Security Mind Maps - Public Gallery
Explore our wide public collection of security mind maps created by Mindomo users all over the world. Here, you can find all public diagrams related to security. You can view these examples to get some inspiration. Some diagrams also give you the right to copy and edit them. This flexibility allows you to use these mind maps as templates, saving time and giving you a strong starting point for your work. You can contribute to this gallery with your own diagrams once you make them public, and you can be a source of inspiration for other users and be featured here.

Yin's Mid-Term Memory
by Yin Wang


The United Nations Organization
by Verene Snopek


AWS Well-Architected Framework
by Yasser Moghrabiah
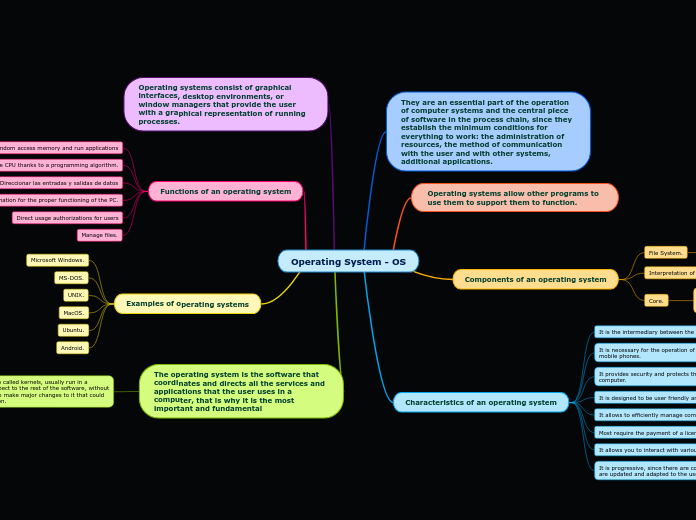

Operating System - OS
by Jesus Anelio Reyes Azuero
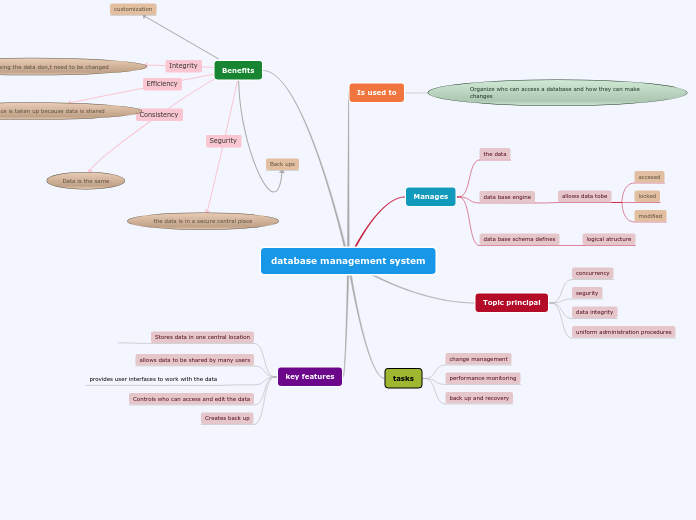

database management system
by Miguel eduardo racine soto
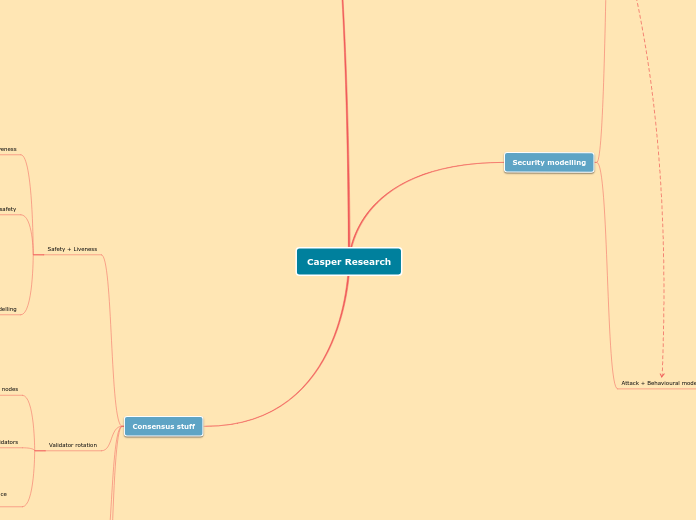

