作者:Robert Mccausland 16 年以前
2490
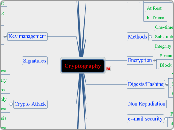
Cryptography
The text delves into various aspects of cryptography and its applications in securing information. It covers key management practices, including the creation, distribution, storage, and destruction of cryptographic keys.