jonka Jennifer Ryan 12 vuotta sitten
473
Chapter 11
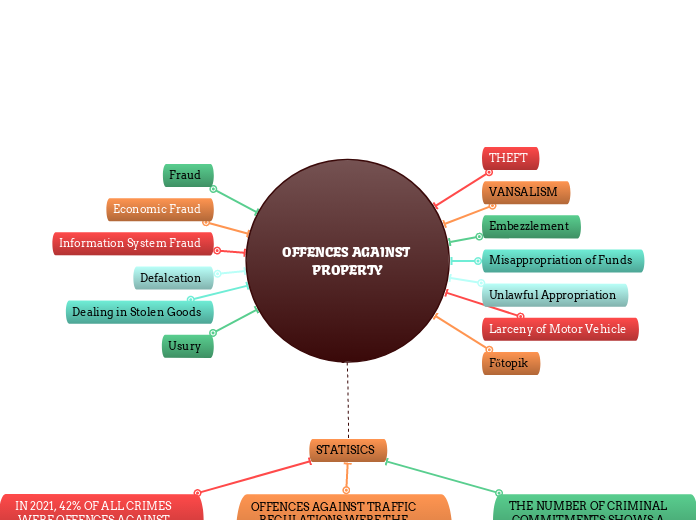
The document discusses various aspects of computer crime and information technology security, emphasizing the importance of protecting digital assets from a wide range of threats. It outlines common risks like malicious software, fraud, and denial-of-service attacks, and underscores the necessity for robust security measures.