CasperResearch
by Vlad Zamfir

Cryptography
by Robert Mccausland

ICT Department Organogram
by Jason Oliver

Google GCP ACE-2019
by Simon Erses

Sainsburys1
by David Mills

Chapter 2 The Saber-Tooth Curriculum
by Julie Morris
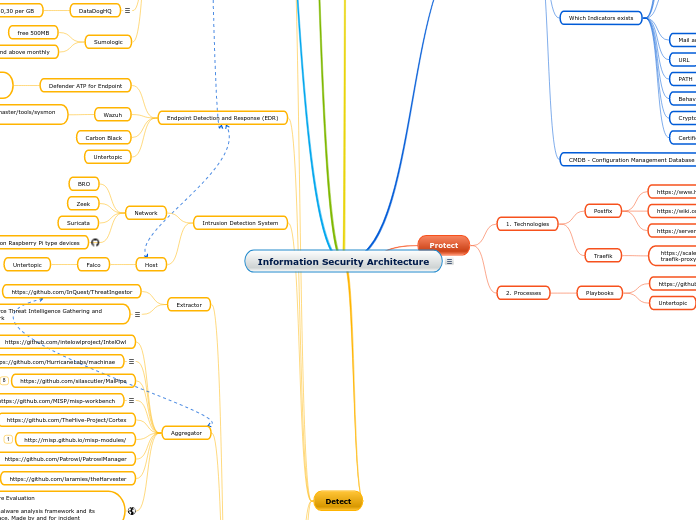

Information Security Architecture
by Cyber Threat

Windows 8
by vidhyadhar pandit

MS302 - 303 Section 2: Active Directory
by James Herbert
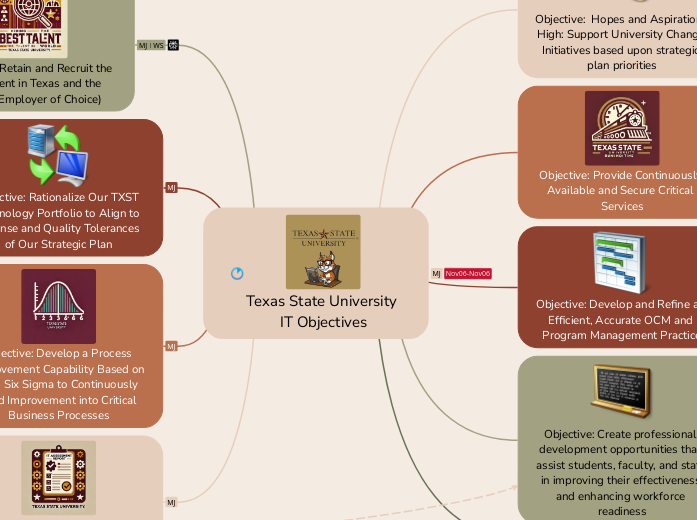

