NetBIOS
NETBIOS
●Name Registration 137 (TCP/UDP)
-Uses UDP Primarily for name resolution
●Datagram connectionless (UDP 138)
-Primarily used for Mailslots
●Connection-Oriented (TCP 139)
-Netbios over TCP
Get local NETBIOS Names
nbtstat
nbtstat –n
Hostname vs NETBIOS names
Netbios names = 16 characters with 15 visible, cannot be a part of domain and can use “_”
Domain names = 255 characters, can be static or manually assigned, and can use “-” instead of “_”
After BIOS or UEFI
CSRSS
- Client/Server Runtime Subsystem
- Client side of the Win32 subsystem process
- Thread creation.
WININIT
- Starts Service Control Manager (SCM)
- Starts Local Security Authority SubSystem (LSASS)
- Starts Local Session Manager (LSM)
SMSS
- Session Manager
- Session 0 loads Win23k.sys (kernel subsystem)
- Runs WININIT
HAL.dll
- Hardware Abstraction Layer (HAL)
- Interfaces driver & system to kernel
NTOSKRNL
- SYSTEM
- Prepares for running native system
- Runs SMSS
Malware Analysis
Dynamic Analysis
Examines Malware while it is running.
Wireshark
Reg Shot
TCPView
ProcMon
Static Analysis
Examines malware without executing it.
OSINT (Open Source Research)
Name/Hash check for existing information online.
OSINT framework focused on gathering information from free tools or
resources.-https://osintframework.com/
DLL's used/referenced in Strings Output
IDA Pro, OLEDebug
IDA is a Windows, Linux or Mac OS X hosted multi-processor disassembler and debugger that offers so many features it is hard to describe them all.
Strings
Bots & Zombies
Purpose
Bot herder can utilize the botnet to accomplish a task such as:
- Attack (DDoS)
- Computation (Password Cracking / Bitcoin Mining)
- Infection of additional systems.
- Obfusaction of traffice.
Methodology
- Payload is configured to infect the intended machines and delivered to the victim.
- Victim executes the payload, infecting the machine, and joining the botnet.
- Victim machine calls back to the bot herder's C&C server for additional instructions.
Zombies
Individual machine infected and part of the botnet.
Bot Herder
Person in control of the botnet.
Botnet
Multiple machines infected and controlled by a bot herder.
Malware Tools
Ransomware
Blocks access to a resource, requires payment from victim (Top threat currently).
Adware
Paid for ads to infect users device.
Spyware
Monitors behavior of user.
Botnet Client
Remote administration/Command and control of a botnet.
Keylogger
Records keyboard usage.
Rootkit
- Malcious program that is only used to hide things.
- Does not provide access or command and control alone.
Remote Access Tool (RAT)
Malicious program that provides remote command and control.
Backdoor
- Malicious program that allows illegitmate access to a machine.
- User is unaware.
Types of Malware
Blended Attack
Multiple infection/transmission methods used together.
-Blended threats are bundles of malicious programs that combine the functionality of different types of malware such as Trojans, worms, and backdoors.
A blended threat often involves an infection chain that begins with a user visiting a website and then diverted to a malicious URL. After this, social engineering lures will lead the user to download a malicious file which will continue to download additional malicious files.
By using multiple methods and techniques, cybercriminals are able to quickly and surreptitiously spread threats.
Layered security platforms that provide in-depth defense and continuous monitoring are best used against blended threats.
-
https://www.trendmicro.com/vinfo/us/security/definition/blended-threat
-
.
Mobile Code
- Transmitted from remote host to local host.
- Executed without user instructions (i.e. Javascript, VBScript, etc)
- Often comes through browser activity, pages that require code to move location in order to function for user.
- Mobile code, such as a Java Applet, is code that is transmitted across a network and executed on a remote machine. Because mobile code developers have little if any control of the environment in which their code will execute, special security concerns become relevant. One of the biggest environmental threats results from the risk that the mobile code will run side-by-side with other, potentially malicious, mobile code. Because all of the popular web browsers execute code from multiple sources together in the same JVM, many of the security guidelines for mobile code are focused on preventing manipulation of your objects' state and behavior by adversaries who have access to the same virtual machine where your program is running.
-https://www.owasp.org/index.php/Unsafe_Mobile_Code
Trojan
Hidden within legitimate program, not usually self-replicating.
Worm
Does not require user interaction. (Self Replicating)
A computer worm is a type of malware that spreads copies of itself from computer to computer. A worm can replicate itself without any human interaction, and it does not need to attach itself to a software program in order to cause damage.
-
https://us.norton.com/internetsecurity-malware-what-is-a-computer-worm.html
Virus
Request user interaction in to replicate and spread.
Type of System Processes
User Mode
- Runs in private virtual address space.
