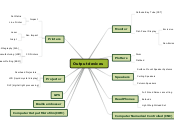
Access Contol
Why
Compliance
Security
Privacy
How
Technology
LDAP
ACLs
PKI
Active Directory
Anonymous vs known
Oversight
Policy
FIPS
Segregation of Duties
Least Priviledge Principal
Processes
Governance
Centralized
Decentralized
Mixed mode
Where
Remote
Partners
Employee facing
Client facing
When
Pre/post employment
Day of Week
Time of Day
Who
IT Security
Audit
ATIP
DSO
Clients
Identified
Anonymous
Super Administrators
Super Users
Administrators
Owners
Users
Status
Position
What
Threats
External
Phishing attacksSpear-Phishing attacksSocial EngineeringDOS attacksSpoofingMan-in-the-middle attacksInternal
SabotagePassword sharingUnlocked sessionsUncontrolled access to logsPrivilleged accessServices
Non Critical
Critical
Devices
Phones
Smartphone
Cell
Desktop
Mainframe
Storage
I/O devices
Connectivity Devices(switches, etc.)
Workstations
Servers
Facilities
Media
Integrated Circuit Disk (thumb drives)
Removable disk
Web-sites
Disk
Tapes
Applications
Screens
Information
Metadata
Lists
Directory Service
Documents
Data
Classification
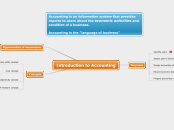
Classification is difficult for most users to understand and is, therefore, often neglected.
Classification is essential for data protection.
Unclassified
Top Secret
Secret
Classified
Protected C
Protected B
Protected A
Flat files
Database
Enterprise Controlled Access
Database Controled Access
Application Contoled Access
Functions
Monitoring and Reporting
Authorization/Access Control
Authorization can be direct (person 1 has access to system 1) or it can be abstracted by roles and entitlements (the auditor role has a read-only entitlement on to all data and meta-data)
Profiles
Roles
Authentication
Authentication is how you prove who you are:
Authentication can be performed using passwords, tokens or biometrics or a combination of the three.
Idenitification
Identification is about who you are:
"I am Santa Clause"