Authentication Mind Maps - Public Gallery
Explore our wide public collection of authentication mind maps created by Mindomo users all over the world. Here, you can find all public diagrams related to authentication. You can view these examples to get some inspiration. Some diagrams also give you the right to copy and edit them. This flexibility allows you to use these mind maps as templates, saving time and giving you a strong starting point for your work. You can contribute to this gallery with your own diagrams once you make them public, and you can be a source of inspiration for other users and be featured here.

Routings
by CCNA CCNA


CISSP: Access Control Systems and Methodology
by Walkowska Anna

MicroServices
by Mike Ton

Virtual Private Netw
by sihui lau

IT Security Terms
by Usama Amin


MS302-303 Section 1: Planning Network Infrastructure
by James Herbert

wireless LAN vulnerabilities
by nursyafeera azeera

TPM (TimUR Performance Management)
by Alfiah Khoirunisa

Authentication inter-operability FreeIPA / AzMan
by ericdes (Eric)

Edgar Collins and the new Cezanne
by kinda tarek

Remote Access
by sihui lau

A Paul Cézanne painting
by ALi Abd El-Latif

Auth
by Ivan Kayzer

Authentification/De-authentifiction of Artwork
by Olivia Quinn


Classwork # 8
by Darya Fatih

5c
by soha osman

iis
by Behnam shiri

MS301 Obj 6. Implementing, Managing, and Troubleshooting Network Protocols and Services
by James Herbert

Sample Mind Map
by Octavio Hernandez

BangAli
by Yovi Oktofianus

AD Polling Mode
by Nestor Catacora


Access Contol
by Kenneth Gourlay

As Light Meets Matter: Art Under Scrutiny
by Dalia Kamar

As Light Meets Matter: Art Under Scrutinity
by Farah Anwar

Virtual Private Netw
by sihui lau

Assi 4a
by Khaled Mohsen

Mental Health
by Suresh kumar Mukhiya

YS
by Ken Reid

AD, OD and Cent Workflow
by Cheryl Lynn

El Paseo Web-App
by Geraldine Davila


InfrastructureSecurityComponents
by Iben Rodriguez

Processing
by Taibi Aymane

Authenticating Famous Works of Art
by Clarissa Pharr
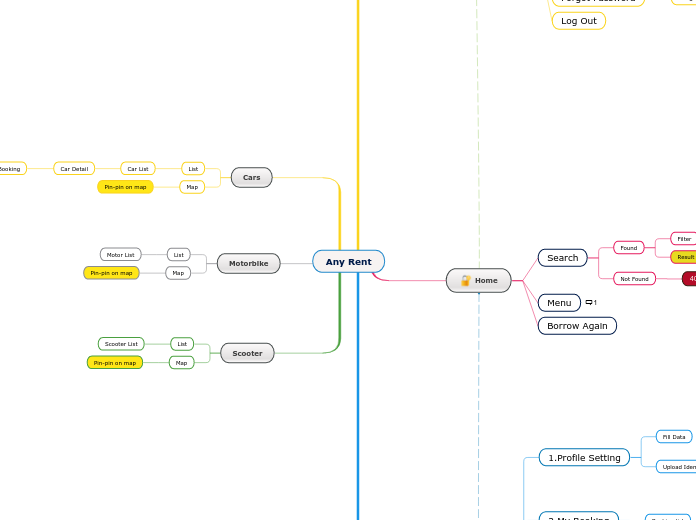

