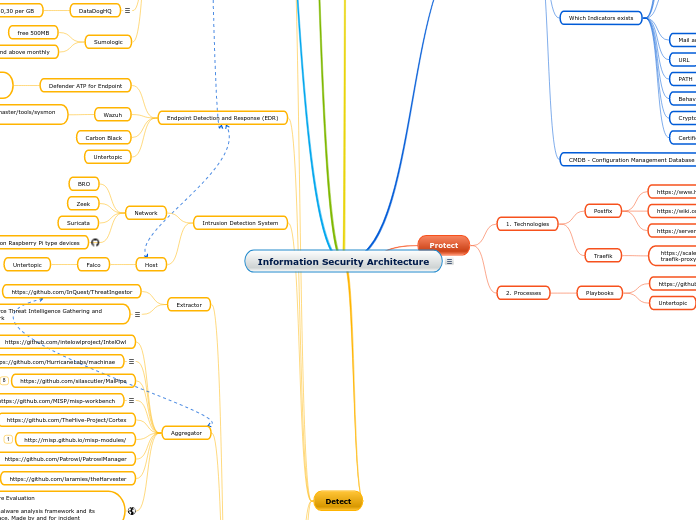
Information Security Architecture
https://www.nist.gov/system/files/documents/cyberframework/cybersecurity-framework-021214.pdf
Detect
Malware Analyse
Sandbox
HyperRun
AnyRun
Cuckoo (Selfhosted)
VMRay (Private)
Enrichment
Log enrichment
ELK for Mikrotik Netflow
https://github.com/robcowart/elastiflow
Mail
https://github.com/dragoangel/parsedmarc-dockerized
https://domainaware.github.io/parsedmarc/
Endpoint
Sysmon
https://browninfosecguy.com/sysmon-101
IoC Storage
[Looks unmaintained] YETI
[Looks Unmaintained] hippocampe
Hippocampe is a threat feed aggregator. It gives your organisation a threat feed 'memory' and lets you query it easily through a REST API or from a Web UI. If you have a
Cortex
server, there's already an analyzer to query Hippocampe. And if you use
TheHive
as a security incident response platform, you can customize the JSON output produced by the analyzer to your taste or use the report template that we kindly provide.
Hippocampe aggregates feeds from the Internet in an Elasticsearch cluster. It has a REST API which allows to search into its 'memory'. It is based on a Python script which fetchs URLs corresponding to feeds, parses and indexes them.
OpenCTI
https://kibana.opencti.io/s/public/goto/011b80ae0da7aca60de6db2d6cf76c75
https://medium.com/luatix/your-cyber-threat-intelligence-knowledge-in-a-magic-box-af2cbf7dd4be
https://www.notion.so/Using-Docker-03d5c0592b9d4547800cc9f4ff7be2b8#39617668dafb42648e8efb75f7d0a558
Minemeld
https://github.com/hkelley/splunksearch-miner
https://live.paloaltonetworks.com/t5/minemeld-articles/using-minemeld-to-create-a-managed-services-offering/ta-p/166505
https://live.paloaltonetworks.com/t5/minemeld-articles/enable-access-to-office-365-with-minemeld-updated/ta-p/224148
https://live.paloaltonetworks.com/t5/minemeld-articles/configuring-nodes/ta-p/77185
https://live.paloaltonetworks.com/t5/minemeld-articles/send-iocs-to-microsoft-graph-api-with-minemeld/ta-p/258540
https://hurricanelabs.com/blog/threat-intelligence-aggregation-and-deduplication-with-minemeld/
DNSBL (DNS Blacklists
https://en.wikipedia.org/wiki/Comparison_of_DNS_blacklists
IoC Feeds
https://socinvestigation-com.cdn.ampproject.org/c/s/socinvestigation.com/top-5-best-open-source-threat-intelligence-feeds/amp/
https://socinvestigation.com/cyber-threat-intelligence-tools-for-security-professionals-2021/
Accountless
https://opendata.rapid7.com/
https://openphish.com/feed.txt
https://twitter.com/dgafeedalerts
https://osint.bambenekconsulting.com/feeds/
https://www.botvrij.eu/
MISP Integration
https://sslbl.abuse.ch/
Virusshare
Samples
SANS Internet Storm Center
https://isc.sans.edu/suspicious_domains.html
Cisco – Talos Intelligence
https://feodotracker.abuse.ch/
https://threatview.io/
OSINT Threat Feed
Bitcoin Address
SHA Hash
MD5 Hash
https://threatfeeds.io/?feed=Talos%20IP%20Blacklist
https://socinvestigation.com
https://socinvestigation.com/threat-intelligence-dridex-malware-latest-iocs/
Website with IoCs, Hash, URL, IP, Domain,
Free Account required
https://pulsedive.com/
https://urlhaus.abuse.ch
Google – Safe Browsing
Google Account
https://bazaar.abuse.ch/
Twitter Account
Paid Account required
https://www.apivoid.com
https://www.ipvoid.com/
Aggregator
FAME Automates Malware Evaluation
Meet the open-source malware analysis framework and its user-friendly web interface. Made by and for incident responders.
