Hacker Mind Maps - Public Gallery
Explore our wide public collection of hacker mind maps created by Mindomo users all over the world. Here, you can find all public diagrams related to hacker. You can view these examples to get some inspiration. Some diagrams also give you the right to copy and edit them. This flexibility allows you to use these mind maps as templates, saving time and giving you a strong starting point for your work. You can contribute to this gallery with your own diagrams once you make them public, and you can be a source of inspiration for other users and be featured here.

Policía Cibernetica
by LUEVANO CANTO LUEVANO CANTO

Que es la Guerra Cibernética
by Aura Báez

Seguridad en redes wifi
by Marina Fajardo

INGENIERIA DE SISTEMAS Y COMPUTACIÓN
by ELKIN MONTOYA MALAVER


VIRUS
by jihan zambrano
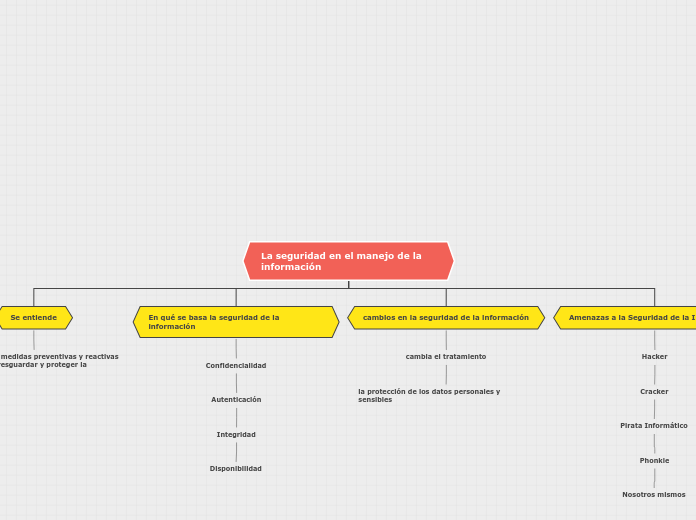

Organigrama
by Karla Georgina Espino Gutierrez
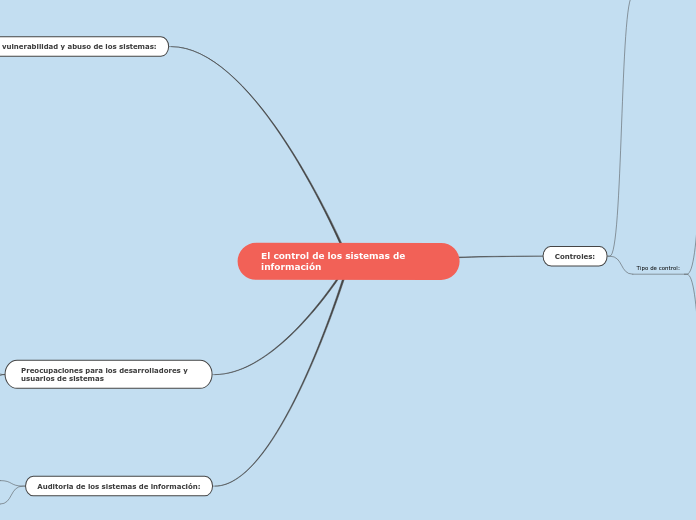

El control de los sistemas de información
by Monik Muñoz
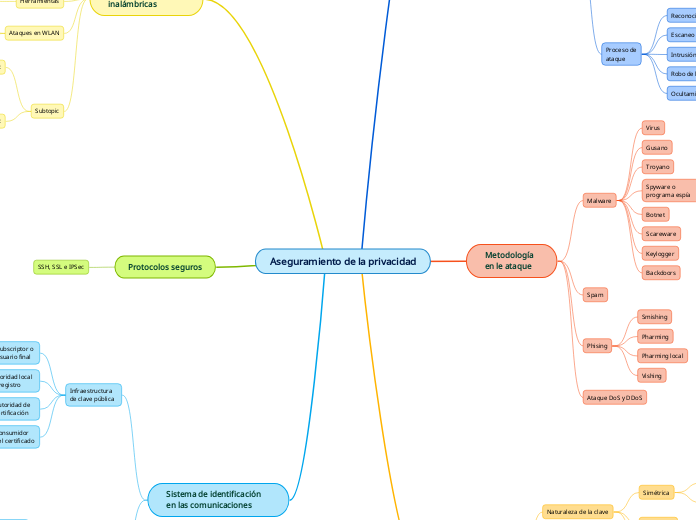

