GROUP MEMBER:
1)AIN IZYANI BINTI ZULKIFLI(193689)
2)WAN MARDHIAH BINTI WAN AYUB(193563)
3)NURAZIZAH BINTI OSMAN(194307)
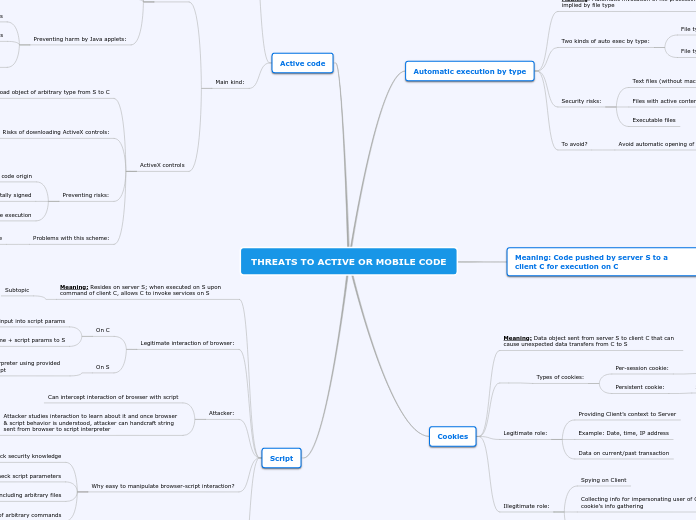
THREATS TO ACTIVE OR MOBILE CODE
Script
Scripting language
HTTP with CGI
When file in certain directory is named in URL (sent by browser), file is not sent back but executed as CGI script (a program). Only CGI script output is sent back for browser to display.
HTTP without CGI
When Web browser looks up URL, browser contacts HTTP server with this URL. HTTP server looks at filename named in URL & that file is sent back and browser displays file in the appropriate format
CGI (Common Gateway Interface)
Enables a client web browser to request data from a program executed on the Web server
Why easy to manipulate browser-script interaction?
Some scripts allow execution of arbitrary commands
Some scripts allow including arbitrary files
Don’t double-check script parameters
Programmers often lack security knowledge
Attacker:
Attacker studies interaction to learn about it and once browser & script behavior is understood, attacker can handcraft string sent from browser to script interpreter
Can intercept interaction of browser with script
Legitimate interaction of browser:
On S
Named script is executed by script interpreter using provided params, invoking services called by script
On C
Browser sends string with script name + script params to S
Browser organizes user input into script params
Meaning: Resides on server S; when executed on S upon command of client C, allows C to invoke services on S
Subtopic
Active code
Main kind:
ActiveX controls
Problems with this scheme:
It does not verify correctness of code
Preventing risks:
Digital signature verified before execution
Downloaded code is digitally signed
Authentication scheme to verify code origin
Risks of downloading ActiveX controls:
If no handler for type T exists on C, C asks S for handler for T then uses it to present object
E.g., attacker defines type .bomb
If handler (or viewer) for type T is available, it is invoked to present object
E.g., after file.doc downloaded, MS Word is invoked to open file.doc
Allows to download object of arbitrary type from S to C
Java code
Preventing harm by Java applets:
Control inter-aplet communication & applets’ effects on environment
Clear memory before its reuse by new objects
Control applets’ access to sensitive system resources
Security flaws in JVM implementations
No type checking for some data types
Security
Enforces type checking
Strongly typed
Designed to be truly machine-independent
Meaning: Recall: code pushed by S to C for execution on C. As demand on server S’s computing power grows, S uses client C’s computing power and
S downloads code to C (for execution on C), C executes it.
Cookies
Illegitimate role:
Attacker who intercepts X’s cookie can easily impersonate X in interactions with Server
Collecting info for impersonating user of Client who is target of cookie’s info gathering
Spying on Client
Legitimate role:
Data on current/past transaction
Example: Date, time, IP address
Providing Client’s context to Server
Meaning: Data object sent from server S to client C that can cause unexpected data transfers from C to S
Meaning: Code pushed by server S to a client C for execution on C
Conclusion
Implementation 2 is better because saves S’s processor time and network bandwidth
Implementation 2
- S sends animation code for execution to C
- C executes animation
- Each new animation frame is available for display locally on C
Implementation 1
- S executing animation (Network bandwidth)
- Each new animation frame must be sent from S to C for display on C
Example : Website with animation
Automatic execution by type
To avoid?
Avoid automatic opening of files by built-in handlers
Security risks:
Executable files
Files with active content
Text files (without macros!)
Two kinds of auto exec by type:
File type implied by embedded type
eg., File named “class28” without extension has embedded info that its type is “pdf”
File type implied by file extension
e.g., MS Word automatically invoked for file.doc
Meaning: Automatic invocation of file processing program implied by file type