do you need to ID the attacker?
Is there a good business reason why?
Attackers cover their tracks well, and indentifying them can take a lot of time and resources, where your goal is simply to minimize the business impact.
Law enforcement has a different viewpoint on this.
Unexpected Findings
What do you do when you find something you don not expect?
There is always a rick you will find what you did not want to find .......Employee breaking the AUP
.......Evidence of illegal activities
'''''''Removing malware and finding XXX
Order of Volitility
Date Collection Priorities:
CPU, Cache, Registers, Running Processes, and Memory
Network Traffic
HDD and USB drives
Backups, Printouts, Optical Media
Commercial and Open-Source for:
Imaging
Analysis
Hashing and Validation
Process and Memory Dumps
Password Cracking
Log Viewer
Log Viewer
Used to analyze log files from collected system images.
Can create timelines and allow you to visualize the data cleanly.
Password Cracking
Encrypted and password protected files require cracking or guessing.
Hacking tools like John the Ripper and Cain and Able can be used.
DOC, XLS, PPT, and ZIP files have other specialized password cracking tools:
Advanced Office Password Breaker
ElcomSofts Distributed Password Recovery
Zip2John
........numerous others.
Process and Memory Dumps
State of the OS and data in-resident memory at the time of collection.
Difficult to collect without changing the contents of the memory.
Useful to capture decryption keys for full disk encryption.
Hibernation files and crash dumps can also contain some of this data.
Linux:
fmem and LiME
Windows:
DumpIt
ALL: windows, linux, os x
Volatility Framework
EnCase
FTK
Memory dumps on system can be found at %SystemRoot%\MEMORY.DMP
Analyze dumps with Microsoft,s WinDbg
Hashing and Validation
Creates a unique file integrity check of a disk image after creation.
Used as part of Chain of Custody.
EnCase uses built-in hashing with its .EO1 format.
Should use both MD5 and SHA1/SHA256.
Analysis Software
Creates timeline of system changes.
Validates file against known good copy.
File system analysis for hidden files, changes, access, and metadata.
Windows Registry analysis.
Log file parsing and analysis.
Commercial:
FTK and EnCase
Open-Source:
SIFT, CAINE, and Autopsy
Imaging Media/Drives
Bit by bit copy of a drive, including the slack space and unalocated space.
FTK Imager -- Free to use--Proprietary
EnCase Imager -- Free to use--Proprietary
dd -- open-source -- free
FTK Imager
Commercial product that is free to use.
Documents chain of custody, adds hash, and creates metadata tags for later analysis.
GUI based
Open FTK
File-create disk image
select drive
where to save
type a file name and other info
where to store
dd
dd is a standard Linux/UNIX tool
Can clone drives using bit-by-it copy.
#dd bs=64k if=/dev/disk1/sda1 of=/mnt/usb1/sda1.img
connect usb through write blocker
fdisk -l
md5sum (filename)
Mobile devices have different operating systems and security issues.
Capturing data from mobile devices can be more difficult and needs special tools.
Tablets
Mobil phones
Mobil Forensic Software
Specialized software for accessing mobile devices.
Cables
Apple - Lightning cables or 30-pin
Android - USB, UCB-C, Micro USB, Mini,
SIM Card Access
Different phones require small screwdrivers or a push pin tool to access the SIM card.
Address book
contacts
call history
Contain a wide variety of software and hardware needed to conduct collection and analysis of data in the field.
Toolkits vary widely in cost and capability. $10-20k
Label Maker
Label cables, components, and other items collected while in the field.
Digital Camera
Used to photograph system layout, system configurations, drive labels, how a machine is cabled, etc.
Cables/Drive Adapters
Be ready to copy/collect any type of media you come across while in the field.
IDE
SATA
eSATA
Wipe Drives and Removable Media
Clean HDs that are ready to receive disk images on.
Drives are prepared using a drive wipe before use in the field.
Forensic Drive Duplicator
Designed to copy HD without changing the original. Bit-by-Bit copy.
Dedicated device that copies drive and hashes the disk image.
Creates images, hashes, and chain of custody metadata
Expensive
Dedicated device
Write Blocker
Ensures hard drives being imaged cannot be written to or its data changed. There are hardware (expensive) and software (not as forensicly sound) variants.
Ensures integrity of the captured disk.
Forensic Investigation Software
Capture and analyze forensic images.
Document and track investigations:
Forensic Toolkit (FTK) - Commercial Products
EnCase - Commercial Products
SANS Investigative Forensic Kit (SIFT) - Open-source
The Sleuth Kit (TSK) - Open-source
Digital Forensic Workstation
Conducts data capture and analysis.
Multicore CPU
Maximum RAM
Large, Fast Storage, SSD, RAID
Documentation is one of the most important steps in digital forensics.
Everything you do needs to be repeatable by third-party investigators.
Chain of Custody is imperative for use in law enforcement.
Much of your incident handling will involve network probes and attacks.
Network probes are usually part of reconnaissance efforts and are easy to detect......like a port scan.
Services and Applications should be monitored per good ITSM processes.
Are they up/down?
Are they responding properly?
Are they functioning properly?
Are they conducting transactions properly?
Are they logging properly?
Attacks to Service/Applications
Memory Overflows
Causes OS errors and crashes.
Monitoring for them is hard.
Detecting after a crash is easier.
Service Interuption
Simple issue or DDOS attack?
Monitoring tools can help determine reason.
Unexpected Outbound Communication
Why is the application sending out data?
Detect with network monitoring.
Unexpected Output
Improper output or garbage output.
User and admin training imperative to determining the root cause.
New Accounts
Were they authorized?
Do they have excessive permissions?
Anomalous Activity
Anything that does not match the typical behavior.
Investigate the activity and solve.
Behavior
Create and understand your baseline.
Log/alert on anything outside of baseline.
HIPS
Service Anomalies
Non-security issues:
Authentication errors.
Permission Issues.
Services do not start on boot up.
Service Failures.
Investigate the issues to ensure it is not security related.
Use antivirus, antimalware, file integrity checks, and whitelisting to verify.
Windows:
services.msc (GUI) or sc (command line)
Event Viewer to view application logs
Linux:
service-status-all (command line)
/var/log directory to view application logs
use tail to view the end of the log files.
Unauthorized Access, Changes, Privileges
Users and permissions are complex with the number systems in use.
Central Management tools (SIM/SIEM) can correlate logs for analysis.
Authentication Logs
User Creation Logs
Systems Logs
Application Logs
Security Event Logs
Malware and Unsupported Software
Use centralized management tools to conduct installs and inventory.
Antivirus and anti-malware tools.
Conduct blasklisting of unsupported software/files.
Application whitelisting - more effective than blacklisting.
System Monitoring
Processor (CPU), Memory, and Drives.
CPU attacks usually occur as DOS or malicious software.
Memory is monitored by the OS based on given thresholds:
Memory leaks occur when programs don't release memory after being terminated. Eventually, all memory can be used up. System restarts to release the memory.
Tools
System Monitoring Tools -
Windows:
Resource Monitor (RESMON):
Built-in Windows tool for monitoring.
CPU, Memory, Disk, and Network Utilization.
Performance Monitor (PERFMON):
Built-in Windows tool for monitoring. Supports collection from remote systems.
Linux:
ps - CPU and memory utilization, process info.
top - Like ps, but provides sorting by top usage.
df - Report of disk usage.
w - Accounts logged on, who ran process.
MAC Address Validation:
Ensure all devices are "Known Devices"
Check device MAC against vendor codes. First 6 digits of the MAC address is the vendor.
Scan the Network to ID devices.
Conduct physical site inspections.
Analyze traffic for irregular behavior.
Rogue Wireless Devices
Can be detected by conducting wireless surveys and mapping the area.
Often used as an Evil Twin to trick users and steal information.
Rogue Wired Devices
Usually occurs when an employee or attacker connects a wired device such as a hub/switch.
Prevention: Network Access Control and Port Security (802.1X).
Denial of Service (DOS)
Detection:
Attacks on a given network, system, or service from a single source.
Attempts to overwhelm system or network.
Prevention:
Block the attacker using your firewall or IPS.
Distributed Denial of Service (DDOS)
Attack on a given network, system, or service from simultaneous/multiple sources.
Detection:
Traffic coming from unknown botnet IPs
Monitoring your traffic and usage patterns.
Prevention:
Network designed with distributed network of endpoints...(like Akamai). https://www.akamai.com/
Ensure your networks can scale upwards.
Cybersecurity analysts should be able to determine an incident based on events.
Analysis of logs and other data are key to understanding if an event will become an incident.
Types of Network Events:
Beaconing
Unusual Bandwidth Consumption
Link Connection Failures
Unexpected Traffic
Unexpected Traffic.
Detected by IDS/IPS, traffic monitoring systems, or by manual observation.
Understand your baseline
Not all unexpected traffic is malicious, but it should be investigated/understood.
Could be unusual based on type of traffic, end point location, or amount.
Connections from other countries if you are a US company? not good
Detecting Unexpected Traffic
Protocol Analysis
Protocol Analysis
Seeks to detect protocols where they aren't expected, like VPNs or IPv6 tunnels.
Heuristics/Behavior-Based
Heuristics/Behavior-Based
Uses signatures and defined rules to detect.
Baseline/Anomaly-Based
Baseline or Anomaly-Based
Monitoring system alarm based on traffic that is outside the normal baseline.
Link Connection Failures
Generally occurs due to a hardware, firmware, or software issue.
Could be as simple as a bad module, broken cable, or unplugged connector.
Bad or malicious software.
DOS attack
Unusual Bandwidth Consumption.
Unusual bandwidth consumption could cause service issues or can be a sign of a larger issue.
Beaconing or a heartbeat sends a signal to a command and control system/sevver due to a botnet or malware infection.
Usually sent over HTTP (80) or HTTPS (443)
Can be difficult to detect.
Generally occurs at a certain frequency or pattern. Every 5 minutes for seconds.
Indication of malware.
Network event analysis is a common task for cybersecurity analysts.
Gather, correlate, and analyze data from different systems/sensors on the network.
Used to detect or prevent incidents.
Many network monitoring tools are available for different cases.
Combination of network data is more powerful than a single piece of data.
