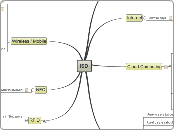
ISD
RFID
System structure
RFiD tag - innovation but not the main innovation
Main innovation is in the RFiD system!
Rotate RFID - structure of the system slide 90deg, and u get:
Process
Applications
Database
Server
Reader
RFID tags
which is the standard systemic structure. the system actually refers to the organization structure rather than the IT structure.
eg. should i buy iphones or netbooks or blackberries etc for employees? have to look at whole structure! look at strategy, process, applications to be used, etc.
Standards
How to define standards in IT
1. Institution defines the standards (ISO, UFI etc)
- eg. if u wanna build new sockets, you must follow the specs etc.
- more top-down, wanna codify info into RFID, top will impose
2. Standard De Facto (typical for IT)
- eg. standards that derive from facts
- everyone company pushes their own product for their own standard. One company will prevail
- this is bottom-up, market decided the standard
NB:
- if something does not become the standard fast enough, the S-curve will change and go downwards instead.
Applications in Singapore
EZ-Link cards
RFID tags are located within EZ-Link cards and readers.
EZ-Link cards work as a smart card for payments made in Singapore on a wide range of areas. They have also been hybrid-ized with NETS to form NETS EZ-Link which allows a greater range of payment methods.
These areas include:
Payments for ERP, all forms of public transport, Mcdonalds, food in foodcourts, 7-11, etc etc.
EZ-Link cards with personal identification may be used for identification purposes too.
These areas include:
Enlisting for national service, borrowing books from the library, taking attendance at schools, concessionary rates for public transport for students, online shopping etc.
IT
EZ-Link card readers are the main form of hardware, other than the cards themselves. Most merchants and many other institutions are required to have the card readers for scanning.
Information Flow
A whole truckload of information is being transmitted, especially with regards to EZ-Link person identification. Information on number of books borrowed, systems within institutions that require personal identification, amount of cash within the EZ-Link card when checked online, etc etc all mean information is flowing all the time to the main EZ-Link system, with huge databases.
Electronic Road Pricing
How it works + uses
RFID tags are located within the ERP hardwares.
IT
Hardware is required for ERP, such as the ERP gantries' scanners, and every RFID card reader to be installed in all Singapore-registered cars.
Mission/Strategy
Government mission is to reduce congestion during peak hours on roads leading to and from commercial areas within Singapore.
The strategy of implementing the system would be to designate the Land Transport Authority with rights to decide areas for implemention, outsourcing to technological companies to construct the system.
Process
Government implements this system by outsourcing the technology to Phillips Corporation in installation of hardware.
NFC
Who/What is involved
Eg. RFID tag in handphone to buy coffee.
Who/what is involved:
1. Users
2. Merchants - must have NFC readers
3. Government infrastructure will have to be extended, considering that this is probably to be used in many govt institutions with regards to public services
4. Public awareness activities
5. Banks or telecommunication companies (depending on decided system of who is gonna charge and how) must have a system in place for NFC for debit charging of items through NFC
6. Hardware production, selling
Wireless / Mobile
Mobile IT innovations
Mobile Applications
Shazan
Mobile application for identifying music.
Shazan -- Wireless - programme, process, requiring internet
Software
Hardware -- Internet -- Server
- connects to internet then to server
- needs to transmit signals fast to the server. to transmit signals, alternatives are WIFI, bluetooth, interconneccting devices (router), 3G (UMTS)
- eg. WIFI (LIUC LAN), 3G (VODAFONE, TIM)
Quality of internet connection determines quality of activity.
All levels must be good for the best experience. One screwed up area means the whole process will be bad.
Factors to be considered - speed, range of connection, cost
GPS Navigation
GPS has become a widely used aid to navigation worldwide, and a useful tool for map-making, land surveying, commerce, scientific uses, tracking and surveillance, and hobbies such as geocaching and waymarking. Also, the precise time reference is used in many applications including the scientific study of earthquakes and as a time synchronization source for cellular network protocols.
How it works
Organizational structure
Process
To support supply chain management and mobile commerce.