https://github.com/laramies/theHarvester
https://github.com/Patrowl/PatrowlManager
http://misp.github.io/misp-modules/
https://github.com/TheHive-Project/Cortex
https://github.com/TheHive-Project/CortexDocs/blob/master/analyzer_requirements.md#free-analyzers
TBD
Virustotal
https://github.com/MISP/misp-workbench
Malware/IOC ingestion and processing engine
MISP
https://github.com/silascutler/MalPipe
BambenekFeeds (osint.bambenekconsulting.com/feeds/)
VirusTotal (https://www.virustotal.com)
FeodoBlockList (https://feodotracker.abuse.ch)
Malc0deIPList (http://malc0de.com/)
NoThinkIPFeeds (www.nothink.org/)
OpenPhishURLs (https://openphish.com
TorNodes (https://torstatus.blutmagie.de)
MalShare (https://malshare.com/)
https://github.com/HurricaneLabs/machinae
Machinae is a tool for collecting intelligence from public sites/feeds about various security-related pieces of data: IP addresses, domain names, URLs, email addresses, file hashes and SSL fingerprints. It was inspired by
Automater
, another excellent tool for collecting information.
https://github.com/intelowlproject/IntelOwl
Extractor
GOSINT - Open Source Threat Intelligence Gathering and Processing Framework
https://gosint.readthedocs.io/en/latest/configuration.html
https://github.com/ciscocsirt/GOSINT
Custom Feed URLs
Whitelist Domains
Whitelist ISP
Alexa Whitelist
CRITs
VirusTotal
AlienVault
Twitter
https://github.com/InQuest/ThreatIngestor
Intrusion Detection System
Falco
Network
Network Security Monitoring on Raspberry Pi type devices
Suricata
Zeek
BRO
Endpoint Detection and Response (EDR)
Carbon Black
Wazuh
https://github.com/0xrawsec/whids/blob/master/tools/sysmon/v13/sysmon-v13.x-optimal.xml
Defender ATP for Endpoint
https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/become-a-microsoft-defender-atp-ninja/ba-p/1515647
SIEM - Central Security Log System
https://ateixei.medium.com/different-siems-same-challenges-only-time-generated-will-tell-fee56b9391e9
https://stackify.com/best-log-management-tools/
https://www.comparitech.com/net-admin/best-windows-event-log-management-tools/
https://wlambertts.medium.com/zero-dollar-detection-and-response-orchestration-with-n8n-security-onion-thehive-and-10b5e685e2a1
https://ateixei.medium.com/different-siems-same-challenges-only-time-generated-will-tell-fee56b9391e9
Sumologic
$200 and above monthly
free 500MB
DataDogHQ
https://www.datadoghq.com/pricing/
$0,30 per GB
Elastic Search
Loggly
Sematext
start monthly at $60
Free 500MB 7d retention
LogRhytm
Logz.io
30d retention for $2,25 per GB; start for 2GB
https://logz.io/blog/docker-logging/
HELK
https://siemonster.com/
Graylog
Security Onion 2
ExaBeam
Splunk
https://github.com/LetMeR00t/TA-thehive-cortex
App / SA - Security App | Dashboards, Searches, ...
TA - Technical Addon | Ingest Data
Respond
Case Management
FIR - Fast Incident Response
TheHive
EmailScanner is an integration application in python that uses `exchangelib` to process mail items in Microsoft exchange.
Reading and processing of email folders for TheHive + Autoupdating case histories
https://github.com/arnydo/Synapse
Endpoint Incident Response Tools
Agent required
GRR
Agentless
Thor, Thor Lite | Nextron
Workflow
Splunk Phantom
Cortex XSOAR Palo Alto
Shuffle
n8n
Recover
Additional Supporting Tools
Choose the best MSSP
https://medium.com/@Mag1cM0n/5-questions-you-should-ask-your-security-monitoring-service-provider-mssp-fec36403d1d2
Test
https://github.com/redcanaryco/atomic-red-team
https://github.com/redcanaryco/invoke-atomicredteam
sed regex verifier
https://sed.js.org/
What is AbuseIO?
It is a toolkit anyone can use to receive, process, correlate abuse reports and send notifications with specific information regarding the abuse case(s) on your network. AbuseIO's purpose is to consolidate efforts by various companies and individuals to automate and improve the abuse handling process.
Breach Information
https://igotphished.abuse.ch
Have I been pawned
GoAccess
What is it?
GoAccess is an open source real-time web log analyzer and interactive viewer that runs in a terminal in *nix systems or through your browser.
Manipulate and extract envfiles in json format.
Banditore retrieves new releases from your starred GitHub repositories and generate an Atom feed with them.
Protect
Processes
Playbooks
Untertopic
https://github.com/certsocietegenerale/IRM/tree/master/EN
Technologies
Traefik
https://scaleup.us/2020/06/21/how-to-block-ips-in-your-traefik-proxy-server/
Postfix
https://serverok.in/postfix-rbl
https://wiki.centos.org/HowTos/postfix_restrictions
https://www.howtoforge.com/virtual_postfix_antispam
Identify
CMDB - Configuration Management Database
Service NOW CMDB
Which Indicators exists
Certificates
x509
Cryptocurrency Wallets
Bitcoin Addresses
Behavior
PATH
URL
Mail address
Hash
SHA512
SHA256
SHA1
MD5
Host
Domain
IP
Asset Discovery
...
Nozomi Networks
What to check?
Network Indicators
Files
Office Files
Executables
other files
Mails
Logs