Different tools can analyze data in different ways.
Cacti
Cacti https://www.cacti.net/
Uses SNMP polling of network devices for status information and shows a GUI.
Nagios
Network and system log monitoring tool.
Provides GUI for system, services, and monitoring capabilities.
PRTG
Paessler Router Traffic Grapher. https://www.paessler.com/prtg
Server monitoring, network monitoring, and bandwidth monitoring.
Open-source Free
Packet Sniffing: Monitors packet headers to determine traffic type.
Flows: Collects information about connections.
SNMP: Network devices report about events through traps.
WMI: Windows Management Instrumentation. Management data of the OS using scripts or application access.
SolarWinds
Netflow Traffic Analyzer
Network Performance Monitor
Wireshark
Passive Monitoring and packet capture.
Used for packet analysis.
Uses a network tap to copy all traffic between two devices.
Useful for after-the-fact analysis.
Detailed information about:
Rate of traffic
Protocols used
Content
Request is sent to a remote system and data is collected from the end point to a centralized server.
Data contains information about:
Availability
Routes
Packet delays
Packet loss
Bandwidth
iPerf
iPerf
Measures maximum bandwidth of a given network.
Remote testing of a link.
Useful to determine a baseline of the network.
Ping
Ping
Data acquired by using ICMP on remote system.
Basic up and down information and latency only.
Provides data flow on the network and information on the status of the device.
Relies on capturing the data about the traffic passing through a router.
Called Network Flows.
NetFlow, slow, J-Flow: Depending on the manufacturer.
All are standardized for monitoring traffic flow.
Count information about the traffic at the interface.
Sample traffic (1:100, 1:1000, ect). Gives information a connection types, not the data itself.
RMON:
Operates at layers 1, 2, 3, 4 of the OSI model.
Operates as client/server model with probes.
Provides statistics, history, alarms, and events to a Management Information Base.
SNMPv3 (Simple Network Management Protocol): port 161
Collects information about routers/switches.
Information is about the devices themselves, not the traffic crossing through those devices.
All incidents should be classified by their threat and severity.
Allows comparison of current incident with past and future ones.
Aids in personnel's understanding of the incident being worked on.
10 classifying threats:
External or Removable Media
Attrition
Web
Impersonation
Improper Usage
Loss or Theft of Equipment
Unknown
Types Of Data
The type of date involved in the incident also affects the classification of severity.
Information Impact...
Degree of information compromised during the incident.
Information Impact
Degree of information compromised during the incident.
Government side only. NIST 800-61 Table 3-3 Do not need to memorize.
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Private Company not covered by NIST 800-61
None
Regulated Information Breach
Intellectual Property Breach
Confidential Proprietary Breach
Integrity Loss
Scope of Impact
Degree of impairment that an incident causes an organization and the effort to recover from the incident.
Functional Impact...
Degree of impairment to an organization.
Economic Impact...
Amount of financial loss to an organization.
Recoverability Impact...
Amount of time lost by an organization.
Recoverability Impact
Amount of time lost by an organization.
Do not need to memorize table
NIST 800-61 (Table 3-4)
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Economic Impact
Amount of financial loss to an organization.
Do not need to memorize table
NIST 800-61 (Table 3-2)
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Functional Impact.
Degree of impairment to an organization.
Do not need to memorize table
NIST 800-61 (Table 3-2)
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
10 classifying threats:
External or Removable Media
Attrition
Web
Impersonation
Improper Usage
Loss or Theft of Equipment
Unknown
Other
Attack that comes from a known origin, but doesn't fit into the other categories.
Unknown
Attack that comes from an unknown origin.
Loss or Theft of Equipment
Computing device or media is lost or stolen.
Improper Usage
Violation of organization's Acceptable Use Policy (P2P program).
Impersonation
Attack that replaces something benign with something malicious (spoofing, SQL injection, etc.)
Attack executed from email or attachment.
Web
Attack executed from web-based applications or site.
Attrition
Attack employing brute-force to compromise, deny, or degrade services, systems, or networks.
Advanced Persistent Threat (APT)
Not a category under NIST, but prevalent today.
Often funded by nation states, organized crime, or other sources.
Highly skilled and sophisticated attackers.
Often takes advantage of zero-day vulnerabilities.
External or Removable Media
Attack executed by removable media or peripheral.
Event - Any observable occurrence in a system or network.
Adverse Event - Any event that has negative consequences.
Incidents - An imminent threat of violation, or a violation itself, of a security policy, acceptable use policy, or standard security practice.
Not every event is an incident, however every incident contains at least one event.
During an incident, how will you communicate and share information?
When will you communicate with outside people like law enforcement, media, shareholders, and others?
Your incident response plan should state when.......
What information are you going to give them.
Press releases....statements.
Who?
Law Enforcement....
If incident involves criminal acts.
Information sharing partners......
Do you want to share indications of the incident?
Vendors....
Can provide patches and support during incident.
Other Organizations affected..........
Do you have evidence others were targeted?
Media or General Public.............
May be mandatory depending on type of incident.
Do you volunteer the information to the media?
How will the CSIRT communicate amongst themselves and to leadership?
How will management communicate to other employees?
Text
Phone
Meeting
Your incident response plan dictates how you will communicate during an incident.
Use an out-of-band communication method.
If voip is attacket do not use phones.
Printer
Foundation of the organization's Incident Response program.
Guides efforts at a high-level.
Provides authority for response efforts.
Approved by CEO or CIO.
Should be fairly timeless.
Detailed information.
Step-by-step guidelines.
Not a replacement for CSIRT's professional judgement and expertise.
Often developed as a specific playbook.
Playbook:
Describes a response to a high severity incident such as:
Data breach of financial information.
Data breach of PII.
Phishing attack against customers.
Web server defacement.
Loss of corporate laptop.
Intrusion into the corporate network.
Windows Golden Ticket reset.
Contents of the Policy
Statement of management commitment.
Purpose
Objective
Scope of policy
Definition terms.....What is a event....
Roles, responsibilities, and authority.
Incident prioritization scheme
Measures of performance for CSIRT
Reporting requirements
Contact information
Members are permanent or temporary.
Core team is cybersecurity professionals with incident response experience.
Temporary members brought in for specific cases (DBA or SQL Admin).
Smaller organizations have CSIRT as a collateral role in addition to their day job.
Testing the teams.
Plans without testing are ineffective.
You must ensure the teams are trained and ready for an incident response.
Testing allows a walk-through of the policy, procedures, and playbooks.
Can be combined with a penetration test to simulate a real attack.
What would trigger activation of CSIRT?
Who authorizes the activation?
Do they respond for all parts of the organization, or just specific ones? only ecommerce or internal network.
Can CSIRT talk to law enforcement?
Can CSIRT talk to the media? Generally CEO, CIO, CSO.
How would CSIRT escalate an issue?
Can you outsource the CSIRT?
Retaining a third-party gives you instant capability without daily resourcing.
Can be very expensive.
Ensure your organization is comfortable with the third-party's guaranteed response time.
Agree upon the scope of work to be performed. What does the organization have to do for themselves.
Who is on the CSIRT team?
Team of professionals responsible for handling a security incident within an organization by using a standardized procedure.
Leader is a skilled Incident Responder.
Subject matter expert. (Linux, Windows, DBA,)
IT support staff.
Legal counsel. (advisors)
Human resource staff.
Public relations and marketing staff.
What does management do?
Active role in an incident response.
Ensure the team has funding, resources, and expertise needed to conduct incident response.
Make critical business decisions.
Communicate with legal or news media.
Communicate with key stakeholders.
The process is not linear but cyclical. NIST SP 800-61 page 30.
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
Cyber incidents will happen.
No matter what your organization does to prevent a cyber incident...eventually one will happen.
How will you respond?
How will you react?
How will you recover?
Plan in advance.
Allows you to have a coordinated and methodical response.
Prior planning minimizes the damage and decreases your response time.
CSIRT isn't done once the incident is contained and eradicated, they still need to conduct:
Event Reconstruction
Lessons Learned
Evidence Retention
Evidence Retention
Large quantities of evidence have been collected.
What do we do with all the evidence?
The CSIRT must identify internal/external retention requirements.
If legal actions will be conducted, consult an attorney before deleting anything.
Timelines
US Government Agencies must retain all incident handling items for 3 years due to legal requirements.
Most organizations maintain records for 2 years, unless otherwise required by regulatory requirements.
HIPPA
FIRPA
SOX
Lessons Learned
Utilizes the timeline to aid improvement of procedures and tools used by CSIRT.
Group discussion to determine how the incident was handled, and how it could have been handled better.
Lessons learned must be fed into the ITSM processes in order to follow-on actions to be taken.
What happened and when?
How did staff perform?
Were procedures followed?
Were procedures adequate?
What should have been done differently?
Was information shared effectively?
How could we detect incidents sooner?
What new tools or resources does the organization need?
Event Reconstruction
Recreate a timeline of the incident.
Identify the root cause of the intrusion and/or incident.
Conduct consultations with system admins and management.
Focus on stopping the spread of the incident, remove it from the network, and recovering from it.
Phase focuses on active detection and removal of the incident.
5 Steps:
Pick containment strategy.
Use Strategy to Limit Damage Incident Causes
Gather evidence needed for potential future legal actions
Identify attacking system or attacker
Remove effects of the incident and recover normal business operations
Remove Effects of the Incident
Remove effects of the incident and recover normal business operations
Identify Attacking System/Attacker
Gather Evidence
Gather evidence needed for potential future legal actions.
Use Strategy to Limit Damage Incident Causes
Pick a Containment Strategy
Objective of Containment:
Limit the damage to the organization.
Provide incident handlers an opportunity to collect evidence and repair the issue.
Maintain and operate services for your customers.
Perform containment as quickly as possible.
Isolate the issue.
Stop the spread of the incident.
Containment Considerations:
Containment is not perfect. It's quick and dirty.
Can cause some loss of business functionality.
Coordinate with stockholders before you take actions.
Segmentation
Proactive strategy to prevent spread from one part of network to another.
Isolate or Removal
Remove a system from your network and directly connect to internet.
Remove the attacker (disconnect PC)
The Hardest to Standardize
Tools help in detection, but it takes a trained analyst to understand all the details during analysis.