TO BE RESEARCHED
Windows
Google
Nokia
Apple
Wireless Cocktail
WAN - wide area network (eg 3G)
MAN - metropolitan area network (eg WIFI)
LAN - local area network (eg router)
PAN - personal area network (eg bluetooth)
- this is just a question of range, and unprecise.
Wireless cocktail
- different technologies may increase in range and shift within the model
Company Structure
ORGANIZATION
Mission
Strategy
Processes (eg. marketing, production)
Information flow
IT
Software applications
Hardware devices
Communication between different areas of organizational structure
Between:
i) Strat/Processes - Collaboration
ii) Information - Communication
iii) Software applications - Data transfer
iv) Hardware - Signal Transmission
IS v IT
Assignment
choose a company not belonging to the IT industry and create a reasonable example of how its its information system works:
1. idenitify an organizational role and describe it in terms of:
- the activity it performs
- the decision it is expected to take
- the related information requirements
2. identify an event (internal or external to the organization) that may bring raw information that can contribute to create an information item meeting one or more of the information requirements identified in 1.
and describe this event in terms of raw information
3. briefly describe how this raw information should be transformed into useful information to meet the information requirements
4. identify how raw information could be transformed into useful information, the processes, the organizational rules, the people and the IT that may be involved in this transformation.
Raw --> Useful
Process of info from event
Information from event:
1. Clients' latest financial statements
2. Clients' new forecast of cash flows
3. Clients' future operational and budget plan
4. Meeting with client
Process of info from event:
Head of tax dept will have to review the new financial statements, compare them to the old ones, singling out key items such as revenue and expenses. By finding out the differences, economic crisis impacts can be seen in terms of financial values to see if impact is small or large. Synthesizing: Key financial ratios from both pre-econ crisis and post-econ crisis will also be drafted out for evaluation and comparison. After comparison, head of tax dept will have to take financial factors into account to see if client company will eventually be able to sustain itself in order to pay for its tax services.
Head of tax dept will then look at clients' new forecast of cash flows to see if they are realistic and achievable based on knowledge of industry and experience. If realistic and achievable, head of tax will then have to evaluate the new forecast to see if company has continued ability to pay for its tax services.
Head of tax dept will then look at overview of clients' future operational and budget plan. Client is likely to only provide a overview for accounting firm's review. Head of tax dept will have to study plan to see if client has continued ability to pay for its tax services.
Head of tax dept will have to meet the client to discuss if client wishes to continue engaging PwC for its tax services.
Taking all the different information, processing it and analysing it, Head of taxation dept will then make a decision on whether to keep client company engaged, to lower taxation fees, or to disengage the company,
Information from event
Information from event:
1. Clients' latest financial statements
2. Clients' new forecast of cash flows
3. Clients' future operational and budget plan
4. Meeting with client
Clients will have their financial statements, forecast of future cash flows and operational budgeting plan drastically affected by the new economic crisis. New forecasts, operation and budgeting plans will have to be formed in order to handle the crisis and ensure client companies remain in operation.
Event
Economic crisis hits Asia, major drop in profitibility of all companies in the world.
Information required
Information required:
1. Clients' yearly financial statements (either direct from client or from PwC's bookkeeping department)
2. History of clients' financial statements and notes to financial statements
3. Company laws of country (especially absolvency and taxation laws)
4. Yearly meeting minutes with client.
Activity & Decision
Activity:
To do a yearly review of clients' profitability to see if they have client company has the ability to pay for tax computation and submission services done by PwC.
Decision:
To decide if client company should continue to be contractually engaged to pay for taxation services offered by PwC.
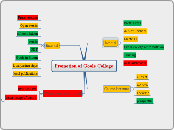
Head of Taxation Dept, PwC
1. Any medium-large accounting firm, eg PwC
a) Organizational role: Head of Taxation
Activity: To approve all tax returns, manage tax department, evaluate employees performance, participate in budgeting process of company
Decisions: as described above.