Texas State University IT Objectives
by Matthew Jett Hall

Map IEC/ISO 27001:2013 Annex A - English
by Grandt Grandt

coll 100 concept map
by Luis Leon
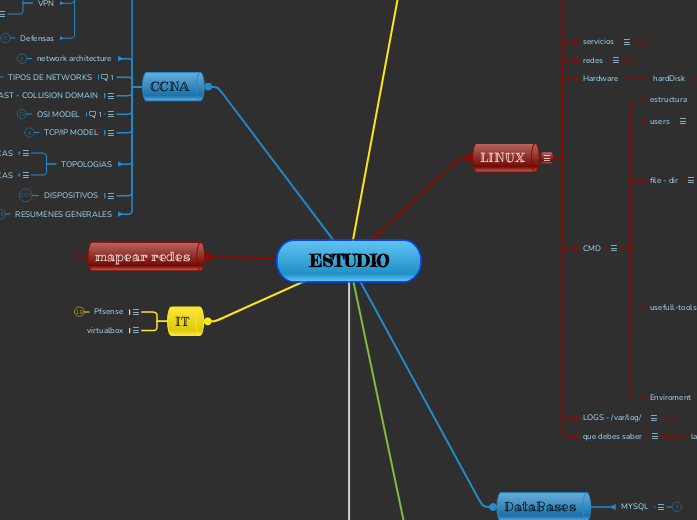

ESTUDIO
by humberto garcia

Service Desk
by wh tang
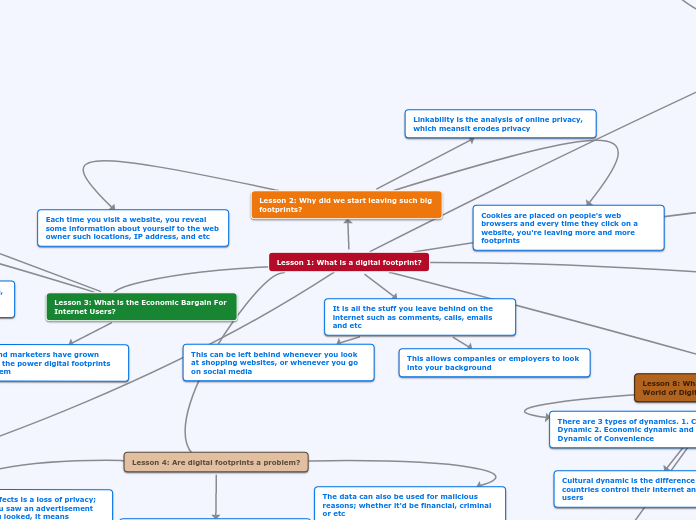

Lesson 1: What is a digital footprint?
by Summer Ly

wireless Network security
by nursyafeera azeera

Network Security
by Clint Groves

Layered Application
by Daniel Sima


RESP-Reverse Engineering For Security Professionals
by Content Admin

Risk Society
by Meredith Gore


9 Elements of Digital Citizenship!
by Kristin Dattoo


Unit: Urbanization & Urban Agriculture
by rebecca fisher

Freight Transport
by Sorawit Yao

9 Elements of Digital Citizenship
by Zef Shkambi

Access Controls
by Robert Mccausland

bios
by ESME GOMEZ

A.I. - Artificial Intelligence
by Jonathan Cook

The United Nations
by Nolan Philipps

Security Architecture and Design
by Robert Mccausland
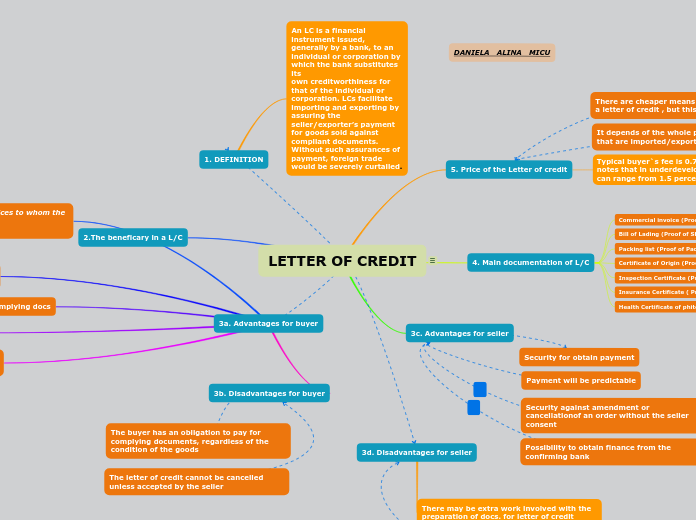