When detection,occurs, analysts shift to validation mode, then into analysis.
Primarily passive activities designed to uncover and analyze incidents.
Best Practices for Analysis
Profile networks/systems.
Understand your baseline.
Create good logging policies/practices.
Conduct event correlation by synchronize network and system clocks.
Maintain organization knowledge base.
Capture network traffic ASAP in incident.
Filter information to reduce confusion.
Know when to bring in outside help.
Event Indicators
Publically Available Info
News, media, and other open-source information.
Ransomware out on the market ect.....
People
Suspicious activity reported by users or admins
Logs
From operating systems, services, applications, network devices, and network flows
Alerts
IDS/IPS, SEIM, Anti-virus, or other software alerts.
Takes preparation to build a well-prepared CSIRT.
Requires proper policy foundation within the organization.
Preparation includes building proper cyber defenses in the organization.
Includes indentifying/training personnel and building response kits.
Preparation Toolkits:
Digital forensic workstations
Forensic software
Packet capture devices
Spare servers/network gear
Backup devices
Blank removable media
Collection, analysis, and laptops
Portable printers
Office supplies
Evidence collection materials
and more
Gathering information to better understand the security landscape.
Some security standards and laws, such as PCI-DSS, require information gathering from inside and outside your network to ensure compliance through quarterly vulnerability scans.
Numerous tools and techniques for conducting discovery.
Successful reconnaissance does not always mean a successful attack, however we want to limit the damage that could occur as much as possible.
We utilize the same technique to limit both casual and directed reconnaissance.
Respond
Prevent
Control the information you release.
Blacklist systems that are abusing your services.
Use CAPTCHAs to prevent scripts and bot.
Utilize third-party registration for domains/IPs
Set rate limits for lookups and searches.
Avoid publishing zone files, if possible.
Educate your users about social media risks.
Monitoring
Utilize monitoring and alert systems based on signature, behavior, or anomaly.
Limit/Stop Probes/Scans
Utilize an IPS to limit or stop probes and scans.
Fingerprint your Network
Limit external exposure of services and know your forward facing footprint
Network Defences
Employ network defenses. HIPS, IDS, Firewall, ect.
Detect
Monitoring must occur at connection points between two network zones.
Often between Intranet and Intranet or Intranet and DMZ.
Perform data collection so you can analyze the data at a later time.
Data Sources:
Network traffic analysis using IDS, IPS, HIDS, NIDS, Firewalls, and other security devices. Can be done through the following:
Packet Analysis
Protocol Analysis
Traffic and Flow Analysis
Device ans System Logs
Port and Vulnerability Scans
Security Information and Event Management Logs
If you outsource your services, you might have to rely on your SaaS or PaaS provider to detect it for you.
Data Analysis
Manual Analysis
Human expertise is used to analyze the data.
Security Analyst
Heuristic/Behavioral Analysis
Detects threat behavior.
Useful to detect unknown threats.
Signature Analysis
Fingerprint or hash used to detect threats.
Helps to identify future problems based on past.
IE: Traffic congestion
Anomaly Analysis
What is different about this? What's not normal?
Your organization has an online profile, whether you know it or not.
This can be used by an attacker against you.
In a Pen Test, we act as the attacker, so we must use this information.
Social Engineering
Exploits the human element of security
Occurs via phone, email, social media, or in person.
https://www.social-engineer.org/
Metasploit
Phishing and other tools.
Creepy
Geolocation Tool
SET
Social Engineering Toolkit
https://www.social-engineer.org/framework/se-tools/computer-based/social-engineer-toolkit-set/
Document Harvesting
Where can you get these documents?
On the internet nothing is gone forever.
Th internet archive: https://archive.org/
Time travel service:
http://timetravel.mementoweb.org/
Social media
Paid public record searches;
Zaba search
NETR online
Emails
Can be used to perform contact chaining and conduct social engineering campaigns. phishing
Tools: Immersion.
Email Harvesting
The theharvester tool available in Kali-Linux is an e-mail accounts, username, and hostname/ subdomains gathering tool.
As an example, if you want to find e-mail addresses and hostnames for a target domain using Google, following is the appropriate command:
#./theHarvester.py -d targetdomain -l 100 -b google
 Figure: Email Harvesting
Figure: Email Harvesting
Email harvesting can be used by hackers to carry out a phishing campaign against an entire organization. This is one aspect of how emails can be misused. Computer users, who are often unaware of phishing attacks can fall victim and end up loosing confidential information to the hackers.
EXIF Data
Uses Geo location coordinates from photos.
Track patterns of life
Metadata
Contains authors name and software versions used.
IE: Word 2003
Organizational Data
Locations of facilities and buildings.
Work routine of the organization
Organizational charts. (Google)
Can be done using packet captures.
Requires an intruder to breach a company's network to gather information.
Treasure trove of information:
-What hosts are on the network.
-What OSs are running.
-What shares are available.
This is done using tools like Wireshark. https://www.wireshark.org/
INFORMATION AGGREGATION:
Gathering information from various platforms and tools for analysis with a single tool.
theHarvester:
-Gathers emails, domains, hostnames, employee names, open prots, banners, ect.
-Text-based tool installed in Kali Linux
Maltego: Great harvesting tool. https://www.paterva.com/web7/buy/maltego-clients/maltego-ce.php
Shodan: Search engine for IoT devices and vulnerabilities.
Creating a map of the network, systems, and other infrastructure of the company
Create using a mix of information gathering tools a manual research.
NIST SP 800-115 and Open Source Security Testing Methodology Manual (OSSTMM)
(OSSTMM) http://www.pen-tests.com/open-source-security-testing-methodology-manual-osstmm.html
Whois/Host Commands
Allows search of databases for domain and IP blocks.
Provides detailed registration information used when claiming the domain name.
Names, Addresses, IPs, Phone numbers, and more can be gained.
WHOIS Lookup Websites:
DNS Harvesting
Often our first step in information gathering.
DNS information is publicly available.
A quick Whois search can give you many details to use.
Host names can tell you about the server. (DC1.walmart.store120.com might be a domain controller.
NSLOOKUP
WHOIS Lookup Websites:
https://www.exploit-db.com/google-hacking-database/
DNS Brute Forcing
Used when you perform a DNS zone transfer.
Simply sends manual or scripted DNS queries for each IP of the organization.
Organizations can protect against this by sending responses slowly or with IDS/IPS rules to prevent this.
DNS ReconnaissanceWe can interact with a DNS server using various DNS clients such as host, nslookup, dig,etc.
nslookup is a computer program used in Windows and Unix to query Domain Name System(DNS) servers to find DNS details, including IP addresses of a particular computer, MX records for a domain and the NS servers of a domain. The name nslookup means “name server lookup”.
 Figure: Nslookup
Figure: Nslookup
The above image explains that we connected to local server and asked to resolve a record for us. The server responded with the IP address of the victim.
Before going ahead try to understand some DNS records. For more details please visit
https://en.wikipedia.org/wiki/List_of_DNS_record_types
– A – Points to host IP address
– MX – Points to domain mail server.
– NS- Points to host name server
– CNAME-Canonical naming allowing aliases to host.
– SOA- Indicate authority for domain.
– SRV-Service Record.
– PTR-Maps IP address to hostname.
– RP-Responsible Person.
– INFO- Host Information.
In order to retrieve mail server information we can use the following commands
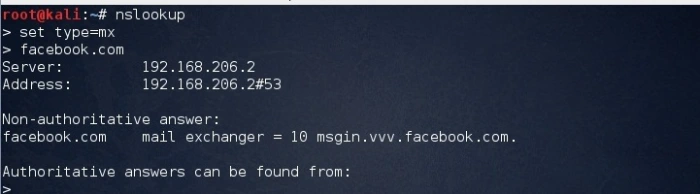 Figure: Nslookup query for mail server
Figure: Nslookup query for mail server
While gathering information can divided into 3 main techniques:-
1. Forward lookup bruteforce
The main idea behind this technique is to guess correct valid server names of organization. We can try this using the host command. The output gave us an IP address of the server.
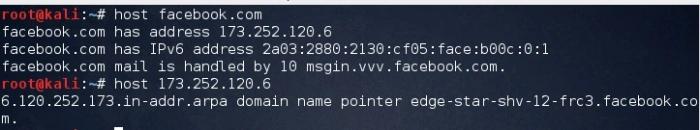 Figure: Forward lookup
Figure: Forward lookup
2. Reverse lookup bruteforce
This is a technique which is reverse to forward lookup bruteforce, in this case victim’s IP address is known and we need to find the server names and other information pertaining to the organization.
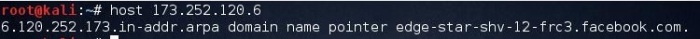 Figure: Reverse lookup
Figure: Reverse lookup
3. Verifying SPF Record
An SPF record is a TXT record that is part of a domain’s DNS zone file. The TXT record specifies a list of authorized host names/IP addresses that mail can originate from for a given domain name.
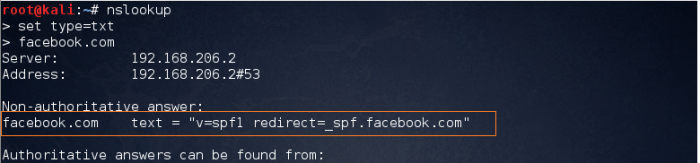 Figure: Verifying spf record
Figure: Verifying spf record
The purpose of an SPF record is to prevent spammers from sending messages with forged From addresses at your domain.
DNS Zone Transfers
Designed to replicate DNS Databases between two DNS servers
This is a vulnerability if some transfers are allowed, so most prevent zone transfers to servers that aren't trusted.
You can use dig to perform the transfer.
#dig axfr @dns-server domain.name
DigiNinja provides a couple DNS servers that allow zone transfers
Zone transfersDNS Zone Transfer is generally used for DNS database replications and backups. The security problem with DNS zone transfer is that it can be used to decipher the topology of a company’s network. Specifically when a user is trying to perform a zone transfer it sends a DNS query to list all DNS information like name servers, host names, MX and CNAME records, zone serial number, Time to live records etc. Due to the amount of information that can be obtained DNS zone transfer cannot be easily found in nowadays.