Information required: information on tax returns from employees, information on clientele expenses profit and financial situation, information from tax law of country, information on company's performance and budgeting
b) Economic crisis in asia
Head of Tax must now re-evaluate all clients' financial situation to see profitability of clients, which will in turn affect profitability of moore-stephens. All clients' engagements must be reviewed by obtaining information on their financial statements, review of past performances to see continued profitability, and consequences of potential disengagements.
c) These raw information will in turn be processed by the Head of Tax and/or with help by lower-level employees by analysing important relevant financial ratios, making forecasts of future cash flows of client companies, and a final decision to be made on retaining/disengaging client. Processed information will then be reverted up to higher level management for final decision approval.
Aurelio says (about IS flow)
Flow:
activity -> decision -> info requirements (t)
Information requirements are not stable. This is not obvious in many companies. Change continuously. Hence, it is a system not a store. Changes because output does not remain the same.
Info is a resource because of the relation to this logic.
IS delivers info that satisfies info requirements internal and external of the company.
USER of INFO vs END-USER
eg.
truck arrives
- amount of material
- type of material
- time
- cost
Inputs must be very good, then good processing for good output. If not, time and money will be wasted on processing if raw information is not relevant.
Aurelio says (about IS)
IS:
Managing info (CxO)
- store
- process/analyze
- exchange
When you talk about IS, definitions depend on background and type of work person is doing at the moment. So, there might be different defns when talking with someone else about IS in business.
Square = specialized ppl
Circle = holistic ppl
Problem is to link both sets of ppl.
Hexagon = more sides more edges, the more u do it it becomes a circle (analogy)
Many projects fail because of the lack of/difficulty of this link.
Fidelity card - loyalty card. why? first is to increase customer loyalty. More importantly, to gain customer knowledge on items they buy, sequence of choosing things, This helps companies to organize, change layout of the market, marketing campaigns such as specific offers for customers of different tastes, budgeting.
Systems: CRMS (customer relationship management system) BI (business intelligence systems)
Buying IT resources - approach: info has to be treated like ppl. like ppl, selection process, trading process, outplacement process (HR management).
Buy IT vs manage IS
INFO is a RESOURCE
INFO needs to be MANAGED (proc, store, xchange)
IS is the SYSTEM that manages INFO
We assume info is always present, so it is always managed to some extent. Hence, IS that is good to some extent always exists. Change info to people. People always present, so to some extent they are managed, so exists a people system which is good to some extent. This assertion is questionable, you don't want good to some extent, you want perfect. This is obvious for a people system, but much less obvious for an IS.
Feedback - controlling, understanding
Processing - list/synthesize/select
Synthesize - graphicalize, tablelize, summarize etc.
Transfer - exchange
Processing procedures depend on characteristics/deadlines or user. More time to work, may require more detailed less synthesizing info. Therre is no good standard procedure, quality of procedure depends on the usefulness of the user. Also, organizational entity affects procedures. Eg, company says all info on individuals shd be stored on paper and never transfered in electronic form for privacy. Due to organizational rules, processes, even if provided by software vendor, cannot be standardized in some template.
eg. Meeting
Raw info before mtg, discussed and processed during mtg, finalized in report and reported to a decision-maker. Taking a company with dozens of mtgs per day, synthesizing contents of mtg may be expensive, so organization rule states report of meeting generated automatically by software.
Cloud Computing
Assignment:
Try to describe what cloud computing is, and what it is for.
Features
Cloud computing features:
- servers available over the internet
- no physical infrastructure (no capex on hardware and software)
- works as a service, pay per use, consumption billed per utility
- servers not left idle
- multi-tenancy allows sharing of resources, hence centralization of infrastructure (in places of lower cost), peak load capacity increased, and efficiency in utilization.
- security of data might improve through centralization of data
- easier to maintain
Uses
Other uses
Applications
Cloud services can include anything from calendar and contact applications to word processing and presentations. Almost all large computing companies today, including both Google and Microsoft, are developing various types of cloud services.
With a cloud service, the application itself is hosted in the cloud. An individual user runs the application over the Internet, typically within a web browser. The browser accesses the cloud service and an instance of the application is opened within the browser window. Once launched, the web-based application operates and behaves like a standard desktop application. The only difference is that the application and the working documents remain on the host's cloud servers.