LETTER OF CREDIT
by Alina Micu

Browser Fuzzing
by Huy na

TOP CASINOS 100% SAFE
by James Taylor

Terrorism
by Johanna Lai


Nairobi, Kenya
by sara crisafulli

ITGS 2012 Exam Prep
by Magda Johnson

Smart City
by Khaldoun Mohsen

HanaTopicsOverview
by Prathap Reddy
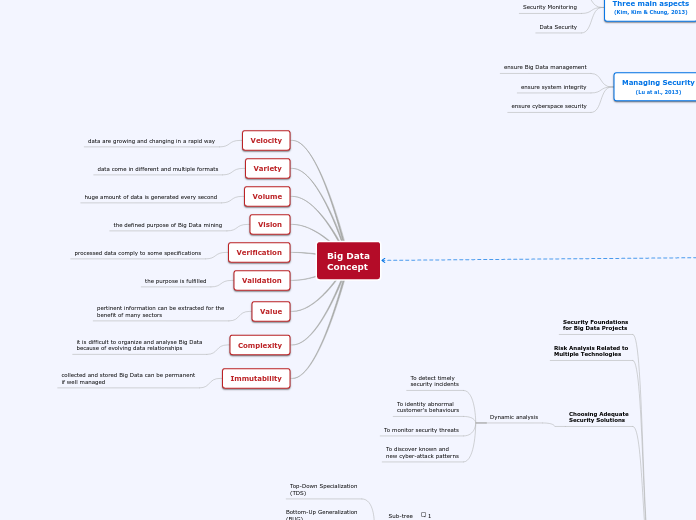

Big data security
by Tânia Esteves
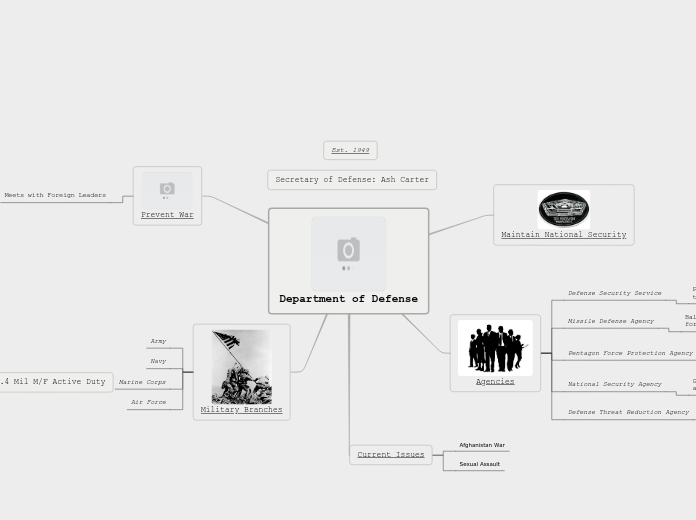

Department of Defense
by Mason Macias

Kaspersky
by Артём Бардин


MS302-303 Section 1: Planning Network Infrastructure