 Figure: Query for name server
Figure: Query for name server
The above image shows the how to get the dns server names.
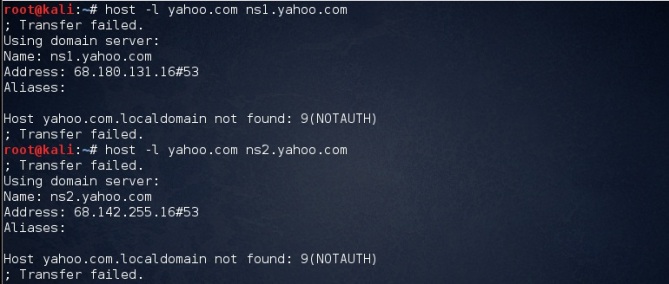 Figure: Zone Transfer Failed
Figure: Zone Transfer Failed
As the response to our query is been failed thus we can say that zone transfer is configured properly
nslookup
open a command prompt and type nslookup
see info
DNS Records
MX (Mail server records)
A (Address records)
C (cononical records)
PTR (Pointer records).
WHOIS Lookup Websites:
Traceroute
Traceroute
Traceroute is using UDP or ICMP ECHO to send out the packet with a Time To Live (TTL) of one, and incrementing it until reaching the target, the tcptraceroute is using TCP SYN to send out the packet to the target.
tcptraceroute will receive a SYN/ACK packet if the port is open, and it will receive a RST packet if the port is closed.
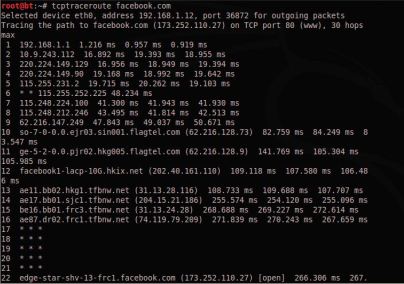 Figure:Traceroute
Figure:Traceroute
After route number 17, we are no longer able to get the route information. Usually this is because our traceroute is being blocked by a filtering device.
Domain Names/IP Ranges
Human readable names we use to locate servers.
Managed by registrars.
Generic top level domains: .com, .net, .org, .edu, .mil, .gov
Country code top-level domain: .com.uk, .edu.it
IP Ranges
There are 5 regional authorities;
AFRINIC (Africa)
ARIN (US,Canada, Antarctica, and Caribbean)
APRIN (Asia. Australia, New Zealand, ect.)
LACNIC - (Latin America, Carribean)
RIPE - (Europe, Russia, Middle East)
Each authority provides Whois services for their IP space.
Passive Reconnaissance
More difficult than active reconnaissance.
Relies on logs and other data.
Data you receive may be out of date.
Often used during a cyber incident response. You don't want to let an attacker know you are looking for them.
Host/Server Logs
System logs are collected by the system.
Useful for troubleshooting and reconstructing a cyber attack.
Log files provide information system configuration, applications, and user accounts.
You need system access to get these logs,
Application Logs- Logged by programs/applications
Security Logs- Records login events, resource usage, files created/open/deleted
Setup Logs- Records application setup actions./installs.
System Logs- Events from Windows components.
Forwarded Event Logs - Event subscriptions from remote computers.
Everything is going to be logged in the var/log directory. /var/log
Other applications may store their own log files elsewhere.
Firewall Logs
Indicates what is accepted and what is blocked.
Is a good way to passively understand your network design.
Reading configurations is quicker than reverse engineering the log files.
Often use log levels to categorize information and debug messages.
Cisco, Palo Alto and Check Point all log things a little different, but have common items. IE: date/time stamp, Details of the event.
Logs are designed to be human readable.
Access logs on Cisco using "show logging" command.
DHCP Logs
Dynamic Host Configuration Protocol
Provides an IP address, default gateway, subnet mask, and DNS server to a host.
DHCP server logs and configurations are useful during passive recon.
Combined with firewall logs, you can determine which hosts use dynamic or static IPs.
Netstat
Built-in Windows utility, Linux, MacOS, and Unix
Provides active TCP and UDP connections.
Identify process using a connection.
Provides statistics on sent/received date.
Route table information.
netstat -a active connections
netstat -o process using the connection
netstat -e ethernet stats - like netflow
netstat -r routing table information
netstat -ano
Netflow Data
Cisco specific protocol. Volume of data and how much is going out at a certain amount of time.
Captures IP traffic information for traffic monitoring to provide flow and volume(Not Packet Capture).
Contains IP, source port, destination port, and class of service.
Other vendors have "flows", like Juniper - Jflow and cflowd, Citrix - AppFlow, and HP -NetStream
NetFlow facilitates solutions to many common problems encountered by IT professionals.
• Analyze new applications and their network impact
Identify new application network loads such as VoIP or remote site additions.
• Reduction in peak WAN traffic
Use NetFlow statistics to measure WAN traffic improvement from application-policy changes; understand who is utilizing the network and the network top talkers.
• Troubleshooting and understanding network pain points
Diagnose slow network performance, bandwidth hogs and bandwidth utilization quickly with command line interface or reporting tools.
• Detection of unauthorized WAN traffic
Avoid costly upgrades by identifying the applications causing congestion.
• Security and anomaly detection
NetFlow can be used for anomaly detection and worm diagnosis along with applications such as Cisco
CS-Mars.
• Validation of QoS parameters
Confirm that appropriate bandwidth has been allocated to each Class of Service (CoS) and that no CoS is over- or under-subscribed.
How does NetFlow give you network information?
What is an IP Flow?
Each packet that is forwarded within a router or switch is examined for a set of IP packet attributes. These attributes are the IP packet identity or fingerprint of the packet and determine if the packet is unique or similar to other packets.
Traditionally, an IP Flow is based on a set of 5 and up to 7 IP packet attributes.
IP Packet attributes used by NetFlow:
• IP source address
• IP destination address
• Source port
• Destination port
• Layer 3 protocol type
• Class of Service
• Router or switch interface
All packets with the same source/destination IP address, source/destination ports, protocol interface and class of service are grouped into a flow and then packets and bytes are tallied. This methodology of fingerprinting or determining a flow is scalable because a large amount of network information is condensed into a database of NetFlow information called the NetFlow cache.
Configuration Files
Invaluable when mapping a network.
Identifies all routes and devices in detail.
Provides details of SNMP and SYSLOG servers on the network, user and admin accounts, and more.
Network Device Logs
Network devices log many activities, their status, and events.
Includes traffic patterns and utilization.
Log files, configuration files, and network flows are great for passive recon.
Cisco Logs
Level Name Example
0 Emergencies Failure causing a shutdown
1 Alerts Temperature exceeded
2 Critical Software failure
3 Errors Interface down
4 Warning Configuration change
5 Notifications Line Protocol up/down
6 Information ACL violation
7 Debugging Debugging Messages
Log and Configuration Files
Local system configuration data and log files can be used to build a network map.
Some tools exist to parse configuration files into a usable topology.
Much of this is done manually.
Active Reconnaissance
Utilizes host scanning tools to gather information about systems, services, and vulnerabilities in the network.
Does not include exploitation of the vulnerabilities, only identification of them.
Permission should be sought before conducting active reconnaissance because it could be mistaken as an attack.
Port Scanning
Most common method for information gathering on a network and devices.
Port scanners perform:
Host Discovery. What is online or off line
Port scanning and service.
Service version identification
Operating System Identification.
Port scanners also used for network inventory tasks and security audits.
Well known ports - (0 - 1023)
Registered ports - (1024 - 49151)
Where you scan from matters.
Internal scans will see more information than external scans.
If you are trying to simulate a cyber attack during a Pen Test, you should be scanning from outside the network to match the attackers perspective.
OS Scanning
OS fingerprinting uses TCP/IP stack responses from the TCP and UDP packets sent to identify Windows, Linux, or OSX, and if possible, the version.
Service Scanning
Service identification attempts to identify the service and its version through banner grabbing or comparing TCP/UDP packet responses to known signatures.
Scanning the subnet.
Network Mapping
Can approximate the network by using Time to live (TTL), Traceroute information, or other responses from the network.
Others
Metasploit has built-in scanners
Qualys Vulnerability Management
Tenable Nessus
or write your own using Python.
Nessus
Angry IP
Multiplatform
Graphical port scanner
Does not provide service or OS information by default.
Must use "fetchers" to get more information.
Well-known, but not as full featured as NMAP or Zenmap
Zenmp
Graphical version of NMAP
NMAP
nmap -O iptoscan ***OS scan
nmap -sV iptoscan *** Service Version. banner grabs and packet analasys
nmap -O -sV iptoscan
nmap -sS iptoscan **Syn scan
nmap -sT iptoscan ** Full 3way handshake
nmap -sA iptoscan ** Acknowledgment
NMAP cheat sheat: https://hackertarget.com/nmap-cheatsheet-a-quick-reference-guide/
Challanges
Firewalls and Layer 3 Switches. ACL's can make it difficult to map a network fully.
Wireless networks - Being able to determine what is wired or wireless.
Virtualized newtworks -
Cloud services -
Technique used to take a finished product and understand its inner workings through docomposition.
Conducted through Dynamic Analysis or Static Analysis
Static Analysis
Software or hardware.
Hardware
Difficult to perform due to embedded software in firmware.
Most often, dynamic analysis is conducted on hardware
Hardware should be purchased from a trusted supplier to minimize the risk of malware.
Software
Analysis of the code of the malware. Difficult and time consuming.
Readable - Ruby, Python
Not readable - C/C++ Java (Compiled)
Static Analysis of compiled code requires a decompiler or analysis in binary format.
Dynamic Analysis
Malware is placed in a Sandbox(Virtual) and its behavior is observed on the system and the virtual network.
Automated solutions can do this in near real-time, where email attachments are launched and automatically analyzed for malicious activity.
What becons, ports, services, ect. is it trying to talk to.
Sandbox
Beyond a Pen Test.
Security exercise where Pen Testers and Defenders are put against each other to provide additional training.
Performed in a simulated environment not the production network.
Conducted by three types of teams:
Red
Blue
White
White
Referee. Mediator.
