door Wirda munira 1 jaar geleden
152
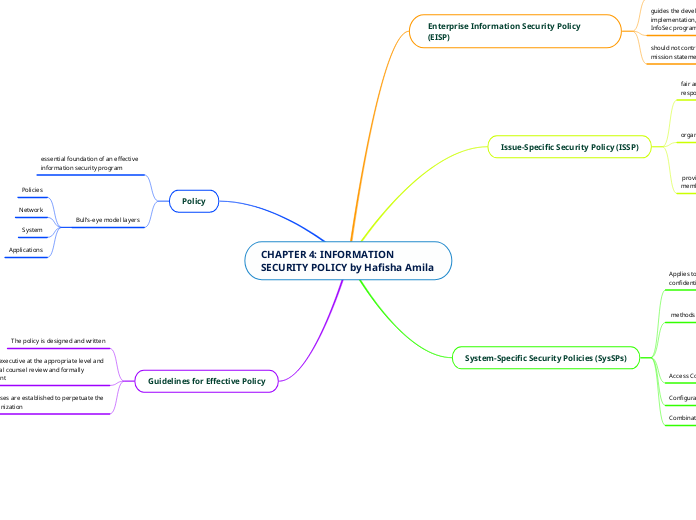
CHAPTER 4: INFORMATION SECURITY POLICY by Hafisha Amila
Crafting an effective information security policy involves multiple layers and specific approaches tailored to various organizational needs. System-specific security policies (SysSPs)