Computer and Society (CS)
What's your essay about?
Type in the title of your essay.
Response
Legal precedent
Consider the potential for negative publicity
Review
Evaluate how the organization responded
Determine exactly what happened
Follow-up
Determine how security was compromised
Eradication effort
Create new backups
Verify necessary backups are current and complete
Collect and log all possible criminal evidence from the system
Act quickly to contain an attack
Document all details of a security incident
All external conversations
All system events and Specific actions taken
Incident notification defines:
Who to notify and Who not to notify
Primary goals
Limit damage
Regain control
Response plan
Approved by
Senior management
Legal department
Develop well in advance of any incident
Educating Employees, Contractors, and Part-Time Workers
Help protect information systems by:
Reporting all unusual activity
Applying strict access controls to protect data
Not allowing others to use passwords
Guarding passwords
Discuss recent security incidents that affected the organization
Educate users about the importance of security
Motivate them to understand and follow security policy which is a written statement that defines an organization’s security requirements, as well as the controls and sanctions needed to meet those requirements.
Prevention
Perform a security audit: A process that evaluates whether an organization has a well-considered security policy in place and if it is being followed.
Back up critical applications and data regularly
Keep track of well-known vulnerabilities
CERT/CC
SANS
Antivirus software
Scans for a specific sequence of bytes
Examples: Norton Antivirus, McAfee
Firewall
Limits network access
Risk Assessment
Aims to improve security in areas with:
Poorest level of protection
Highest estimated cost
The process of assessing security-related risks from both internal and external threats to an organization’s computers and networks
Reducing Vulnerabilities
To increase the security of a system, we need to…
Create a clear reaction (response) plan
Monitor to detect a possible intrusion
Educate users
Identify actions that address the most serious vulnerabilities
Assess threats to an organization’s computers and network (i.e., risk management)
Requires a wide range of activities to be effective
Combination of technology, policy, and people
Cyberterrorists
An individual who launches computer-based attacks against other computers or networks in an attempt to intimidate or coerce a government in order to advance certain political or social objectives.
Cybercriminals
Loss of customer trust has more impact than fraud
Engage in all forms of computer fraud
An individual, motivated by the potential for monetary gain, who hacks into computers to steal, often by transferring money from one account to another.
Industrial Spies
Industrial espionage
Obtains information not available to the public
Uses illegal means
Competitive intelligence
Gathers information available to the public
Uses legal techniques
Someone who uses illegal means to obtain trade secrets from competitors.
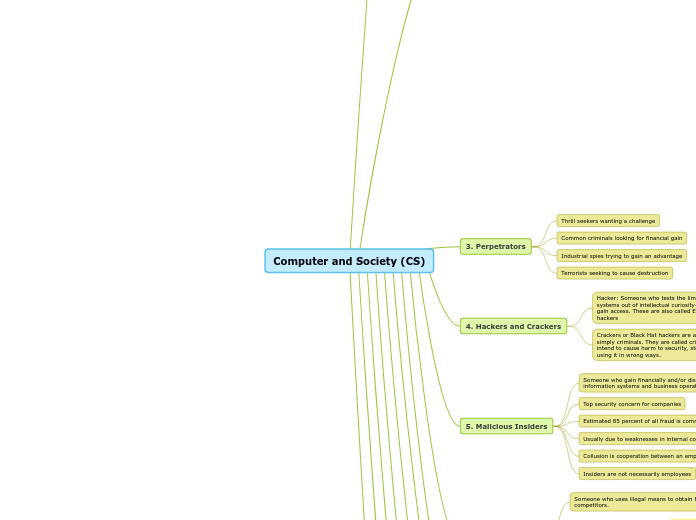
Malicious Insiders
Work on the structure of your essay.
Insiders are not necessarily employees
Can also be consultants and contractors
Collusion is cooperation between an employee and an outsider
Usually due to weaknesses in internal control procedures
Estimated 85 percent of all fraud is committed by employees
Top security concern for companies
Develop the ideas presented in the introduction.
Someone who gain financially and/or disrupt company’s information systems and business operations
Create a catchy introductory paragraph.
Take into consideration the interests of your audience.
Hackers and Crackers
Crackers or Black Hat hackers are also called cheaters or simply criminals. They are called criminals because they intend to cause harm to security, stealing very useful data and using it in wrong ways.