Coordinates the exercise
Maintains the simulated environment and monitors the exercise.
Blue
Defender
Secures the network and attempts to keep the red team out through the use of security tools.
Usually made up of system and network admins.
Red
Attacker
Reconnaissance and exploitation
Similar to a Pen Tester
NIST SP 800-115 - https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-115.pdf page 5-2.
Simulate a cyber attack against a company using the same information, tools, and techniques available to an attacker.
Goal: to gain access to your systems and report the findings.
Performed by internal staff or external consultants.
Time consuming and costly.
Reporting
Detailed report after the test.
Contains results of the Pen Test.
Successful attacks and suggestions on how to fix them.
Things that could not be attacked.
Prioritize based on risk posed by vulnerability exploited.
Attack
Seek to bypass the security controls and gain access to the system.
Attack Phase (Exploitation):
Gain access
Escalating Privileges - Admin rights
System Browsing - May refer back to discovery phase.
Installing additional tools
Discovery
Testers conduct reconnaissance and gather as much information on the network, systems, users, and applications.
Examples:
Open source research
Port scanning
Enumeration
Vulnerabilities
Web application scanning
Securing Desktops, Laptops, Tablets, and Cell Phones.
DAC
Discretionary Access Control - Allows the owners of a file or resource to control the permissions of that resource.
MAC
Mandatory Access Control - Sets all security permissions centrally and the users cannot change permissions locally.
Great security, but is an administrative nightmare....only used in very sensitive environments.
Endpoint Security Software
Specialized software the enforces the company's security policies.
This software should report to a centralized management system for cyber security analysts to view and analyze.
Examples:
Host-based IDS/IPS
Antivirus
Group Policies (GPO)
Provides admins an efficient way of managing system and security configuration settings across many devices in a network.
Example:
Run scripts at login to verify compliance.
Require the use of a firewall on all hosts.
Mapping to a share drive on login.
If you can't implement a security control, you can compensate for it.
Provides a similar level of security by using an alternate means.
Examples:
Patch Management
Making sure patches are installed properly and as quickly as possible.
(SCCM) System Center Configuration Manager.
Hardening System Configurations
Make it as resistant to attacks as possible.
Disable unnecessary services.
Disable unnecessary ports.
Verifying secure configurations.
Centrally controlling device security settings. Only admins can change.
An attempt to lure an attacker to specific targets.
Honeypot
DNS Sinkholes
DNS Sinkhole
Provides false DNS information to malicious software.
A compromised system requests DNS information from the server, but the server detects the suspicious request and gives the IP address of the sinkhole instead of the Command and Control server.
Honeypot
Designed to falsely appear vulnerable and fool malicious attackers.
They simulate successful attacks and allow us to monitor attack techniques.
Designed to look like a lucrative target due to the types of services being run and vulnerabilities.
Limits network access to only authorized individuals or systems.
Ensures the systems connecting to the network meet basic security requirements.
NAC Approval Criteria
System Health Status
User Location
User Role
Time of Day
In-band/Out-of-Band
Not really covered on test but good to know.
Out-of-Band
Relies on existing network and has device communicate to authentication server (like 802.1x).
In-Band
Uses dedicated appliances placed between the devices they services they are requesting.
Example: Hotel networks that require you enter your name and room number before gaining access.
802.1x
The protocol most commonly used for network access control.
Works for wired and wireless connections.
RADIUS Server.
The typical authentication procedure consists of:
Sequence diagram of the 802.1X progression
Agentless
Agentless - NAC authentication is conducted in a web browser and does not need special software (such as wifi in a hotel).
Agent-Based
Agent-Based - Requires the device requesting access to have special software to communicate with the NAC service (Such as 802.1x).
Separates networks into different levels of security.
Much like Intranet, internet, and DMZ.
We apply this same principle to break apart our large networks into more secure enclaves.
Firewall
Most common network perimeter security.
Usually at network boundaries.
**Generally setup as triple-homed devices. Internet, DMZ, and Intranet.***
DMZ: Semi-trusted zone.
ACL - Access Control List - All traffic passing through the firewall is checked against the ACL
ACL contains rules to define what traffic can pass through the firewall.
Deny by default.
Common Ports. --- http://packetlife.net/media/library/23/common_ports.pdf ---
20,21 FTP
22 SSH
23 Telnet
25 SMTP
53 DNS
69 TFTP
80/443 HTTP/HTTPS
110 POP3
123 NTP
143 IMAP
161 SNMP
389 LDAP
443 HTTPS
1433 SQL Server
1521 Oracle
1720 H.323
1723 PPTP
3389 RDP
Web Application (WAF)
Protects against Web application attacks like SQL Injection and Cross-site Scripting. (SQL/XSS).
Placed in front of Web servers.
Next-Generation (NGFW)
Uses contextual information about users, apps and processes to make decisions.
Layer 7 firewall.
Statefull Inspection
Maintains information about the state of each connection.
In addition to IP and Port.
Packet Filtering
Checks each packet against rules (ACL) for IP and Port
Risk Assessments - Measure your current level of risk based on threats, vulnerabilities, and mitigations in place.
Should be conducted routinely.
(NIST) National Institute of Standards and Technology 800-30 page 32
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
Cyber Security professionals work to minimize risk through risk management and controls.
Controls
Physical
Locks, Fence, CCTV, Guards,
System, Devices, Software, and settings used to enforce CIA requirements.
Firewalls, IDS, IPS
Installing anti-virus and endpoint Security
Practices, policies, and procedures to increase security.
Security Awareness Training
Pen testing
Vulnerability Management
Utilize standard operating procedures
Risk Transference
If and organization cannot afford to accept, avoid, or mitigate the risk they can transfer the risk to another business.
Example: Insurance company
Data breach protection insurance.
Risk Mitigation
Minimize risk to an acceptable level.
Not necessarily to eliminate all risks.
By adding risk controls we can mitigate the risk down to an acceptable level.
Risk Avoidance
Risk is too high to accept.
So the system configuration or design is changed to avoid the risk or vulnerability.
Risk Acceptance
Common when the risk is low. Or controls are already in place.
Does not mean there is no risk.
Likelihood and Impact - Measurement of the risk that the combined threat and vulnerability imposed is based on the likelihood and impact.
Likelihood - The chance that the risk will be realized.
Impact - The severity of damage that occurs if the risk is realized.
Likelihood and Impact are Qualitative. low, medium or high.
Qualitative is subjective.
Quantitative is based on numbers or dollars. factual
Qualitative
Impact
Lilelihood
Quantitative
ALE
Annual Loss Expectancy - Quantitative is based on numbers or dollars.
ALE = Cost x Occurance
Let’s discuss the single loss expectancy (SLE). It contains information about the potential loss when a threat occurs (expressed in monetary values). It is calculated as follows: SLE = AV x EF, where EF is exposure factor. Exposure factor describes the loss that will happen to the asset as a result of the threat (expressed as percentage value). SLE is $30,000 in our example, when EF is estimated to be 0.3.
Let’s continue this case. Annualized rate of occurrence (ARO) is described as an estimated frequency of the threat occurring in one year. ARO is used to calculate ALE (annualized loss expectancy). ALE is calculated as follows: ALE = SLE x ARO. ALE is $15,000 ($30,000 x 0.5), when ARO is estimated to be 0.5 (once in two years).
Internal Factors
Our focus is to match vulnerabilities to the threats identified.
Remember if you have a threat without a vulnerability it is not a risk.
Environmental Threats
Occurs when natural or man-made disasters occur.
Fires
Flooding
Storms
Loss of power from city grid
Fiber cut
Structural Threats
Occurs when equipment, software, or environmental controls fail.
IT server fails due to hard drive failure.
HVAC fails in server farm.
OS bug or crash (software failure).
Accidental Threats
Occurs when someone makes a mistake that hurts the security of the system.
System Administrators take servers offline.
Adversarial Threats
Consider their capability, intent, and likelihood.
Trusted Insiders
Competitors
Suppliers
Customers
Business partners
Nation States
Risk - the probability (Likelihood) of the realization of a threat
Risk = Vulnerability + Threat
Vulnerability -Threat = No Risk
Threat - Any condition that can cause harm, loss, damage, or compromise an asset. External factors.
External Threats
Natural disaster
Cyber attack
Breach of integrity of data
Disclosure of confidential data
Malware
Cybersecurity professionals cannot control threats, however they can be mitigated.
Vulnerability - Weakness in the system design, implementation, software code, or lack of preventative mechanisms.
Vulnerabilities are internal factors.
Software bug
Misconfigured software or network device
Improper physical security
Cybersecurity Professionals control vulnerabilities.
Asset - Any item that has value in the organization.
People
Information
Equipment Network/Servers/Computers
Software
Processes
How much up time is the system providing?
Is the data accessible at all times by all users?
Best methods:
Redundancy in system design including components and data paths.
Backup strategies and disaster recovery plans.
Failure of Availability occurs when data cannot be accessed by the end user.
Integrity is about preserving the state of the system—we don’t want attackers to change our data.
How correct is the information?
Has the data been modified at retrieval, in transit or in storage?
Best methods to protect integrity are:
Hashing of files and information.
Checksum during data transmission.
Failure of integrity occurs when someone modifies the data being stored or on transit.
Confidentiality is about not disclosing sensitive information to other people.
How secure is the information?
How secure does it need to be?
Best methods to protect are:
Physical Security - Locks, Fence, Guards, Cameras, a Safe.
Electronic Security - Encryption (at rest and in transit), Passwords, Firewalls, 2FA
Failure of Confidentiality occurs when someone can obtain or view the data.
Centralized Identity and Access Management (IAM).
Systems built to create, store, and manage identity information including group memberships, roles, permissions and more.
What can IAM do?
Provision accounts
Authentication
Single-Sign-On (SSO)
LDAP Directory
Account Maintenance
Reporting
Monitoring
Logging
Auditing
LDAP
Logs and monitors a user when a authentication or authorization attempt is made or completed.
Individual is provided access to a given resource.
Individual proves who they are.
Foundation of good security architecture.
Does not rely on a single defensive measure or control for protection.
Not fulproof.
Architecture Review
Authentication and Authorization
Users
Largest cause of a security failure.