Any Rent
by Syahdan Hidayat
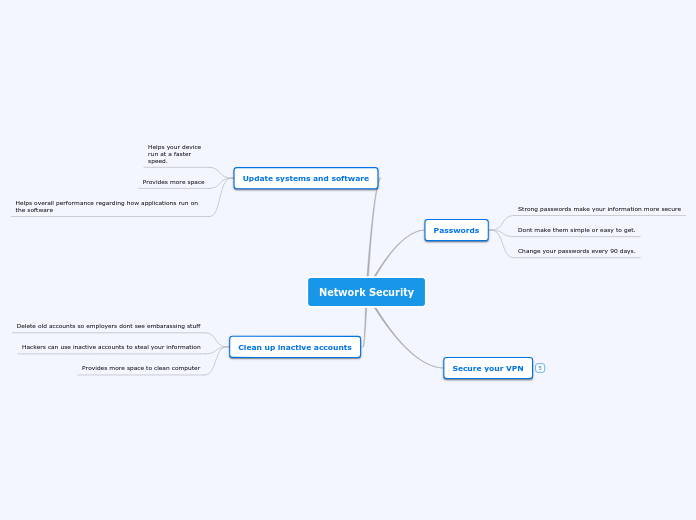

Network Security
by Jake Kilgore

Sample Mind Map
by lama hazaa

Art under scrutiny
by Noha Marei
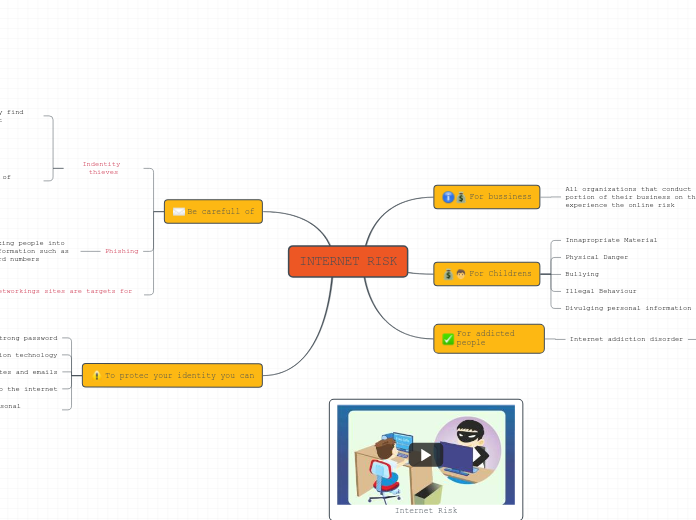

INTERNET RISK2
by Shakirs Franco
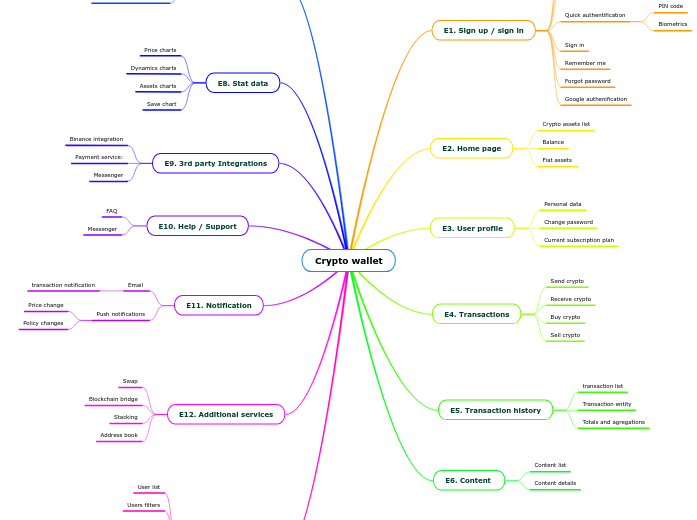

Crypto wallet
by Volodymyr Ponomarenko
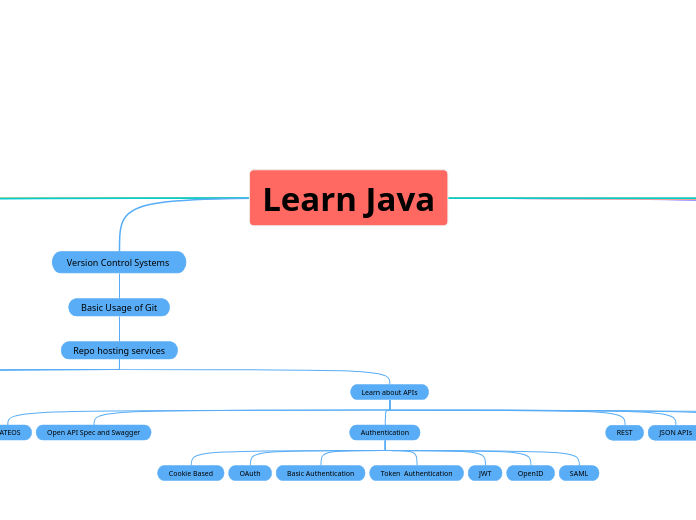

Learn Java
by Артур Базанов
