によって Salvatore La Rosa 1年前.
205
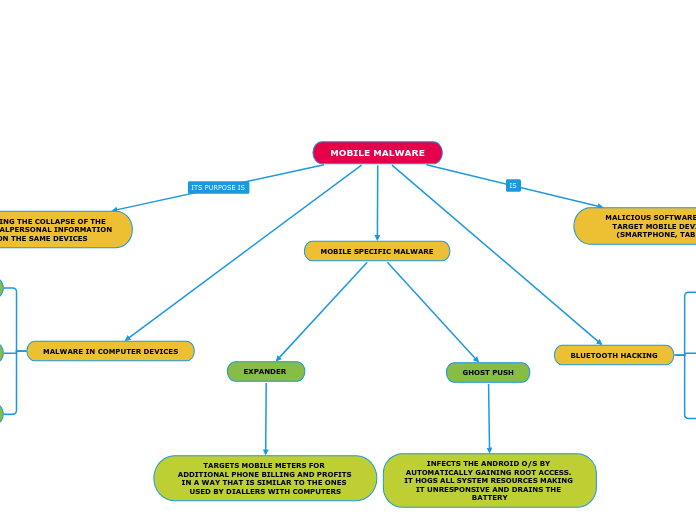
MOBILE MALWARE
Malicious software specifically targeting mobile devices such as smartphones, tablets, and PDAs can come in various forms. One example is Ghost Push, which infects Android operating systems by gaining root access, consuming system resources, and draining the battery.