Mindomo
Assignment
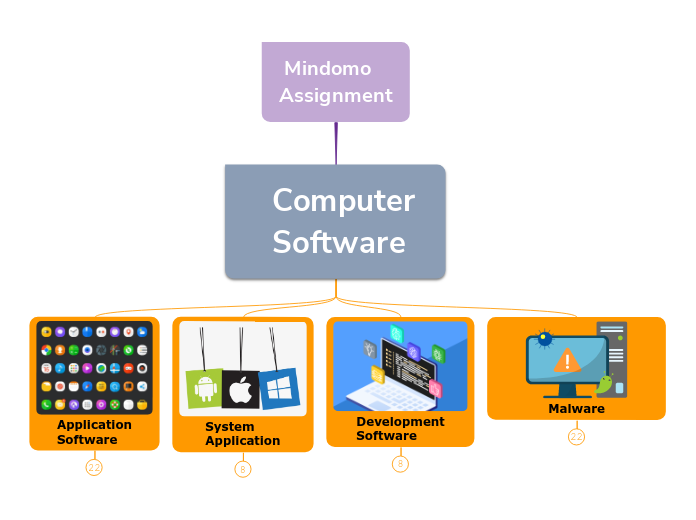
Computer
Software
Malware
Malware is a term for any piece of software that exists to be disruptive: Malicious Software. It's purpose is to infect, explore, steal or conducts virtually any behavior an attacker wants to a file or code.
5 Ways to prevent Viruses
Stay away from Unsecured WiFi
Stay with trusted and secure WiFi. Unsecured WiFi can be easily accessed by any hacker.
Think before you Click
Viruses can spread through e-mails, links etc. so beware of things sent to you that may seem suspicious
Choose a strong password
Make a complex password that's not easy to guess and includes numbers, capital letters, and special characters.
Use a Firewall
prevent unauthorized access into or out of a computer network
Install an AntiVirus
detects and remove viruses and other kinds of malicious software from your computer or laptop
Computer Virus Timeline
The HeartBleed Virus
-Appeared in 2014
-Allowed anyone on the internet to read the memory of systems using the vulnerable OpenSSL software.
The MYDOOM Virus
-Appeared in 2004
-Considered one of the most dangerous viruses
-Created "Zombies" out of computers which hackers could then access and create DDOS attacks.
-Caused more than $38 Billion worth of damage.
The CODE RED Virus
-Appeared in 2001
-Developed by Marc Maiffret and Ryan Permeh
-Was a worm
-Purpose was to exploit a vulnerability in Microsoft's Internet Information Server
-Manipulated computer protocols and spread in just a few hours
The ILOVEYOU Virus
-Appeared in 2000
-Is a virus and also a worm.
-Created by Onel De Guzman
-Was created to steal passwords for internet access since he couldn't pay for it due to College.
-Was spread through e-mails.
-Negatively affected around 45 million users.
The BRAIN Virus
-Debated as the first PC Virus.
-Appeared in 1986
-Developed by brothers, Basit and Amjad Farooq Alvi.
-Infected 5.2" floppy disks
-They were tired of customers making illegal copies of their software from their computer store so they developed Brain, which replaced the boot sector of a floppy disk with a virus.
The ANIMAL Virus
-The first Trojan Horse virus
-Appeared in 1975
-Developed by John Walker
-Used a try to guess the animal game in 20 questions to copy information and carry out actions without user approval
-However had no malicious intent
The RABBIT Virus
-Appeared in 1974
-Purpose was to get on a computer and make copies of itself until the machine crashed
-Did have malicious intent
The Creeper Program
-Appeared in 1971
-Considered the first computer virus
-Developed by Bob Thomas
-Designed as a security test to see if a self-replicating program was possible
-Had no malicious intent
As noted by Discovery, the Creeper program, often regarded as the first virus, was created in 1971 by Bob Thomas of BBN. Creeper was actually designed as a security test to see if a self-replicating program was possible. It was—sort of. With each new hard drive infected, Creeper would try to remove itself from the previous host. Creeper had no malicious intent and only displayed a simple message: "I'M THE CREEPER. CATCH ME IF YOU CAN!"
5 General Categories of Malware
Trojan Horse
Program or file that says it's one thing (like a video or game) and is really something else (like a virus or spyware). (e.g. RootKit)
Worm
Like a virus except it doesn't need to change existing programs to work. (e.g. Morris Worm)
Spyware/Adware
Collects information about the user and changes web searches or traffic to other sites. (e.g. Fireball Adware)
Backdoor
Any way around a security measure without authorization.
(e.g. Backdoor Trojan Horse)
Viruses
Spreads by copying itself. Can affect any type of computer functionality by changing existing programs. (e.g. ILOVEYOU virus)
Development
Software
A Development Software is a set of computer science activities dedicated to the process of creating, designing, deploying and supporting software. It's main purpose is to purpose of allowing people to create new pieces of code, or to fix old ones.
The 3 Categories of Development Software
Integrated Development Environment (IDE)
An interface, usually graphical, that combines an editor window used to write code, an interpreter and a compiler into one package. An IDE also allows you to "debug" or execute a program one line at a time while giving access to all of the program's memory. This is done in order to find problems within the code.
Interpreter
Executes commands. In fact, an interpreter takes a program one line at a time and executes each line as it arrives.
Compiler
A program that is used to translate code from one language (say C, Java or Python) into a language the computer itself understands . The result is usually a file that can be executed or run on the target system. A compiler does not execute commands.
System
Application
A System Application is used to run a computer's hardware and provides a platform for applications to run on top of and allows for communication between hardware and other software.
The 3 Categories of System Application
BIOS
Program responsible for Basic Input Output of a computer. (e.g. ASUS)
Device Drivers
Small programs that provide an Application Program Interface (API) which determines how other programs can interact with hardware.(e.g. Printers)
Operating System
Is a program that, after being initially loaded into the computer by a boot program, manages all of the other application programs in a computer.(e.g. Windows)
Application
Software
An Application Software is a computer software package that performs a specific function directly for an end user or, in some cases, for another application. An application can be self-contained or a group of programs.
The 4 Categories of Application Software
Education/
Reference
Thesaurus
Can be paired with a dictionary to find the definition, synonym, and antonyms of words.
Coding
Can be used to become familiar with programming language such as JavaScript and Python.
Encylopedias
Used to find information on various different types of topics and subjects
Math
Can be used to help solve and graph math problems and equations
Business
Customer Service
Allows for customers to contact companies for aid or complaints (e.g. Intercom)
Human Resources
lets you manage all the employee information under one roof (e.g. Employment Information Systems)
Accounting
lets users create and send invoices, upload receipts, track miles and view accounting reports (e.g. QuickBooks)
Finances
Applications can help you lets you track your cash flow
Entertainment
Streaming Services
continuous transmission of audio or video files from a server to a viewer (e.g. Netflix)
Video Players
An application used to playback videos (e.g. VLC)
Music Players
An application used for playing/listening to audio files (e.g. Spotify)
Video Games
Electronic games that can be played with the use of an input such as a controller(e.g.Fortnite)
Productivity
Photo Editors
used to change and alter pictures/photos in many different ways (e.g. Photoshop)
Database
a organized collection of ordered data, usually kept electronically in a computer system.(e.g. Excel)
Spreadsheets
used to store, organize and easily access information and data (e.g. Google Sheets)
Word Processors
a type of software application used for writing, editing, and printing documents.
(e.g. Google Docs)