What types of applications are available via cloud computing? Perhaps the best and most popular examples of cloud computing applications today are the Google family of applications—Google Docs, Google Calendar, Gmail, and the like. All of these applications are hosted on Google's servers, are accessible to any user with an Internet connection, and can be used for group collaboration from anywhere in the world. None of these apps require software to be downloaded and installed on a user's computer.
Cloud services offer many advantages to users. If the user's PC crashes, it doesn't affect either the host application or the open document; both remain unaffected in the cloud. In addition, an individual user can access his applications and documents from any location on any PC or portable device, via an Internet connection. He doesn't have to a copy of every app and file with him when he moves from office to home to remote location. Finally, because documents are hosted in the cloud, multiple users can collaborate on the same document in real time, using any available Internet connection. Documents are no longer machine-centric; instead, they're always available to any authorized user.
On the downside, web-based applications are typically less robust than their traditional software counterparts. For example, Google Docs offers far fewer formatting features than does Microsoft Word, which can be inhibiting to more sophisticated users. In addition, cloud services can only be accessed when a user has a live Internet connection; they're not suited for instances where no Internet connection is available.
Cloud storage
One of the primary uses of cloud computing is for offsite data storage. With cloud storage, data is stored on multiple third-party servers, rather than on the dedicated servers used in traditional networked data storage.
When storing data, the user sees a virtual server—that is, it appears as if the data is stored in a particular place with a specific name. But that place doesn't exist in reality; it's just a pseudonym used to reference virtual space carved out of the cloud. In reality, the user's data could be stored on any one or more of the computers used to create the cloud. The actual storage location may differ from day to day or even minute to minute, as the cloud dynamically manages available storage space. But even though the location is virtual, the user sees a "static" location for his data—and can actually manage his storage space as if it were connected to his own PC.
Cloud storage has both financial and security advantages over traditional storage models. Financially, the cloud's virtual resources are typically cheaper than dedicated physical resources connected to a personal computer or network. As for security, data stored in the cloud is secure from accidental erasure or hardware crashes, because it is duplicated across multiple physical machines; because multiple copies of the data are kept continually, the cloud continues to function as normal even if one or more machines go offline. If one machine crashes, the data is duplicated on other machines in the cloud.
That said, the ultimate reliability and security of cloud storage is yet to be determined. While companies offering cloud services tout their security features, there are many stages in the process where security could be breached, just as with a traditional network. And access to your data could be compromised if the cloud storage provider has a service outage or goes out of business—both of which have happened in recent months. It may be too early in the adoption process to recommend that a company store its data exclusively in the cloud, without some sort of traditional physical backup.
Cloud computing
Cloud - metaphor used to represent the internet in a cloud drawing, with its networks in the "cloud"
"collection of computers and servers that are publicly accessible via the Internet."
Wiki def: "a computing capability that provides an abstraction between the computing resource and its underlying technical architecture (e.g., servers, storage, networks), enabling convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction."
Other def: "a large group of interconnected computers that typically extends beyond a single company or enterprise. The applications and data served by the cloud are available to a broad group of users using different operating system platforms; access is via the Internet."
5 characteristics: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service.
Internet integration
Internet integration
The integration of cloud-based services is in its early days. OpSource, which mainly concerns itself with serving SaaS providers, recently introduced the OpSource Services Bus, which employs in-the-cloud integration technology from a little startup called Boomi. SaaS provider Workday recently acquired another player in this space, CapeClear, an ESB (enterprise service bus) provider that was edging toward b-to-b integration. Way ahead of its time, Grand Central -- which wanted to be a universal "bus in the cloud" to connect SaaS providers and provide integrated solutions to customers -- flamed out in 2005.
Today, with such cloud-based interconnection seldom in evidence, cloud computing might be more accurately described as "sky computing," with many isolated clouds of services which IT customers must plug into individually. On the other hand, as virtualization and SOA permeate the enterprise, the idea of loosely coupled services running on an agile, scalable infrastructure should eventually make every enterprise a node in the cloud. It's a long-running trend with a far-out horizon. But among big metatrends, cloud computing is the hardest one to argue with in the long term.