Data Validation and Trust
Single point of Failure
Spearphishing and Phishing
User Awareness Training
Users are the biggest threat to networks.
Proper security training is the most cost effective control that can be applied in an organization.
All the technical controls in the world won't stop a threat if a user lets the bad guys in.
Acceptable use policy
Outsourcing concerns
Proper vetting of the provider.
Employment practice
Access Control
Data ownership and control
Incident Response and notification process.
Incident Response and notification process
Who owns the data
Is it encrypted
Does the service provider have access to just the data, or do also have the encryption keys
Access Control
How is access control handled to the system
How is your data physically or logically segmented from other organizations that the service provider handles.
Proper Vetting and Employment Practices
What kind of background checks are you doing on the service provider, employees.
What internal personnel controls are used.
how do they handle employee issues.
Termination
Policies and procedures focuses on what to do when an employee is terminated.
Retrieving company property, disabling accounts, changing security codes, ect.
Mandatory Vacation
Allows us to identify any issues being hidden since the person will not maintain access to the systems.
Background Checks
Cross Training Employees
Succession Planning
Focuses on ensuring important duties will always have someone who can perform them.
Prevents issues from task not being performed during personnel turnover.
Dual Control
Process requires two individuals to perform the action together.
Separation of Duties
Separation of Duties - Requires more than one person to perform a task by breaking the task into additional parts. Provides a system of checks and balances to prevent fraud and abuse.
Integrating logs across the devices provides the most value and information.
You need to conduct data aggregation and correlation, trend analysis, and historic analysis.
Historical Analysis
Analyzes system, events, and devices over time to detect trends and patterns.
Helpful during incident responses as it looks back over a long period of time.
Trend Analysis
Analyzes system, events, and devices to detect trends and patterns.
Identifies issues that are outside of expected growth or usage patterns.
Looks forward based on past history.
Data Aggregation and Correlation
Combine data from multiple sources to identify events impacting different systems.
System logs
Authentication logs
Application logs
Event logs
and others
Detective control
Splunk
End-point security:
Servers, desktops, laptops, smartphones, are all considered hosts on your network.
Often the most at-risk part of the network since your users directly use them.
Common Security Controls:
Passwords and strong authentication
Encryption - File/Full Disk
Host Firewalls/Host-based IPS
Data Loss Prevention (DLP) software
Whitelisting/Blacklisting software
Anti-malware/Antivirus software
Patch management
Configuration Management
File Integrity Monitoring
Logging of events and issues
Logging/Monitoring/Validation
Logs must be securely stored and centrally monitored.
Specialized log server or (SIEM) Security Information and Event Management......Tripwire, AlienVault, Splunk
Configuration Management (Microsoft SCCM) allow you to validate system settings and software across the connected hosts.
Cryptography
Encrypting and hashing.
Encrypting files or the full disk can protect data at rest.
Proper storage of the encryption keys/passphrases is critical to security.
Hashing (file integrity check)files can be used to ensure file integrity, as well.
Combining the network architecture, configuration management, practices, and policies.
Can be accomplished through:
Network Segmentation
Firewalls
Outsourcing Network Segments
Outsourcing Network Segments
Remote services - SaaS and PaaS rely on providers for security and network designs.
Directly Connected Remote Network:
Acts as an extension of your intranet.
Utilizes LaaS with direct point-to-point VPNs.
To users, it appears the IaaS is just part of your network.
Low-level host protections at IaaS are still handled by the third-party service provider.
Firewalls
Multi-Firewall
Dual-firewall puts a firewall at each control point.
Allows for more stringent controls as you move deeper into the network.
Multiple Interface Firewalls
Different ACL and rule sets applied to each interface, creating multiple network segments.
Often called service-leg DMZ
Single Firewall/Router
Simplest network design utilized to create a DMZ for a lower trusted segment of the network.
Network Segmentation
Compartmentalization of the Network
Benefits:
Reduces the network's attack surface
Limits scope of regulatory compliance
Increases availability of critical services
Increases network efficiency
Implemented through:
Firewalls
Routers
Switches
VLAN's
Controls prevent, detect, counteract, or limit certain security risks.
Technical
Administrative
Physical
Preventative
Detective
Corrective
Compensating
Compensating Controls
Designed to satisfy a security requirement not being met by other controls.
Minimizes threat down to an acceptable level of risk.
Blocking certain ports instead of upgrading all the OSs
Segmenting vulnerable software to a separate part of the network.
Corrective Controls
Designed to fix an issue after an incident has occurred.
Part of Incident Response Process.
Reactive measures.
Patches
System rebuilding
Restore from backups
Detective Controls
Designed to detect when an incident occurs, capture details about it, and send an alert/alarm so someone can act.
Intrusion Detection Systems
Security Cameras
Logs
Preventative Controls
Designed to stop an incident before it happens.
Proactive Measures
Firewalls - Preventative and Technical
Antivirus
Training
Security Guards - Preventative and Physical
Designed to provide security by preventing physical access or harm to the organization's systems or facilities.
Fences
Mantraps
Security Guards
Fire Suppression Systems
Also called Procedural Controls
Designed to provide security through processes and procedures.
Legal controls are a type of these controls that are put in place by the law.
Incident Response Plans
User Awareness Training
Account Creation Policy
Acceptable Use Policy
Technical Controls
Designed to provide security through technical measures.
Firewalls
IDS/IPS
Authentication Systems
Network Segmentation
Data - Encryption
Application - Patches
Endpoint Security - Antivirus/Malware protection
Network - IDS/IPS
Perimeter - Firewalls
Difficult to design and implement, but it is important.
Must consider business needs and usability in the design of layered controls.
Four Design Models:
Uniform Protection -
Protected Enclaves -
Risk or Threat Analysis-Based -
Information Classification-Based
Information Classification-Based
Maps data protection to different classes of information.
Higher classification levels get additional attention and security controls.
Niper and Siper
Risk or Threat Analysis-Based
Addresses specific risks or threats in the design of the networks and systems.
Example:
If you are concerned with phishing as a threat vector, you could employ additional controls to securely scan and filter your incoming emails.
Protective Enclaves
Enclaves that house more sensitive data are given additional protection.
Network is segmented and firewalls are placed between your most critical/sensitive assets.
Uniform Protection
Gives same level of protection to all data, systems, or networks.
Can be expensive for large networks. Focus is everything and everywhere.
Standard Frameworks:
Creating your own cybersecurity framework is a daunting task.
Standard frameworks exit to help provide a standard approach.
Sherwood Applied Business Security Architecture (SABSA).
Alternative model for security architecture that maps to architectural layers from different perspectives.
Used in Enterprise Architecture
The Open Group Architecture Framework (TOGAF)
Widely adopted approach to Enterprise Architecture.
Four Domains: Business Architecture:
Application Architecture:
Data Architecture:
Technical Architecture:
Control Objective for Information and Related Technologies (COBIT).
Set of best practices for IT governance developed by ISACA.
Divides IT activities into four domains:
Plan and Organize
Acquire and Implement
Deliver and Support
Monitor and Evaluate
Information Technology Infrastructure Library (ITIL)
Comprehensive approach to ITSM
Used to be the most commonly used information security standard.
Declining in usage outside of regulated regulated companies that require ISO compliance.
To become ISO 27001 certified, an external accesor validates organizational compliance.
Designed to meet 1 or more of the 5 objectives.
Specificly modeled for Cybersecurity.
Framework Core is a set of five security functions that apply to all industries.
Framework Implementation tiers measure how the organization is positioned to meet cybersecurity objectives.
Framework Profiles describe how the organization might approach the functions covered by Framework Core.
The US has various laws and regulations that must be adhered to, based on your industry (CySA+ focus).
Data Breach Notifications
Various State Laws.
Requires companies to notify victims of data breaches in a timely manner.
Payment Card Industry Data Security Standard (PCI-DSS)
Rules about storage, processing, and transmission of credit/debit card info.
Not a law, but a contractual obligation.
Family Education Rights and Privacy Act (FERPA)
Requires educational institutions to implement security and privacy controls for educational records.
SOX
Sarbanes-Oxley (SOX) Act
Requires publicly traded companies to maintain good security around their IT systems storing and processing their financial records.
Gramm-Leach-Bliley Act (GLBA)
Requires financial institutions to have formal security programs in place.
Must designate a "responsible" individual.
HIPAA
Health Insurance Portability and Accountability Act (HIPAA)
Security and privacy rules for healthcare.
Affects healthcare providers, insurers, and others storing health information.
Evaluation of your cybersecurity program is essential to it being effectively run.
Evaluation occurs as audits and assessments.
You get what you inspect, not what you expect.
Assessments
Much less formal than a audit.
Usually requested by the organization itself for process improvement purposes.
Information gathered through interviews with employees (which is considered the truth) instead of independent verification.
Audits
Formal review of organizational cybersecurity program. Usually done internally.
Or it can be for a specific compliance requirement (externally) like PCI-DSS.
Rigorous, formal testing of controls resulting in formal declaration by the auditor of compliance.
Policies provide the control objectives the organization wants to achieve.
This is the desired end state, not the method to accomplish them.
Security controls are used to achieve the control objectives.
Physical Controls
Logical Controls
Administrative Controls
Combining Control Objectives
Physical, logical, and administrative controls are most effective when they are combined.
To prevent theft of data from a server:
Physical controls for building access
Logical controls like encrypting the HD
Administrative controls like requiring two people to open lock/door
Administrative Controls
Procedural controls to implement good cybersecurity practices.
Policies and procedures.
Separation of duties
Background checks
Reviewing log files
Logical/Technical Controls
Technical controls to enforce (CIA) confidentiality, integrity, and availability. Even Non-repudiation
ACL's in a firewall or router
Encryption schemes.
Physical Controls
Controls that impact the physical world.
Cameras
Fences
Gates
Locks
Lighting
Alarm System
Fire Suppression Systems
Information Security Policy Framework:
Policies
Standards
Procedures
Guidelines
Policies, Standards, and Procedures should be followed.
Your information security framework should include the method for granting any necessary "exceptions".
Exceptions:
Specific approval to deviate from a policy, standard, procedure.
Approval authority is specified in policy.
Exception request includes:
Policy, standard, procedure requiring exception.