by James Herbert

Holography
by Matthew Ku
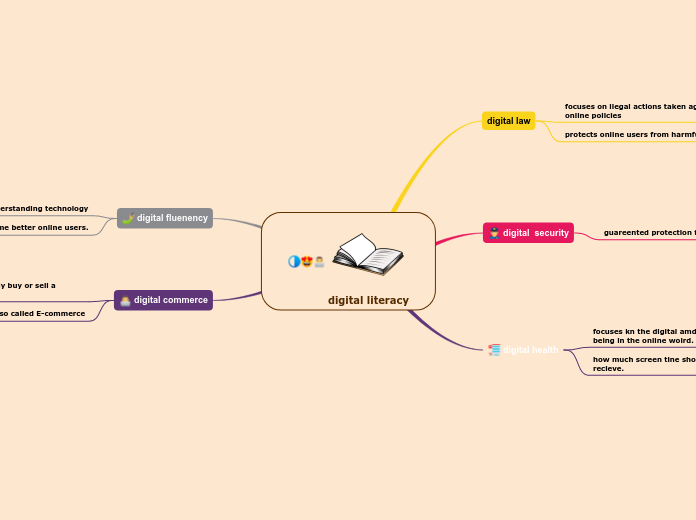

digital literacy
by Nook Bradford

Карта
by Sofia Jermakova

Middleware
by Justin Meyers
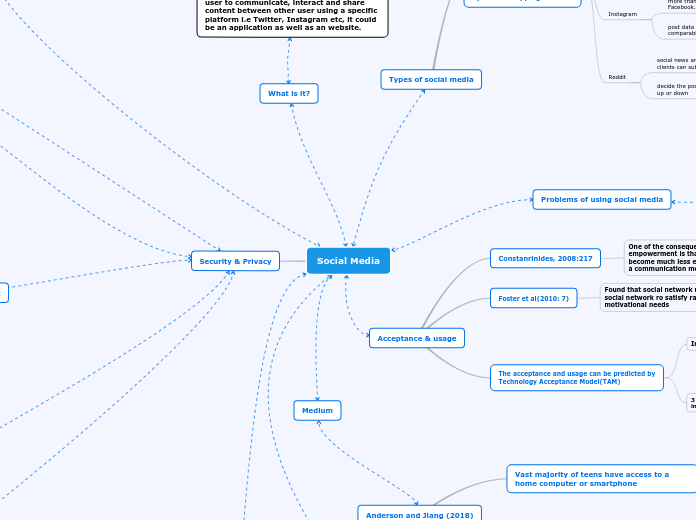

Social Media
by HAJI MUHAMMAD AZRI HAJI MUHAMMAD AZRI

Elements of a Digital Citizenship
by Gregory Gerbal

My knowledges & skills
by Weiyan Lin

Security and Encryption - Revision
by Jarod Farrer
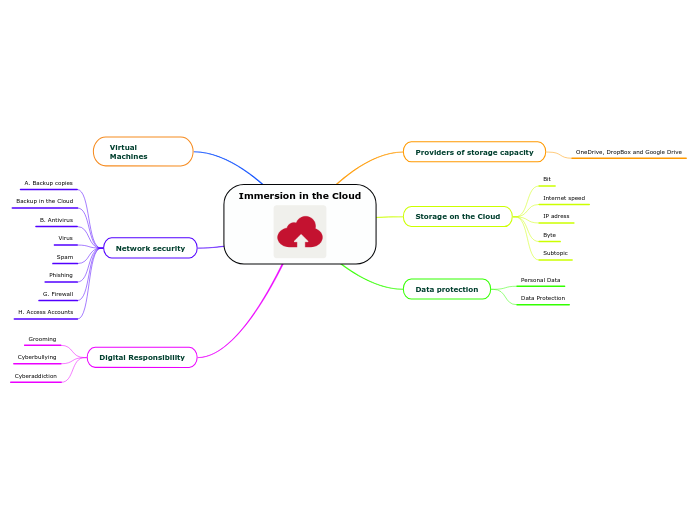