Service commerce platforms
Service commerce platforms
A hybrid of SaaS and MSP, this cloud computing service offers a service hub that users interact with. They're most common in trading environments, such as expense management systems that allow users to order travel or secretarial services from a common platform that then coordinates the service delivery and pricing within the specifications set by the user. Think of it as an automated service bureau. Well-known examples include Rearden Commerce and Ariba.
MSP
MSP (managed service providers)
One of the oldest forms of cloud computing, a managed service is basically an application exposed to IT rather than to end-users, such as a virus scanning service for e-mail or an application monitoring service (which Mercury, among others, provides). Managed security services delivered by SecureWorks, IBM, and Verizon fall into this category, as do such cloud-based anti-spam services as Postini, recently acquired by Google. Other offerings include desktop management services, such as those offered by CenterBeam or Everdream.
Platform as a service
Platform as a service
Another SaaS variation, this form of cloud computing delivers development environments as a service. You build your own applications that run on the provider's infrastructure and are delivered to your users via the Internet from the provider's servers. Like Legos, these services are constrained by the vendor's design and capabilities, so you don't get complete freedom, but you do get predictability and pre-integration. Prime examples include Salesforce.com's Force.com, Coghead and the new Google App Engine. For extremely lightweight development, cloud-based mashup platforms abound, such as Yahoo Pipes or Dapper.net.
Web services in the cloud
Web services in the cloud
Closely related to SaaS, Web service providers offer APIs that enable developers to exploit functionality over the Internet, rather than delivering full-blown applications. They range from providers offering discrete business services -- such as Strike Iron and Xignite -- to the full range of APIs offered by Google Maps, ADP payroll processing, the U.S. Postal Service, Bloomberg, and even conventional credit card processing services.
Utility computing
Utility computing
The idea is not new, but this form of cloud computing is getting new life from Amazon.com, Sun, IBM, and others who now offer storage and virtual servers that IT can access on demand. Early enterprise adopters mainly use utility computing for supplemental, non-mission-critical needs, but one day, they may replace parts of the datacenter. Other providers offer solutions that help IT create virtual datacenters from commodity servers, such as 3Tera's AppLogic and Cohesive Flexible Technologies' Elastic Server on Demand. Liquid Computing's LiquidQ offers similar capabilities, enabling IT to stitch together memory, I/O, storage, and computational capacity as a virtualized resource pool available over the network.
SaaS
1. SaaS
This type of cloud computing delivers a single application through the browser to thousands of customers using a multitenant architecture. On the customer side, it means no upfront investment in servers or software licensing; on the provider side, with just one app to maintain, costs are low compared to conventional hosting. Salesforce.com is by far the best-known example among enterprise applications, but SaaS is also common for HR apps and has even worked its way up the food chain to ERP, with players such as Workday. And who could have predicted the sudden rise of SaaS "desktop" applications, such as Google Apps and Zoho Office?
Internet
Internet is a communication channel for things
Hardware:
Pallet + RFID tag + microsensor
--
Router
--
Pallet + RFID tag + microsensor
eg. RFID tag on carrot (certain temp wanted consistently), sensor takes temperature of carrot
hence, sensor takes information in a smart way on the environment about a target item
eg. accelerator-monitor - used in car airbags, robots
Things that can take decisions completely independently from the presence of human beings
Strat <--> strat partnership <--> strat (Co-opetition)
Companies <--> co-laboration/co-operation <--> companies/clients
Competition - either you increase market share, or increase market size and keep market share. So now many companies, some areas compete, some areas co-operate.
Enablers - enable processes, whether wanna do the process or not is another thing. necessary conditions but not sufficient conditions
Marketing guerrila - strategy. using platforms like blogs or facebook that can provide information about products like covering damage by adding information
Summary of Readings
8 Biz Tech Trends
Article precinct:
Economic value is created when technology is combined with new ways of doing business.
