a Jennifer Ryan 12 éve
475
Chapter 11
The document discusses various aspects of computer crime and information technology security, emphasizing the importance of protecting digital assets from a wide range of threats. It outlines common risks like malicious software, fraud, and denial-of-service attacks, and underscores the necessity for robust security measures.
Megnyitás
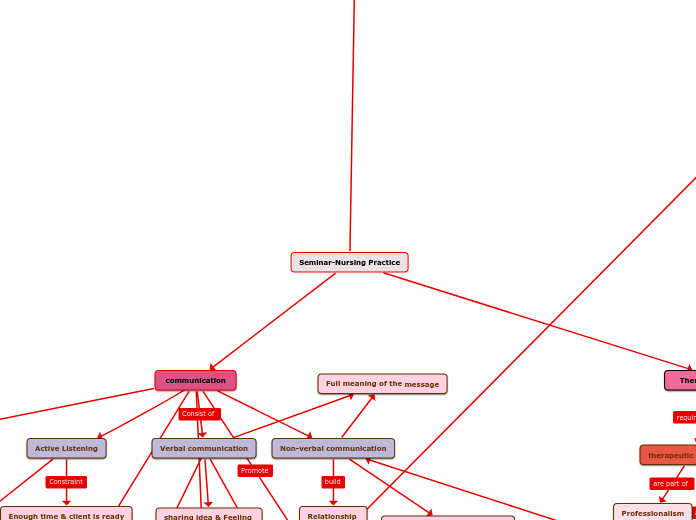
Computer Crime and Information Technology Security Risks and Threats Extortion Web site defacements Denial-of-service attacks Malicious software Information maniputlation Information theft Intrusions Disclosure of confidential information Service interruption and delays Error Fraud CoBIT Accountability Framework Audit committee External audit Internal audit IT and information security management Board of Directors Stakeholders 7 information criteria Reliability of information Compliance Availability Integrity Confidentiality Efficiency Effectiveness Perpetrators of Computer Crime Insiders Terrorists Corporate spies Organized crime Cyber-criminals Hackers Script kiddies Information Security Technical security controls antivirus software access control software encryption firewalls Administrative security controls security reviews and audits adequate superision of employees security awareness and training security policies and procedures Physical security controls alarms badges security guards locks Basic principles availability data integrity confidentialtiy