Hacker: Someone who tests the limitations of information systems out of intellectual curiosity—to see if he or she can gain access. These are also called Ethical Hackers or white hat hackers
Perpetrators
Terrorists seeking to cause destruction
Industrial spies trying to gain an advantage
Common criminals looking for financial gain
Thrill seekers wanting a challenge
Types of Attacks
Analyze another essay written on this topic
Find at least one example and see whether it is well written or not.
Most frequent attack is on a networked computer from an outside source
Type in the title and the author(s)
of the essay which you're going to analyze.
Distributed denial-of-service (DDoS)
Egress filtering
Ensuring spoofed packets don’t leave a network
Subtopic
Ingress filtering
When Internet service providers (ISPs) prevent
incoming packets with false IP addresses from being passed on.
Spoofing generates a false return address on packets therefore, sources of attack cannot be identified and turned off
Does not involve a break-in at the target computer
Legitimate users cannot get in
Target machine is busy responding to a stream of automated requests
Malicious hacker takes over computers on the Internet and causes them to flood a target site with demands for data and other small tasks
The computers that are taken over are called zombies
Trojan horse
Is the logical sequence of the essay accurate or faulty?
Select an option:
AccurateFaulty
Used to steal passwords, or spy on users by recording keystrokes
Users are tricked into installing it
disguised as iTunes file or malicious web site
Add some reasons to support your previous choice.
Program that a hacker secretly installs
Worm
Negative impact of virus or worm attack
Effort for IT workers
to clean up mess
Lost productivity
as IT workers attempt to recover data & programs
Lost data and programs
Can propagate without human intervention (unlike viruses)
replicate itself in order to consume resources to bring system down.
Harmful programs
What evidence do(es) the author(s) present?
Type in the evidence.
Add notes if you need larger blocks of text.
Reside in active memory of a computer
Virus
Famous Virus: Melissa
Infect documents
insert unwanted words, numbers or phrases
Macro viruses
Created in an application macro language
Most common types of virus and easily created
Does not spread itself from computer to computer
Must be passed on to other users through
Shared files
Infected e-mail document attachments
Deliver a “payload”
reformat hard drive
delete or modify a document
display a message
Often attached to files - when file is opened, virus executes
that causes a computer to behave in unexpected and undesirable manner
Usually disguised as something else
Malicious pieces of programming code
What claims do(es) the author(s) make?
Type them in.
IT Security Incidents: A Worsening Problem
Research your topic
Write down the sources you will base your essay on.
Computer Emergency Response Team Coordination Center (CERT/CC).
Higher computer user expectations.
Computer users share login IDs and passwords
Computer help desks
Sometimes forget to
Check whether users are authorized to perform the requested action.
Verify users’ identities.
Under intense pressure to provide fast responses to users’ questions.
Bring Your Own Device.
A business policy that permits and encourages employees to use their own mobile devices (smartphones, tablets, or laptops) to access company computing resources and applications.
Increased reliance on commercial software with known vulnerabilities.
Since security fixes could make Software harder to use or
eliminate “nice to have” features.
US companies continue to use installed software “as is”
JRE
RealPlayer
IE
Often patches are released on a regular basis, one example being Microsoft’s Patch Tuesday. On the second Tuesday of each month, Microsoft releases security fixes that resolve identified holes. If, however, a critical vulnerability is discovered, a patch may be released outside of schedule
Software developers quickly create and issue patch:
delays in installing patches expose users to security breaches
users are responsible for obtaining and installing patches
- which they can download from the Web
a “fix” to eliminate the problem
Zero-day attack
Takes place before a vulnerability is discovered or fixed
Exploit
Due to poor system design or implementation
Takes advantage of a particular system vulnerability
Attack on system
Increasing complexity increases vulnerability.
Number of possible entry points to a network expands continuously as more devices added.
this increases possibility of security breaches
Continues to increase in complexity:
all interconnected and driven by 100s of millions of lines of code.
switches, routers, gateways
apps, web sites
networks, computers, OSes
Computing environment is enormously complex
.
Number of IT-related security incidents is increasing around the world.
Security concerns must be balanced against other business needs and issues.
Security of information technology is critical
List first-hand information :
- historical and legal documents
- eyewitness accounts
- results of experiments
- statistical data
- pieces of creative writing