Big Data
Security
Security Solutions
Security Surveillance
and Monitoring
dynamic analysis of security
events
Security Information and Event
Management (SIEM)
Data Loss Prevention
(DLP)
Data Confidentiality and
Data Access Monitoring
Centralized Security
Management
Data Cryptography
Cloud Background Hierarchical
Key Exchange (CBHKE)
Homomorphic Cryptography
Anonymization of Confidential
or Personal Data
Models for data
anonymization
l-diversity
k-anonymity
m-invariance
t-closeness
Sub-tree
Lack of Performance
Cannot scale when applied to anonymize Big Data on distributed systems.
Hybrid approach
(TDS + BUG)
Provides efficiency, performance and scalability required to anonymize huge databases
Bottom-Up Generalization
(BUG)
Top-Down Specialization
(TDS)
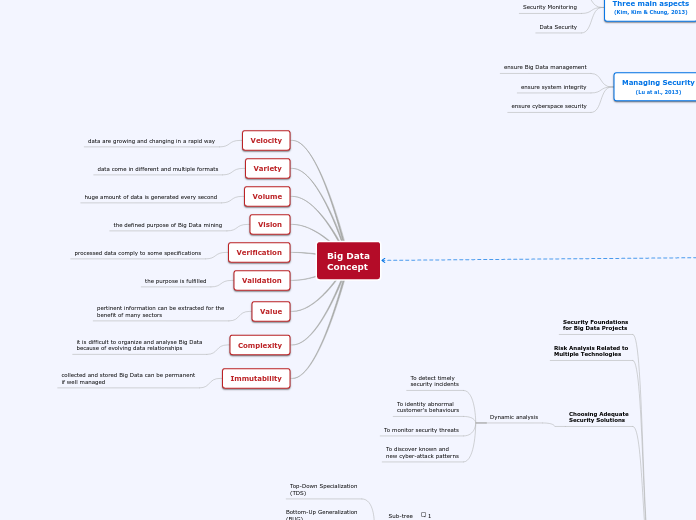
Choosing Adequate
Security Solutions
Dynamic analysis
To discover known and
new cyber-attack patterns
To monitor security threats
To identity abnormal
customer's behaviours
To detect timely
security incidents
Risk Analysis Related to
Multiple Technologies
Security Foundations
for Big Data Projects
Managing Security
(Lu at al., 2013)
ensure cyberspace security
ensure system integrity
ensure Big Data management
Three main aspects
(Kim, Kim & Chung, 2013)
Data Security
Security Monitoring
Information Security
aims to ensure
a generation of security performance indicators
a robust protection of confidential information
a granular role-based access control
a real-time monitoring to detect vulnerabilities,
security threats and abnormal behaviours
Security Challenges
Big Data Security on Social Networks
Detect rapidly abnormal patterns and
ensure a real-time monitoring of
alarming events
Can prevent terrorist and security
attacks and assess citizens' satisfaction
regarding public services
Need of Big Data Experts
need for advanced security analysis experts
(Constantine, 2014)
Compliance to Security
Laws Regulations and Policies
Big Data analytics may be in conflict
with some privacy principles.
Deal with multiple laws and regulations
(Tankard, 2012)
Information Reliability
and Quality
Data have to be filtered, organized and
contextualized before performing any analysis
It is difficult to assess the authenticity and
integrity of all various data sources
It is important to verify Big Data sources
authenticity and integrity before analysing
data
Compatibility with Big
Data Technologies
It is mandatory to verify their compatibility
with organization Big Data requirements and
existing infrastructure components.
(Zhao et al., 2014)
some security techniques are incompatible
with commonly used Big Data technologies
(e.g.: MapReduce)
Data Anonymization
It is difficult to process and analyse anonymized
Big Data
Traditional anonymization techniques are based
on several iterations and time consuming computations
may slow down system performance
may affect data consistency
Should be achieved without affecting system
performance or data quality
New Security Tools
Lack of Maturity
Inadequate Traditional
Solutions
are not efficient
are time-consuming
slow the performance
e.g.: types of data encryption
Multiple Security
Requirements
There is a need to find a balance between multiple
security requirements, privacy obligations, system
performance and rapid dynamic analysis
Security tools should be flexible and easily scalable
To handle information security while managing
massive and rapid data streams
The Need to Share
Information
Data sharing associated with advanced
analytics techniques
Correlation attacks, arbitrary identification,
intended identification attacks, etc
Illegal access to network's traffics
Discovering confidential information
Multiple connections with different levels
of securities
Big Data Nature
Sharing data over many networks increase security risks
It is difficult to handle data classification and management
of large digital disparate sources
Adding security layers may slow system performances
and affect dynamic analysis
Big Data
Concept
Immutability
collected and stored Big Data can be permanent
if well managed
Complexity
it is difficult to organize and analyse Big Data
because of evolving data relationships
Value
pertinent information can be extracted for the
benefit of many sectors
Validation
the purpose is fulfilled
Verification
processed data comply to some specifications
Vision
the defined purpose of Big Data mining
Volume
huge amount of data is generated every second
Variety
data come in different and multiple formats
Velocity
data are growing and changing in a rapid way