af lama hazaa 7 år siden
209
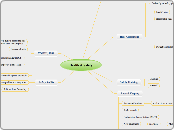
Sample Mind Map
Ensuring the security and control of information systems is crucial for businesses, especially when handling electronic evidence and computer forensics. Digital evidence plays a significant role in uncovering white-collar crimes, with proper data management streamlining legal discovery processes.
Åben
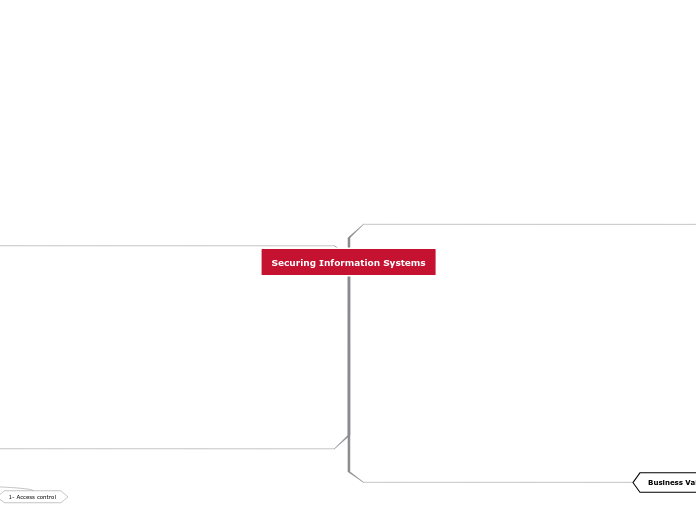
Securing Information Systems Technologies and Tools for Protecting Information
Resources 1- Access control 2-Authentication 3-Techniques for preventing unauthorized access to a system are listed Tokens Password system 4-Technologies and Tools for Security Smart card Biometric authentication Unified threat management (UTM) systems Intrusion Detection Systems, and Antivirus Software Antivirus and anti-spyware software: 1-Antivirus 2-Anti-spyware software Intrusion detection systems: Encryption and Public Key Infrastructure Two methods of encryption:Symmetric key encryption
and Public key encryption Two methods for encryption on networks:(SSL) and (TLS) Encryption Establishing a Framework for Security and Control The rule MIS auditing Disaster Recovery Planning and Business Continuity Planning make info easier to remember
interesting
save time 3-Identity management 2- Acceptable use policy (AUP) 1- Risk assessment Probability of occurrence during year Potential losses, value of threat Expected annual loss Business Value of Security and Control Electronic Evidence and Computer Forensics 4- Ambient data 2- Proper control of data can save time, money when responding to legal discovery request 3- Computer forensics 1-Evidence for white collar crimes often found in digital form Legal and Regulatory Requirements for Electronic Records Management Sarbanes-Oxley Act HIPPA Gramm-Leach-Bliley Act System vulnerability software vulnerability commercial software contains flaws that create security vulnerability internal threats: employee social engineering security threats often originate inside an organization Computer crime click fraud pharming evil twins phishing identity theft Hackers and computer crime distributed denial-of-service denial-of-service attacks(DoS) sniffer cracker Hacker Malicious software spyware 3- Trojan horses 2-worms 1- viruses Larg public networks facing threats because: 4- Network open to anyone 3- Email used for transmitting trade secret 2- size of the internet 1- Email attachment Wireless security challenges 2- the service set identifiers 1- war driving Storing problems 4-Use of networks and computer outside of firms control 3- Disasters 2- Hardware problems 1- software problems security control Subtopic