Immersion in the Cloud
by miranda cervantes

Command Economy
by Logan B
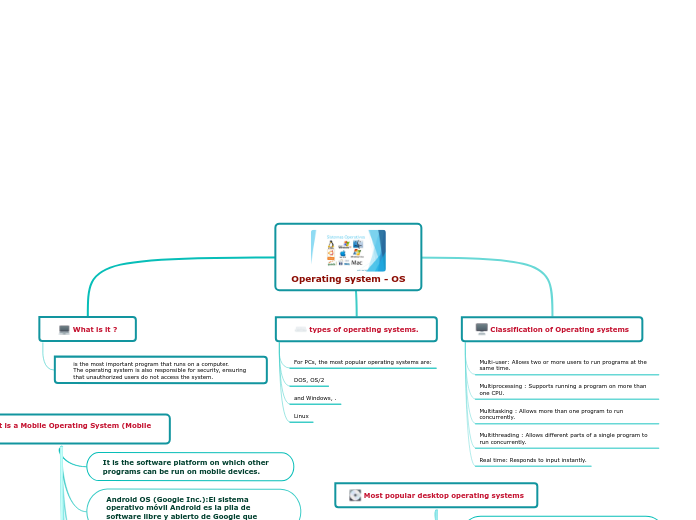

Operating system - OS
by luis brayan tandayamo imbaquingo
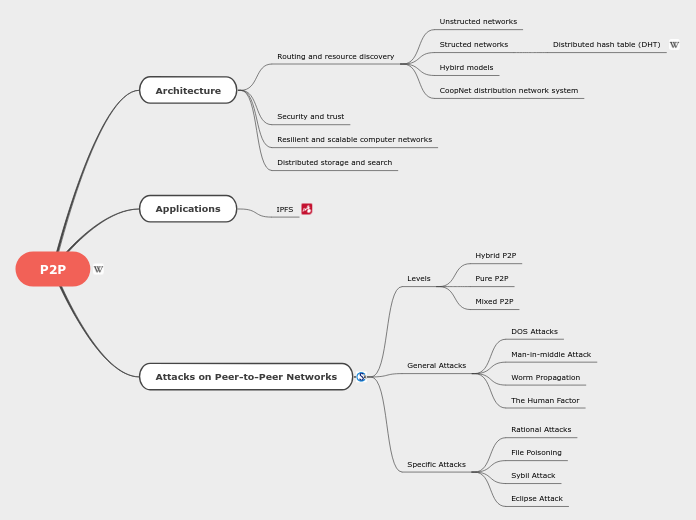

P2P
by Yu Wang

BOGOTÁ
by Camila Lee
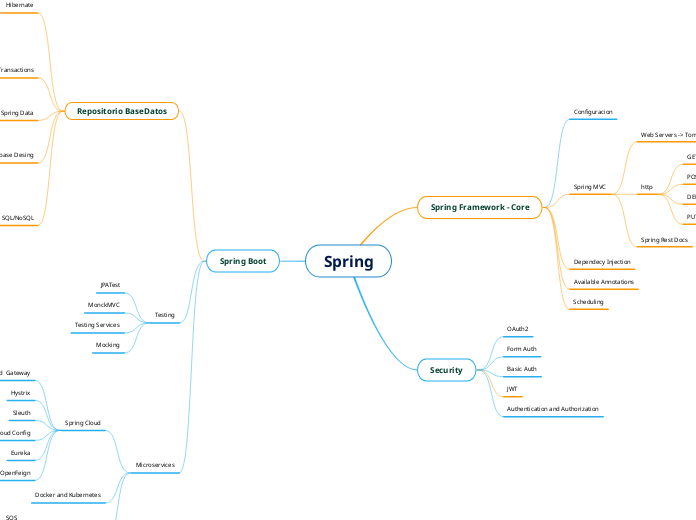

Spring based on amigoscode.com
by Omar Velez

ICT Portfolio
by Jason Oliver

IMPORTANT THINGS TO BOGOTA
by diana torres

EXPAT
by Boo OoB

Odoo Support Scope of Requirements
by Anthony Gardiner

Authentication inter-operability FreeIPA / AzMan
by ericdes (Eric)

ASSIGNMENT 3.1 Defending North America
by taylor h


Nine Elements
by Daniel Lionti

Self-Service Checkout
by Alex Webster

6420A Fundamentals of Windows Server 2008 Network and Application Infrastucture
by maya sh


Kiosk
by Pat Witt

Android apps that we use and like
by Daniel Sima

British Welfare State
by patricia.martinez Jones

The Book Theif - Hans Hubermann
by esha mann


DCP Innovation
by kurt ahrens

Internet Economics
by Josh Polterock

Privacy and Security
by Andrea Perez

Internet Marketing Niches
by Madhu Rai

Global Security
by joe walker
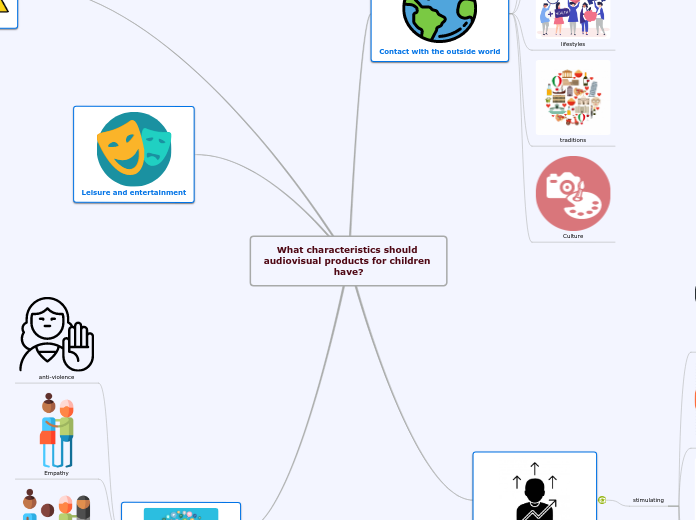

What characteristics should audiovisual products for children have?
by isabel lomas