Aseguramiento de la privacidad
by Remigio Andújar Sánchez
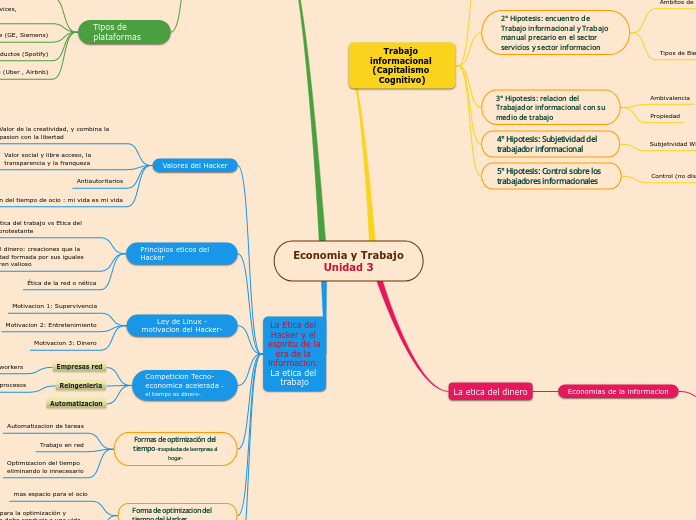

Economia y Trabajo Unidad 3
by MARIA DEL CARMEN PAREDES
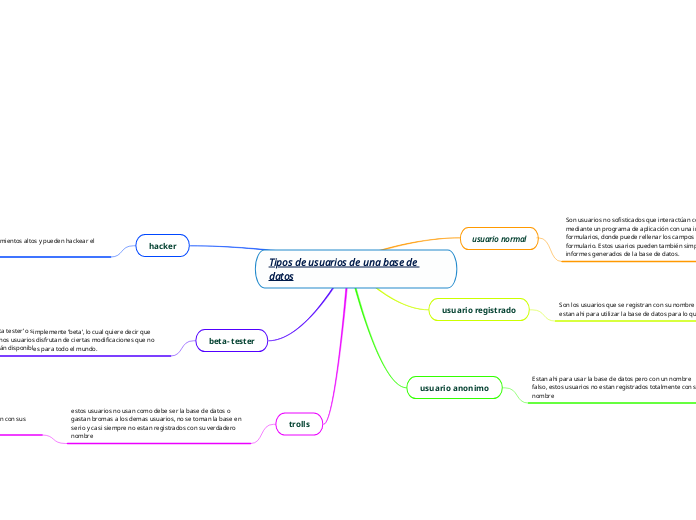

Tipos de usuarios de una base de datos
by Gabriel Eduardo Varela Sotelo


Las Tecnologías de la información y la comunicación
by Lianys Castillo

Inseguridad ciberneutica
by Nicolle Reveles
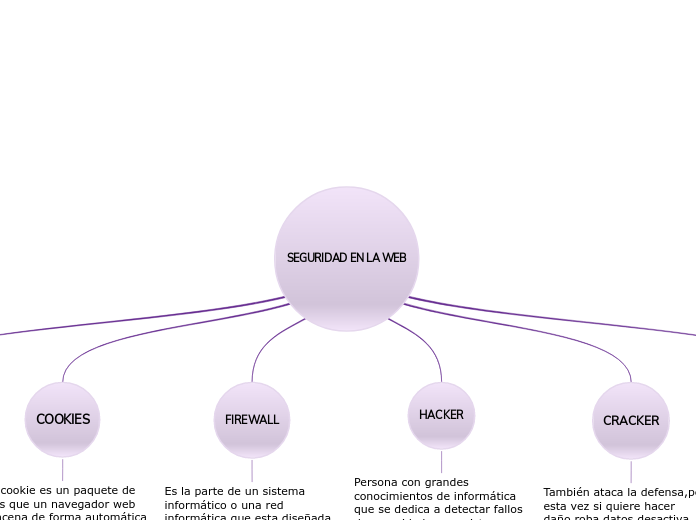

