Internet Risk
You can now Download your mind map and use it to communicate with your stakeholders.
It can then become the basis for detailed planning and scheduling.
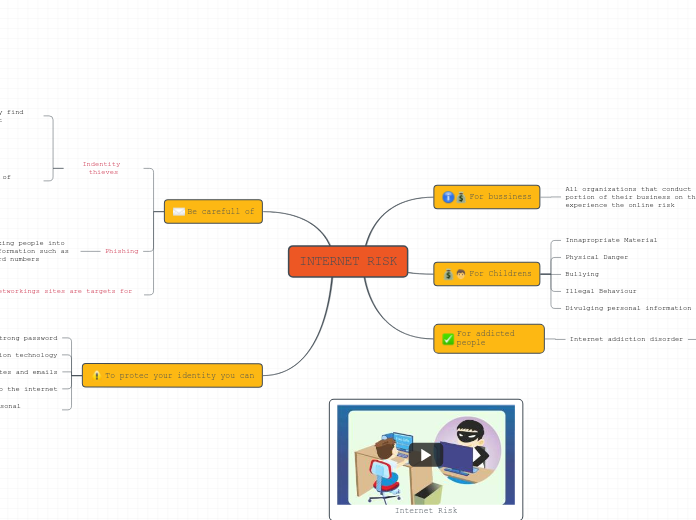
INTERNET RISK
Enter your project name
Begin by typing your project name into the Central Topic.
To protec your identity you can
Beware of asked for your personal information
Use encrypted connections to the internet
Learn how to "Phys" websites and emails
Uses strong authentication technology
Use the strong password
Be carefull of
Social networkings sites are targets for scams
Instagram
Twitter
Add other communication events that will support your project
Facebook
Include a project review?
The project review meeting takes place once the project has been closed, and examines the processes that led to both success and failure in the project.
Add a description of the meeting goals in the Notes panel
Phishing
It is the crime of tricking people into sharing confidential information such as passwords and credit card numbers
Indentity thieves
Signs that you might be a victim of identity thieves
Missing mail
Undamiliar mail
Medical insurance statement
Collection agency calls
Credit card gets declined
Errors on your credit report
They can use the information they find online to drain your bank account
Add a communication/collaboration tool.
Examples include:
- Physical meetings
- E-mail distribution lists
- Instant messaging and virtual meetings
- Local or cloud-based file sharing
- Online project management tools
- Online discussion boards
- Collaborative tools
For addicted people
Internet addiction disorder
Refers to excessive computer use which interfers with daily life
Add a requirements management technique
Techniques might include:
- Using a process for discovering requirements
- Maintaining a master list of requirements
- Writing testable and measurable requirements
- Establishing a formal process for agreeing on changes to the requirements
For Childrens
Divulging personal information
Illegal Behaviour
Bullying
Physical Danger
Innapropriate Material
For bussiness
All organizations that conduct some portion of their business on the internet experience the online risk
Their online risk can be in
Type in a project deliverable
For example:
- A key document or agreement
- Some equipment or working software
- An event, such as a demonstration or training
Processes by which the organization operates
Information about projects
Personal data