Reason for exception
Scope and duration of exception
Description of compensating controls to lower risk
Guidelines
Not required actions, just recommendations.
Flexible in nature to allow for exceptions and allowances during a unique situation.
Example:
The organization may create a guideline showing users how to store data files in a cloud service and how to encrypt the files.
These aren't required, but may be useful to the end user and can be changed quickly.
Procedures
Detailed step-by-step instructions created for people to perform an action.
Actionable steps to create a consistent method for achieving a security objective.
Example:
The service desk has a procedure for how to create a new user's account.
Encompass all the security related policies, standards, and guidelines for action by your front-line employees.
Standards
Used to implement a policy.
Includes mandatory actions, steps, or rules needed to achieve cybersecurity.
Approved by a lower level than C-suite, such as Director of Information Systems or mid-level manager.
Standards can also exist in industry frameworks (COBIT, ITIL, etc.)
Policies
High-level statements of intent. Must be followed. Management Intent.
Contain broad statements about cybersecurity objectives in the company.
Framework to meet the business goals and to define roles, responsibilities, and terms used in other security documents.
Who approves the policies?
Usually the C-suite will approve the policy for the organization.
Without management buy-in, the policy is a waste of your time and effort.
Top-down approach is most effective
Account Management
Data Retention
Data Classification
Data Ownership
Password
Acceptable Use
Information Security
Identification, prioritization, and remediation of vulnerabilities before a threat can exploit them.
An organized approach to scanning and continuous assessment of your organizational security posture.
Scanners do a great job of automating the identification of vulnerabilities.
However, a trained analyst is required to understand the implications of those vulnerabilities to:
Eliminate false positives.
Find root causes.
Prioritize remediation actions.
Vulnerability scanners can detect 10000's of different types of vulnerabilities.
Internet of Things (IoT) Vulnerabilities
ICS
(ICS) Industrial Control Systems - Pumps, valves.
SCADA
(SCADA) Supervisory Control and Data Acquisition Systems.
Power plants and factories. Monitoring sensors.
Not often patched or upgrades.
Should be separated and off the network.
Smart TV's/Consumer Devices
Big threat inside your network at the office and at home.
Smart home.
Not often patched or updated.
Shodan Tool
Webb Application Vulnerabilities
Injection Attacks
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Nessus and Qualysguard can scan for Web vulnerabilities, but they are not specialized (like Nikto).
https://www.owasp.org/index.php/Category:Attack
Cross-Site Request Forgery (CSRF)
Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated.
Attacker cannot see web server's response, but this attack can be used to have victim transfer funds, change their password, ect.
https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) attacks are a type of injection, in which malicious scripts are injected into otherwise benign and trusted websites. XSS attacks occur when an attacker uses a web application to send malicious code, generally in the form of a browser side script, to a different end user. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it.
Attacker embeds scripting commands on a website that is executed by a regular user without knowing it.
Victim in this case is the regular user, not the server.
If one of these are discovered during a scan, you need to work with the developer to fix the code and setup proper controls to prevent it in the future.
https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
Injection Attacks
Most common is SQL injection.
Allows an attacker to send commands through a web server to a back-end system, bypassing the normal security controls.
Prevent this through input validation and using least privilege for the database.
Injection flaws, particularly SQL injection, are unfortunately very common in web applications. There are many types of injections:
SQL,
Hibernate Query Language (HQL),
LDAP,
XSLT,
XML,
and many more.
Virtual Vulnerabilities
VM Escape
Management Interface Access
Virtual Host Patching
Virtual Guest Issues
Virtual Network Issues
Virtual Network Issues
Virtual firewalls, routers, and switches all need to be considered as part of your scanning program.
If embedded as part of your VM solution, ensure appropriate patching is being done to prevent attacks.
Virtual Guest Issues
Each Guest represents another server on the network, and they all need patching.
Ensure your remediation and patch management considers all your VMs.
Ensure your vulnerability management program also scans Guest VMs.
Virtual Host Patching
Just like other servers, Virtual hosts need patching of the OS and software.
This can help prevent VM Escape.
Management Interface Access
This interface controls access to all the virtual machines and can configure them.
Should be highly secured, including use of two-factor authentication.
VM Escape
The most serious issue of all virtualization issues.
Occurs when an attacker can break out of the virtual machine (guest) and reach the host (hypervisor).
In May 2017, a hacking contestant stitched together 3 different exploits and managed to perform a VM escape.
Network Vulnerabilities
Missing Firmware Updates
SSL and TSL Issues
Domain Name Service (DNS) Issues
Internal IP Disclosure
Virtual Private Network (VPN) Issues
Virtual Private Network (VPN) Issues
VPN's consist of application protocols ans SSL/TSL encrypted tunnels.
Configuration issues and missing firmware patches an also affect VPN's.
Internal IP Disclosure
Networks that use NAT attempt to hide their internal IP structure.
Information could be leaked in headers if a server isn't configured properly.
Domain Name Service (DNS) Issues
DNS servers are victims of reconnaissance and other attacks.
SSL and TSL Issues
Secure Socket Layer (SSL) and Transport Layer Security (TSL) are designed to secure information sent over the internet (such as HTTPS).
SSL is insecure and should not be used.
Admins should disable support for older versions. (SSL and TSL before v1.2)
Insecure Cipher Use:
SSL/TSL are only the protocol used, not the cipher.
Cipher is the encryption algorithm. Do not use RC4
Certificate Problems:
Certificates identity servers and exchange the encryption keys.
Missing Firmware Updates
Network devices rely on firmware for their operating systems.
Firmware needs patching and upgrades.
Server and Host Vulnerabilities
Missing patches
Unsupported Software or Apps
Buffer Overflows
Privilege Escalation
Arbitrary Code Execution
Insecure Protocol Use
Debugging Modes
Debugging Modes
Debugging modes give lots of information to developers, but should be disabled prior to server and code deployment.
Debugging information could give attackers a lot of information during a reconnaissance.
Insecure Protocol Use
When using older protocols not designed with security in mind.
Example: FTP, Telnet, SMBv1, SSL, .........
Arbitrary Code Execution
Allows an attacker to run software on a targeted victim machine.
Remote code execution is worse, because it allows it to occur over the network.
Privilege Escalation
Occurs when an attacker upgrades their level of access to an admin or root user.
For example, CVE-2016-7255 is an example in Windows Vista, 2008, 7, 8.1, 10, and 2016 machines.
Kernel-mode drivers are exploitable to allow local users to become an admin.
Buffer OverflowsBuffer Overflows
Occurs when the attacker manipulates a program to place more data into memory than it is allocated for causing overflow.
Another specific type is integer overflow.
These vulnerabilities tend to exist for a long time, but are corrected by a patch.
In 2015, over 85% of the data breaches were caused by buffer overflow attacks.
Unsupported Software/Apps
Software vendors do not support software forever, they have an "end of life" date.
After the "end of life" date, no more patches are released for the software.
Missing Patches
One of the most common issues found. One of the easiest to fix.
Missing patches.
Comes from improper patch management.
CVSS scores are helpful, but they alone don't tell you how a vulnerability affects your systems.
Conduct Trend Analysis
Conduct Trend Analysis - Trend analysis also allows the analyst to ensure the vulnerability management program is working effectively.
Compare Results
Compare results with other information sources
Logs from servers, network devices, applications, and other devices.
Configuration management systems.
Security information and event monitoring (SIEM).
Informational Results
Not everything reported by the scanner is considered a vulnerability.
Some are reported as "informational".
Typical "informational" items are configurations that would allow an attacker to perform reconnaissance.
Documented Exceptions
Vulnerabilities that are known, but will not be fixed by the organization.
Vulnerabilities that are on the system but are to expensive to fix.
Once the risk is accepted by management, they should be documented in the scanner to prevent future reporting of them.
False Positives
Scans can often report a vulnerability exists even if it does not.
How often this occurs is known as the false positive error rate.
Vulnerabilities can be validated and verified:
Check if a patch is missing.
Attempt to exploit erroneous code.
Verify the system configuration.
Common Vulnerability Scoring Systems (CVSS)
Industry standard for identifying the severity of a vulnerability.
Analysts use this score to help prioritize remediation efforts
Measured in six categories:
Three for the exploitability
Three for the impact
There are two versions of CVSS
SySA focuses on CVSS not CVSS 3.0
CVSS 3.0 adds two additional measures:
User Interaction (exploitable metric)
Scope (both exploitable and impact metric)
SEE CVSS score breakdown here:
https://nvd.nist.gov/vuln-metrics/cvss/v2-calculator
or
https://en.wikipedia.org/wiki/Common_Vulnerability_Scoring_System
CVSS Base Score Chart
Severity Base Score Range Severity Base Score Range
None 0.0
Low 0.0-3.9
Medium 4.0-6.9
High 7.0-10.0
CVSS Temporal Score
The Temporal score changes over the lifetime of the vulnerability.
As exploits are developed, disclosed, and mitigations made available, the score changes.
Not covered by the CySA exam
Temporal Score = Base score x Exploitability x Remediation Level x Report Confidence.
Report Confidence
Report Confidence (RC) Metric - Used to show the level of confidence in the existence of the vulnerability and the technical details of the report.
Remediation Level
Remediation Level (RL) Metric - Used to decrease temporal score as mitigations and fixes are made available.
Exploitability
Exploitability (E) Metric - Current state of exploitation techniques or automated exploitation available.
Unproven
Proof-of-Concept
Functional
High
Not Defined
CVSS Base Score
SEE CVSS score breakdown here:
https://nvd.nist.gov/vuln-metrics/cvss/v2-calculator
or
https://en.wikipedia.org/wiki/Common_Vulnerability_Scoring_System
CVSS Base Score Chart
Severity Base Score Range Severity Base Score Range
None 0.0
Low 0.0-3.9
Medium 4.0-6.9
High 7.0-10.0
Availability
Availability (A) Metric - Describes the impact to availability of the system.
None - No impact to availability of the system.
Partial - Reduced performance or loss of functionality.
Complete - Total loss of availability.
Integrity
Integrity (I) Metric - Describes the impact to integrity of data processed by the system.
None - No impact to integrity of the system.