SEGURIDAD EN LA WEB
by Fabiola Vega
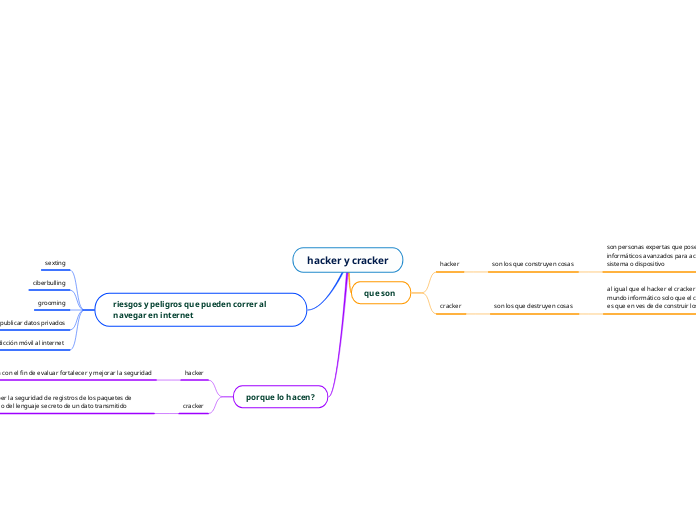

hacker y cracker
by salome OSORIO
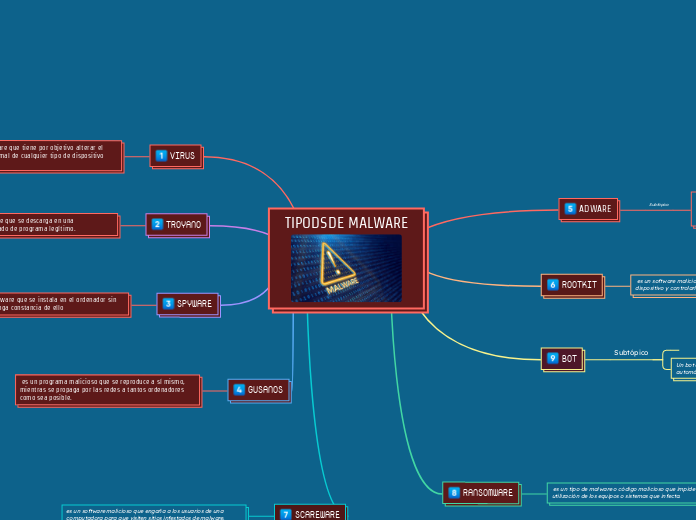

TIPODSDE MALWARE
by Jhon D'a
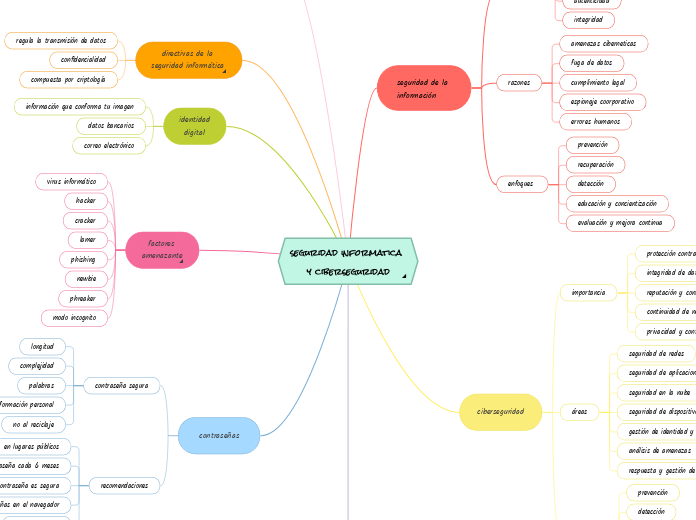

seguridad informatica y ciberseguridad .monica-writing-entry-btn { position: absolute; right: 1px; bottom: 1px; pointer-events: all; cursor: pointer; user-select: none; -webkit-user-drag: none; display: flex; flex-direction: row; justify-content: center; align-items: center; background: transparent; transition: all ease 0.2s; border-radius: 20px; border: 1px solid transparent; } .monica-writing-clickable-item { cursor: pointer; user-select: none; -webkit-user-drag: none; display: flex; flex-direction: row; justify-content: center; align-items: center; padding: 0 4px; height: 26px; color: #a0a0a0; } .monica-writing-clickable-item.monica-writing-first { border-top-left-radius: 20px; border-bottom-left-radius: 20px; } .monica-writing-clickable-item.monica-writing-last { border-top-right-radius: 20px; border-bottom-right-radius: 20px; } .monica-writing-clickable-item:hover { color: #3872e0; } .monica-writing-divider { background-color: #eeeeee; min-width: 1px; height: 12px; } .monica-writing-entry-btn:hover { background: #ffffff; border: 1px solid rgba(115, 114, 120, 0.15); } .monica-writing-caret { width: 1.5px; background-color: #3872e0; pointer-events: none; position: absolute; border-radius: 1px; } .monica-writing-caret-head { background-color: #3872e0; width: 6px; height: 6px; border-radius: 6px; position: absolute; left: -2.25px; } @media print { .monica-writing-entry-btn { display: none; } }
by LUCIA VALERIA DAVILA NUÑEZ



