Container
Demo Help
Multiple Layers
User Instructions
THEN Skip user instruction
The container will find the previous instruction and skip
Install X first
Base Image Changes
Security
Debian or Linux flavor
Social Trends
Exploit Maturity
Software Composition Analysis
Operating System vs OSS
For Linux Packages
OS Package manager metadata
Deployments
Cloud
On-Prem
Broker
Base Image Recommendations
Most vulnerabilities are found here
User will get the least vulnerable version
Public Repos
Custom
Personal Registries
Git-Based PR Scanning
Automate PRs automatically
Remediation advice
Dockerfile scanning is less accurate
PreBUILT
Open a Fix PR
Integrate directly in a container registry
Benefit
The container has been BUILT
ACR
ECR
HarborCR
Talk about the CI/CD Pipeline
Choose to ignore "Base Image Vulnerabilities" in the scan
monitor the container within the Snyk UI
Based on gating
LEVERAGE the container CLI (Developer Endpoint)
Mention the container IDE (Limited though)
Talk about the remediation advice from the CLI
Build off of the SDLC Slide
Relative Importance
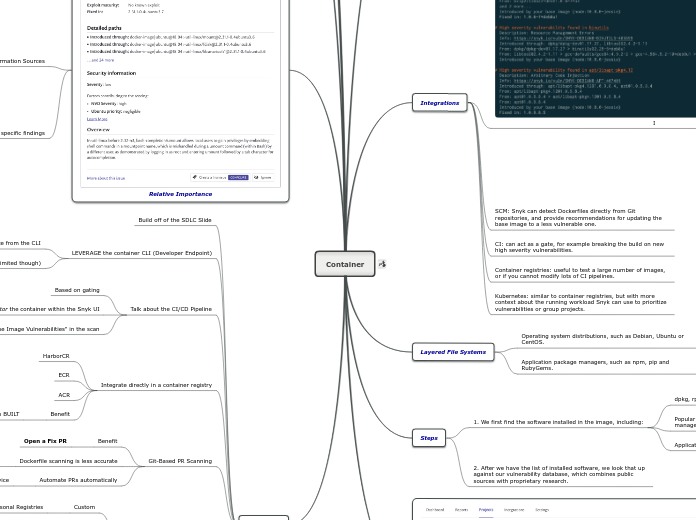
Distro specific findings
External Information Sources
Amazon Linux
SUSE Linux Enterprise Security Rating Overview
Red Hat Enterprise Linux Severity
Ubuntu CVE Priority
Debian Severity
NVD
Monitoring/Recurring Scans
snyk container monitor :
- Downloads the image if it’s not already available locally in your Docker daemon
- Determines the software installed in the image
- Sends that bill of materials to the Snyk Service
- Returns a list of the vulnerabilities in your image
Results on Snyk can be shared with other members of your team
Interactively filter the results and explore the list of vulnerabilities in your web browser
Snyk will alert you if new vulnerabilities are disclosed that affect your image, without you having to retest it locally
Integration which saves snapshot
File Fingerprinting
OpenJDK
Node.js
Supported OS's
Link Images
Snyk allows you to manually or automatically link from a Dockerfile to all container images built from it.
You can use this to understand the security impact on your running applications, and understand which images can be better secured, or need to be rebuilt, when taking action and updating the Dockerfile base image.
You can get automatic links between imported images (via container registry integration) to existing Dockerfile projects. This is done by checking whether the OCI label in the image matches the path of a Dockerfile that exists in the org in Snyk.
Steps
2. After we have the list of installed software, we look that up against our vulnerability database, which combines public sources with proprietary research.
1. We first find the software installed in the image, including:
Application packages based on the presence of a manifest file.
Popular unmanaged software, ie. installed outside a package manager.
dpkg, rpm and apk operating systems packages.
Layered File Systems
Application package managers, such as npm, pip and RubyGems.
Operating system distributions, such as Debian, Ubuntu or CentOS.
Integrations
Kubernetes: similar to container registries, but with more context about the running workload Snyk can use to prioritize vulnerabilities or group projects.
Container registries: useful to test a large number of images, or if you cannot modify lots of CI pipelines.
CI: can act as a gate, for example breaking the build on new high severity vulnerabilities.
SCM: Snyk can detect Dockerfiles directly from Git repositories, and provide recommendations for updating the base image to a less vulnerable one.
I
Specific Platform
snyk container test --platform=linux/arm64 debian
Direct Test Docker/OCI Archives
snyk container test docker-archive:archive.tar
snyk container test oci-archive:archive.tar
If Snyk determines the base image used, and the image uses an Official Docker image, the output includes recommendations for upgrades to resolve some of the discovered vulnerabilities.
Vulnerabilities appear in reverse severity order, so there's less scrolling up to see the most important issues.
If you use a Dockerfile to build your image, you can provide that when running Snyk.
Clearer Recommendations
Provides more Context
snyk container test : --file=Dockerfile
You can use Snyk to test any image that you can pull from a remote registry, or any image you have built locally and made available in your local Docker daemon.
snyk container test :
Install Snyk CLI
snyk container test debian
- Downloads the image if it’s not already available locally in your Docker daemon
- Determines the software installed in the image
- Sends that bill of materials to the Snyk Service
- Returns a list of the vulnerabilities in your image
snyk auth
npm – npm install -g snyk
Create images with security built-in from the start