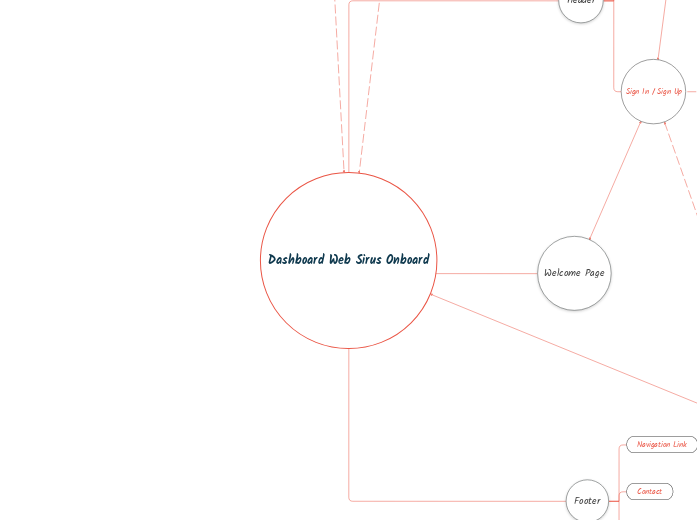

Mind Map Projek Onboard Sirus
by Aditya Wibowo
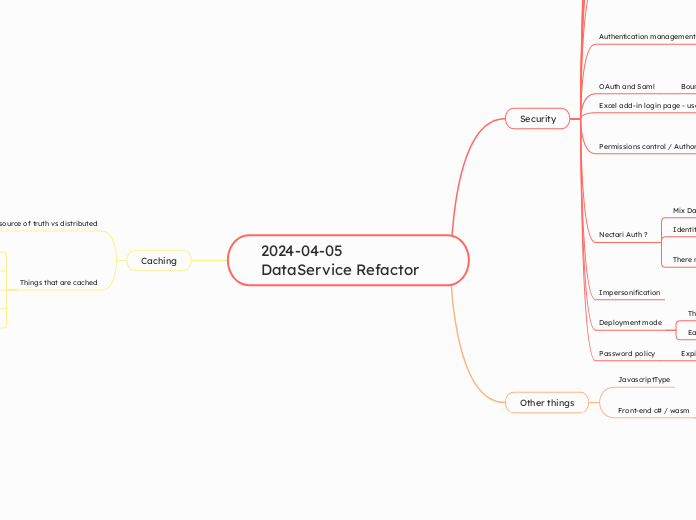

2024-04-05 DataService Refactor
by Samy Sarem
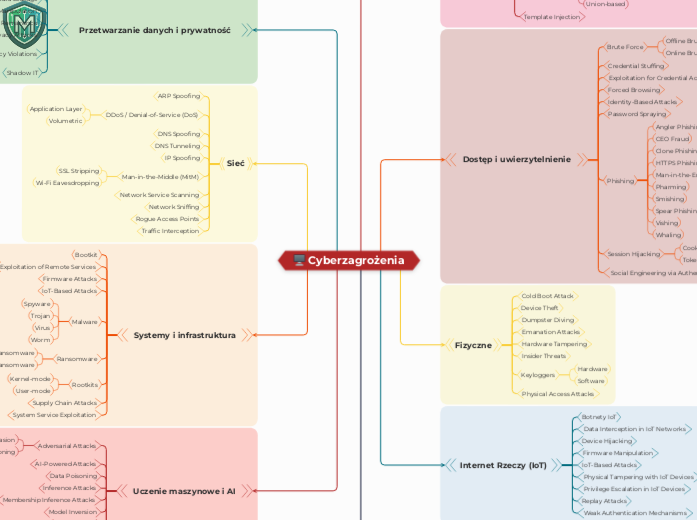

Cyberzagrożenia
by dr inż. Michał Malinowski
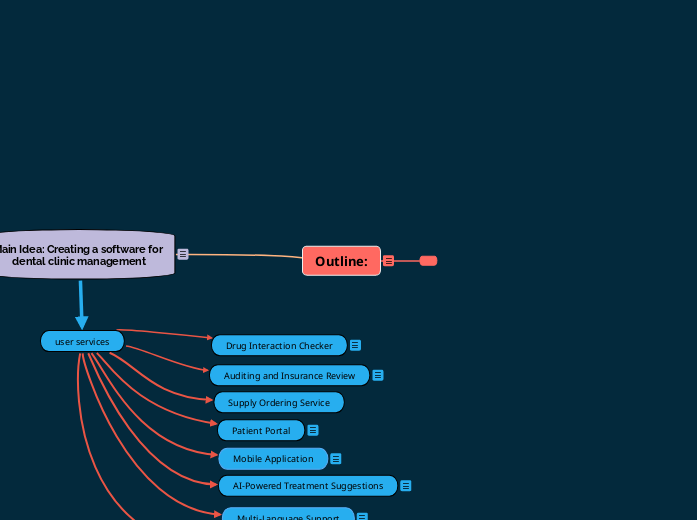

Outline: - Copy
by code clinic
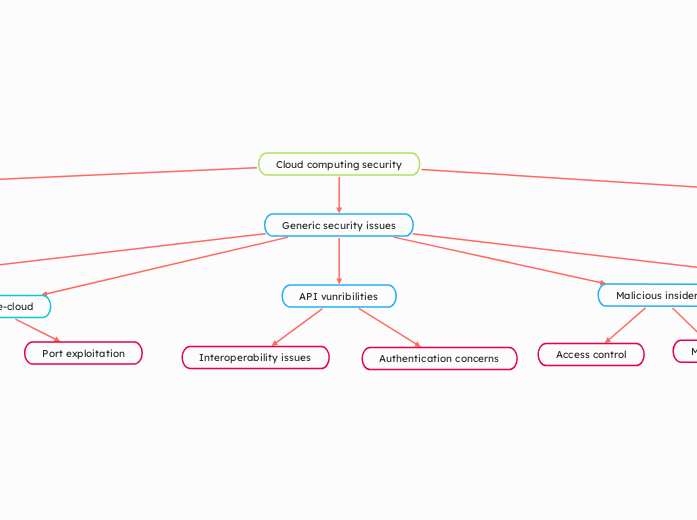

Cloud computing security
by Jack Barnes