Partial - Modification of some information possible.
Complete - Total loss of integrity.
Confidentiality
Confidentiality (C) Metric - Describes the impact to confidentiality of data processed by the system.
None - No impact to confidentiality.
Partial - Considerable disclosure of information.
Complete - Total disclosure of information.
Authentication Metric
Authentication (Au) Metric - Describes the number of times an attacker would have to authenticate.
Multiple - Requires two or more authentications.
Single - Requires one authentication.
None - No authentication required.
Access Complexity
Access Complexity (AC) Metric - Describes the difficulty an attacker would have to exploit the vulnerability.
High - Requires difficulty/specialized conditions.
Medium - Requires "somewhat specialized" conditions.
Low - No Specialized conditions required.
AV Metric
Access Vector (AV) Metric - Describes the method an attacker would use to exploit the vulnerability.
Three Categories:
Local - physical access or logical access to the system
Adjacent Network - Access to LAN for affected system
Network - Remote Access from WAN
Look at the Synopsis (Remote windows execution) and Description (much more detail).
See Also (For greater detail)
Solution
Risk Factor and CVSS(2.0 not 3.0) Score
References
Exploitable, Plugin, and Hosts
See Nessus sample reports here -
https://www.tenable.com/products/nessus/sample-reports
Detection
Remediation
Testing
or
Continuous Monitoring =
Provides for on-going scanning of the network.
Checks for vulnerabilities as often as possible based on resources available.
Provides earlier detection of vulnerabilities.
Automation
Many products include built-in workflows and automation to track vulnerabilities through the cycle.
Can automatically close out vulnerabilities when testing shows they are resolved.
Some tools can be integrated into your IT Service Management system.
Implementing and testing a solution.
Vulnerability Analysts do not implement the fixes
Their role is to find the issues and pass them to the system administrators to fix
Fixes may not be quick, often they require approval from the Change Control Board,
Fixes should be tested in a lab environment prior to rolling it out to the enterprise.
IT Governance
Can create hurdles in getting approval to implement changes.
Fixes can risk disrupting business functions.
Overcoming Objections:
Work within the organization policies when possible to get resources and support.
Utilize the Emergency Change Control board when critical fixes must be implemented quickly.
Promise to Customers
MOUs and SLAs have specific up-time, performance, and other requirements that the organization must meet.
Scans can risk disrupting business functions.
Overcoming Objections:
Ensure the cybersecurity team is involved in the drafting of the MOAs and SLAs.
Discuss appropriate times and scope for scans.
Service Degredation
Vulnerability scanning places a resource tax upon the network and its servers when scans are conducted.
Scans can risk disrupting business functions.
Overcoming objections:
Consider different scanning times (non-peak hours).
Change scanning settings to lower intensity modes.
Coordinate Efforts
Coordinate your efforts.
Vulnerability Analysts view fixes as the highest priority.
Not everyone in the organization does.
You need to coordinate with others to get these vulnerabilities remediated.
Service degradation, promises to customers, and IT governance can slow down your efforts.
Remediation Priority.
Man-hours, money, equipment, and other items are a limited resource.
Vulnerability management is all about prioritization of organizational efforts.
You can't fix everything right away.
How Exposed
How exposed is the server to the vulnerability?
External facing servers are more exposed than intranet servers.
Often, you should fix a lower external vulnerability before a higher internal one.
How Severe
How severe is the vulnerability?
Each vulnerability is given a criticality value in the Common Vulnerability Scoring System (CVSS).
Different vulnerabilities are more severe than others.
Example:
Known-exploit against a software bug that allows remote-code execution is very severe.
Cross-site scripting vulnerabilities might be less severe if its on an intranet server only.
How Difficult
How difficult is it to fix the vulnerability?
How much time and money will it cost to fix?
Example:
I can spend all my time and money fixing the vulnerability #1, or I can fix vulnerabilities, 2, 3, 4, and 5.
How Critical
How critical is the system and information it contains?
Take into account confidentiality, integrity, and availability if the vulnerability was exploited.
Example:
If an attacker was able to breach your customer database and get all their information. How bad is this?
Vulnerability Reporting.
Vulnerability analysts need to communicate the issues found to the system administrators.
Scanners provide detailed reporting that can be automated to alert system administrators at periodic intervals.
Critical vulnerabilities found can be sent out of cycle because they are soo critical.
Dashboards. Managers love dashboards because it provides a high-level summary of issues.
Overview of Hosts. Shows which hosts are most vulnerable.
Criticality - Shows which vulnerabilities are most critical.
Criticality
Criticality - Shows which vulnerabilities are most critical.
Overview Of Hosts
Overview of Hosts. Shows which hosts are most vulnerable.
Dashboards
Dashboards. Managers love dashboards because it provides a high-level summary of issues.
Vulnerability management used to be performed by numerous types of software with no common protocol
Security Content Automation Protocol (SCAP) led by NIST standardized vulnerability management between different software.
Ensures standardization.
NIST SP 800-117 Guide to adopting and using SCAP
https://csrc.nist.gov/publications/detail/sp/800-117/final
OVAL
Open Vulnerability and Assessment Language - Language for low-level testing procedures used by the checklists.
XCCDF
Extensible Configuration Checklist Description Format - Language for checklists and reporting results.
CVSS
Common Vulnerability Scoring System - Standard approach for severity of software flaws.
IMPORTANT
CVE
Common Vulnerabilities and Exposures - Standard names for security-related software flaws.
IMPORTANT
Important
CPE
Common platform Enumeration - Standard names for product names and versions.
CCE
Common configuration Enumeration - Standard names for system configuration issues.
Scheduling Automated scans.
Producing reports.
Providing authenticated access for scans.
Choosing plugins and scan agents.
Conducting scans from different perspectives. (Internal, External)
Vulnerability management tools are vulnerable also.
You should always update the tools and its plug-ins/signatures before use.
This can be automated, as well, but check to verify the update has occurred before use.
Patching
Implements bug fix
Feature enhancements
Improves scan quality.
Update plug-ins daily
Small software agents installed on your server or clients.
Provides an inside-out perspective of vulnerabilities on the server or client.
Agent-based approaches require more resources on the server and often system administrators fight against their installation.
Can get very detailed information.
Also called Credential scan.
Some security devices can prevent some details of a scan from being successful.
Provides the scanner read-only access to the servers.
Scanner can access the operating system, databases, and applications on the server.
Comprehensive scanners provide you with different scan perspectives.
External scans provide a viewpoint of the attacker.
internal scans provide insider threat viewpoint.
Data center scans provide a close internal scan, one that might be blocked by other security devices.
PCI-DSS requires both internal and external.
Datacenter
External
Internal
Vendors provide templates for scans with common settings.
Admins can also create their own templates for commonly used scans.
This prevents errors ans saves time.
Plug-ins contain hundreds of vulnerabilities.
Enable/Disable plug-ins.
If Linux system Disable Windows plug-ins and visa-versa
Some scans can disrupt your systems or cause loss of data
Ensure you are scanning safely and with permissions.
Linux
Windows
Safe Checks
Will not allow an unsafe check to occur.
Sometimes vulnerability scans will knock out a service or server for a period of time.
Describes the extent of the scan.
What networks and systems are included?
How will you test if a system is on the network? Ping sweep.
What tests will be performed against the systems during a scan?
Importance of your scope.
Develop scope properly and gain agreement from staff and management.
Ensure you are unlikely to cause issues during your scanning efforts.
You do not want to take systems down during work hours.
Minimizing the scope.
Network segmentation often allows you to minimize your scope for compliance scans.
PCI-DSS networks should be segmented from the rest of the organizational network.
Is run on the client.
Web app spacific
Open source
Walkthrough
Install and load Nessus Web client.
Login
Policies Tab
Set up scan
Add and give it a name (Windows Scans)
Leave default if necessary.
--Vulnerability scan you may want to use a credentialed scan.
--An attacker will not use credentialed scan.
Plug-ins- turn on or off plug-ins depending on scan (Windows)
Preferences - If you have DCs on the network.
Scans tab and scan now or schedule a scan.
Select your policy or the policy you created.
Type scan targets.
Launch
After scan completes it will show up in reports.
by default the report will show you the most vulnerable.
Laws and regulations that require vulnerability management programs (like PCI_DSS, and FISMA) don't apply companies.
But....vulnerability management is still very important to them as a key component to security. Therefore, organizations can and do require scanning under their own corporate policies.
Start Small. Start with a small section of your network.
Expand slowly. Gradually add more scope to your scans.
Prevent overwhelming the enterprise systems and your sys admin team.
how often do we scan the systems?
Schedule determined by your goals to meet security, compliance, or other business requirements.
Automate email reports or alerts can be configured.
Example: Nessus scanner allows you to setup daily, weekly, monthly, or other scheduled scans by date/time.
Licensing Limitations
Scanners can control y concurrent scans can be performed through licensing.
Business Constraints
Do you have to avoid high business activity times?
Technical Constraints
Network may not support scanning everything.
Do you fall under FISMA or PCI-DSS requirements.
Organizational Risk Appetite
How much time between a new threat and scan?
What systems do you want to be covered by your scans?
Do you scan all systems or just critical assets?
Scanning tools like QualysGuard can be used to build your asset inventory automatically.
Admins then take that information and classify the systems as critical or no-critical.
Laws and regulations that govern information storage and processing. HIPPA, GLBA, and FERPA
Laws and regulations that require vulnerability management programs. PCI-DSS, FISMA
Federal Information Security Management Act
Specifies security controls for government. Both agencies and organizations that run the systems.
Systems are classified as low, moderate, or high impact which dictate the requirements.
Requirements:
Scan systems when new threats emerge.
Use tools/techniques that are interoperable
Analyze scan reports from assessments.
Remediate vulnerabilities based on risk.
share findings with other agencies to eliminate similar vulnerabilities in other systems.
Payment Card Industry Data Security Standard
Specific security controls for credit card processors and merchants.
Most specific of any requirement for vulnerability management.
Examples:
Internal and external scans must be conducted.
Scanned at least quarterly and all major changes
Internal scans by qualified individuals
External scans by approved scanning vendor
Remediate any high-risk vulnerabilities and re-scan until a clean report is achieved.