av CAITLYN KNIGHTS 3 år siden
209
Digital Forensics
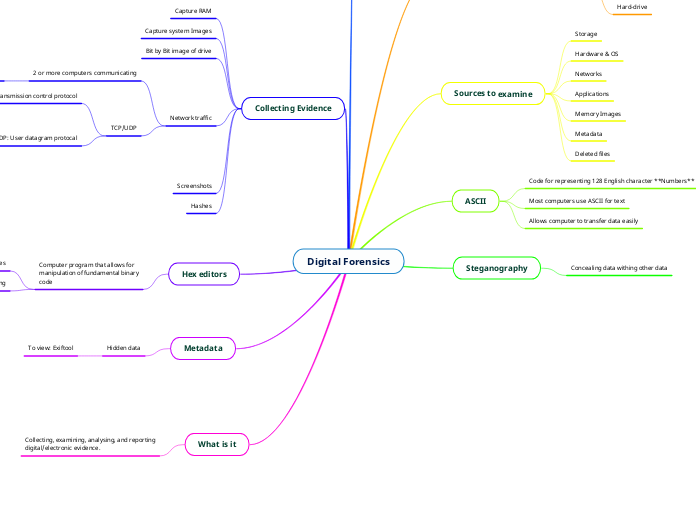
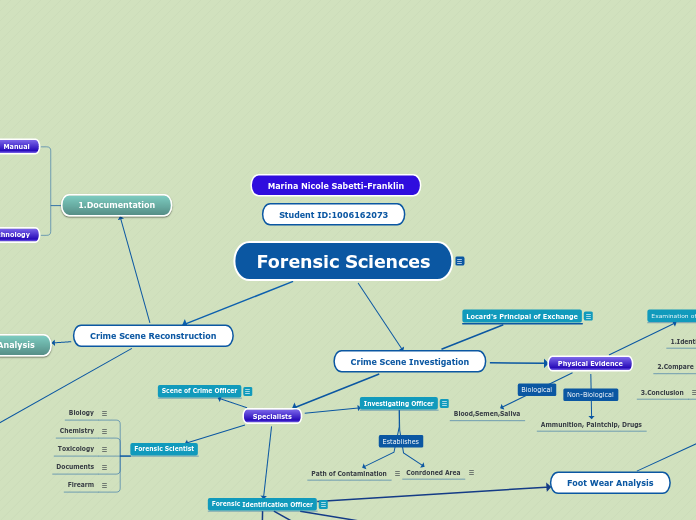
Digital forensics involves the collection, examination, analysis, and reporting of digital and electronic evidence. Tools like Wireshark, a protocol analyzer, help in recording and analyzing network traffic by capturing packets, the fundamental units of data transfer over a network.