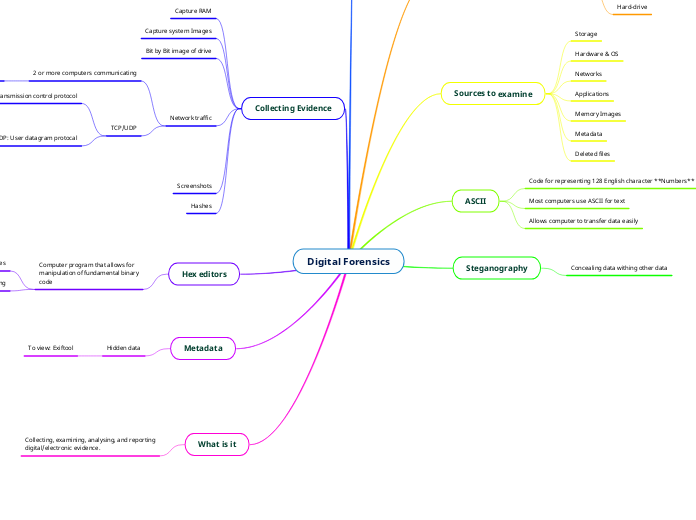
Digital Forensics
Volatility
Memory most to least
CPU cache/registers
Data stored in RAM
Files written to disk
Hard-drive
Sources to examine
Storage
Hardware & OS
Networks
Applications
Memory Images
Metadata
Deleted files
ASCII
Code for representing 128 English character **Numbers**
Most computers use ASCII for text
Allows computer to transfer data easily
Steganography
Concealing data withing other data
Wireshark
protocol analyser/ network packet
Packet
Unit of data transfer over a network
Contains data & other important info : Directed IP address
Recorded traffic in pcap files
Collecting Evidence
Capture RAM
Capture system Images
Bit by Bit image of drive
Network traffic
2 or more computers communicating
Wireshark, tcpdumb
TCP/UDP
TCP: Transmission control protocol
To setup a connect a handshake is preformed
UDP: User datagram protocal
Data is sent without connection
Fast
Common: video chatting, Onlinegaming
Screenshots
Hashes
Hex editors
Computer program that allows for
manipulation of fundamental binary
code
Examining and fixing corrupt files
Reverse Engineering
Metadata
Hidden data
To view: Exiftool
What is it
Collecting, examining, analysing, and reporting
digital/electronic evidence.