C) Leveraging info in new ways
7. Putting more science into management
- exploit info explosion with diverse set of management techniques
8. Making businesses from information
- info-based biz opportunities
- advantage: reduce problem of info assymetry, inability to obtain data
B) Managing capital and assets
5. Expanding the frontiers of automation
- automate processes
- many processes stil unautomated
- advantages: lower costs and improve time-span of customers obtaining what they want
- disadvantages: challenge of finding right balance between raising profit margins and keeping customers happy
6. Unbundling production from delivery
- breaking down of processes into smaller segments with accurate measuring and metering use of each to result in effective allocation and capacity planning
A) Managing relationships
1. Distributing cocreation
- outsourcing various functions to business networks
- decentralized innovation good for software and editorial content
- advantages: lower production costs
- disadvantages: lost of creative control and intellectual property
2. Using consumers as innovators
- eg. Wiki
- eg. Threadless
- advantages: better insight into customer needs and behavior
- disadvantages: might be influenced by vocal minority, focused on long-term rather than immediate needs of customers
3. Tapping into a world of talent
- decentralize work to specialists, free agents, talent networks
- made less costly by internet etc.
- new talent-development models emerge
- new pricing models
- might be popularised in segmentable industries
- competitive advantage to companies able to breakdown and recompose tasks
4. Extracting more value from interactions
- advantage: efficiency increases
- disadvantages: creating right incentives for employees
5 Commandments
5. Wirth's law
Wirth's law: Software is slowing faster than hardware is accelerating
- 1995
- accusation on microsoft: as speed of calculation increases, amount of calculation needed per function increases, resulting in less gains for user
- "feature bloat": inflated software features unusable if not for hardware advances
- tolerated bcoz i) embarassment of computer riches ii) consumers' inability to discern useful and uselessness despite influence on software design
- root cause argued as caused by software companies
- programmes don't require massive manuals, but if they do, keep clients in the long haul
- competitive pressure prevents meticulous pruning of software design
4. Metcalfe's law
Metcalfe's law: network value grows proportionately to no. of users squared
- 1993
- eg. telephone value increases per user
- not all "users" add value, some contaminate, eg. cold calling, spam emails
- 4 probs of networks: saturation, cacophony, clustering & search
i) saturation: valuable information saturated
ii) cacophony: too complex interplay btwn members eg. forums
iii) clustering: users only in parts of network, end up communication with each other
iv) search: riches of network remain inaccessible in practice
- solutions to probs: recruit new members with valuable assets, combat clustering thru deliberate subdivision of units, filter to combat saturation
- not as practically true as Metcalfe's law
3. Machrone's law
Machrone's law: the pc u wanna buy will always be $5k
- 1984
- statistics show approximate fixed price ranges per time period of approximately a decade
- total pc sales revenue continue to increase despite falling unit costs due to factors such as usage for online services
2. Rock's law
Rock's Law: Cost of semiconductors x2 every 4 years
- mid 1990s
- actual: 1980s - fabs increased yield, 1990s - increasing throughput (rate of production) 2000s - increasing throughput
- cost not impt, more impt is value of product
- essentially rate of production has increased with economies of scale
- resulting in changes in prices of PCs -> Machrone's law
1. Moore's law
Moore's law: No. of transistor chips x2 annually
- 1965
- no tech barriers to tech advancements, trend will continue
- basis: cost per elec. component inversely proportional to no. of elec. component in simple circuits
- implies econ limit to tech longevity
- yield rate (ie. monetary returns to semiconductor producers from chips produced) will eventually reach a point of econ constraint
- econ end but not tech end
- no exponential trend lasts forever? arguable, i.e. postponement
- semiconductors at least 15 years from now. might move on to nanotech
- legal status: does law describe reality or create it?
- hence, econ basis means law comes down to Rock's law of fabrication costs of semiconductors
Aurelio says
NEW hardware performance --> NEW faster applications and features --> for OLD activities, need to innovate,
HENCE,
Moore’s law exists because new transistors are required those who require /or produce faster transistors, by all industries.