mnnclub.net
by Ji Hyeonho

Command Economy
by Katarina P

Economic System
by Amanda Huston

Event-Driven Player Search - Mind Map
by Paulo Jesus

Internet 2E2
by Peggy Lim

servientrega
by canal de aprendizaje

CSILM Navigation
by Udara Weerakoon
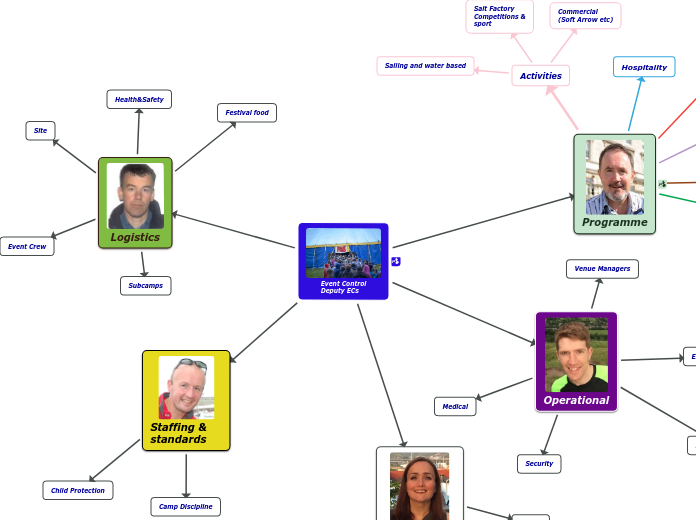

Org Chart 2019
by John Kee
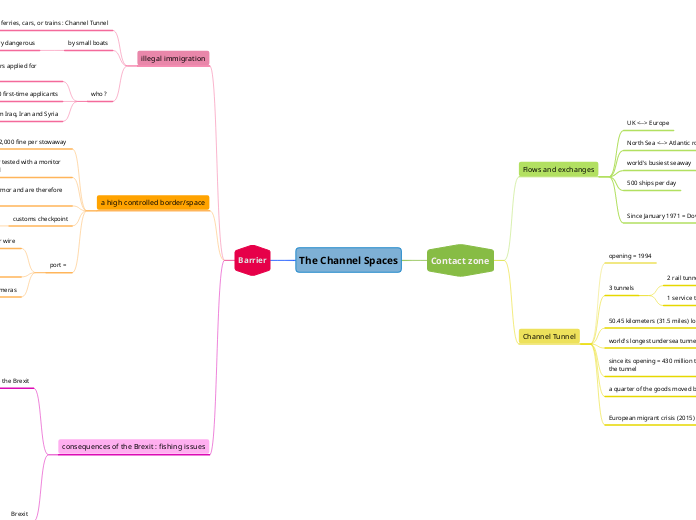

The Channel Spaces
by ELODIE THEDENAT

EE²
by Niccolò Sessa

Adobe Connect
by Alistair Lee

Planning of the opening and closing ceremonies of the 2012 Olympics
by Christine Eikeberg

Airbus
by Olivier Pfeiffer

How did people in singapore show unhappiness to British
by Joyce Lee


RISKS ON THE INTERNET
by Eike Berroci

chapter 1
by Ziryan Shorsh

tech neologisms
by Varvara Moskaliuk

Mind Map
by Hutchinson Hutchinson

Fall 2013 Konkol
by Charles Konkol

ECDL
by aleksandr boiko


IT for Managmers
by Niaz Aziz Ali