- Applications are isolated, one crash will not cause another to crash.
Kernel Mode
- All run in a single virtual address space
- Not isoloated from other process.
**Need access to all processes in order to function**
The Versus
Represents sequential machine-code instructions that a processor executes
The primary container (memory structure) for a program being executed
Pointer to OS objects referenced within a process
8 Thread States in Action
Mutex Vs Semaphore
Threads
- Basic unit which OS allocates processor time (Belong to Process).
- Can execute any part of process code
- Including parts currently being executed by another thread.
- Share memory with each other as well as the process.
- Deadlock is possible if the threads are waiting for each other's resources.
- Synchronization (semaphores, mutexes) are used to control access to shared vaiables.
- mutexes-mutual exclusion object-program object that is created sot hat multiple program thread can take turns sharing the same resource, example, access to file.
- Semaphore- are widely used to control access to files and shared memory.
- Client/Server Run-Time Subsystem (CSRSS), maintains a list of threads.
- Threads are part of a execution priority pool 0-31 per processor, highest executes next (most times)**Hinted as testable**
Race Condition-Two threads trying to access the same resource.
Deadlock-When two threads depend on each other (Example: thread depends on thread b value)
Thread States
Initialized
Thread is being created.
Terminated
Finished execution, heading for deallocation in most cases.
Transition
Ready for execution, but paging needed to bring back in memory.
Period of inactivity while waiting for an event.
Thread currently running on a processor.
Standby
Next thread to run, only one per processor per system.
Deferred Ready
Selected to run, but not yet executed. Optimization for scheduling database.
Waiting for Execution, in priority pool.
Handles
- Objects are data structures representing a system resource (file, thread, etc). ID Resources
- Applications can't access objects directly, must obtain a handle.
- Handles for each process are tracked in an internal table known as the Object Manager.
Object Manager-An object consists of a standard header and object-specific attributes. Because all objects have the same structure, there is a single object manager in Windows that maintains all objects.
The object header includes items such as the object name, so that other processes can reference the object by name, and a security descriptor, so that the object manager can control which processes access the system resource.
The tasks that the object manager performs include the following:
- Creating objects
- Verifying that a process has the right to use the object
- Creating object handles and returning them to the caller
- Maintaining resource quotas
- Creating duplicate handles
- Closing handles to objects
https://docs.microsoft.com/en-us/windows/win32/sysinfo/object-manager
- Handles allow a common interface to objects, regardless of underlying changes to the object.
- Handles allow Window to track ACL's for objects during handle creation time.
Paging
Paging is a memory management scheme by which a computer stores and retrieves data from secondary storage[a] for use in main memory.
Page Fault
Overcommited
Page Size
Simple Process States Diagram
During the "Waiting" Page file/Swap space is given.
Detailed Process States Diagram
Example 2 (Win 7)
Example 1 (Windos XP & Windows 7)
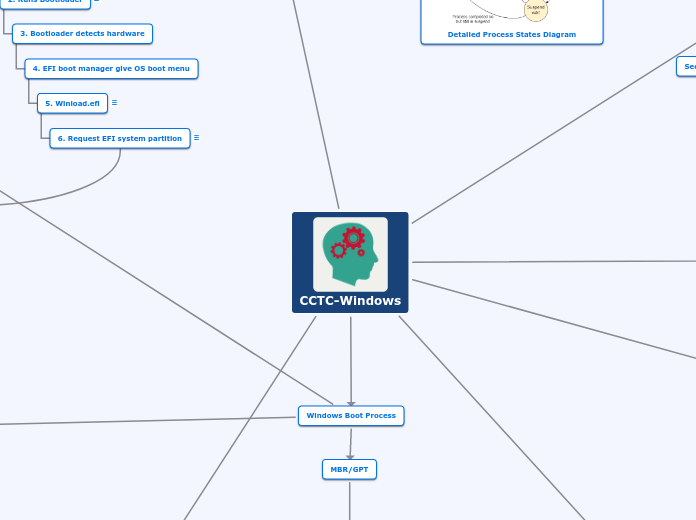
(1.1)EFI/UEFI Boot Process
2. Runs Bootloader
Loads BCD
3. Bootloader detects hardware
4. EFI boot manager give OS boot menu
5. Winload.efi
Extensible Firmware Interface, executes files for the firmware of the computer.
6. Request EFI system partition
Formatted as FAT
Up to 1GB in size
CCTC-Windows
Windows Registry
The Hivelist
\REGISTRY\MACHINE\HARDWARE-Recreated every time the system starts.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc959353(v=technet.10)
\REGISTRY\USER\Security ID number
-Specifies location of files that store the current user profile.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc976065(v=technet.10)
\REGISTRY\MACHINE\SECURITY
-Specifies location of files that store the HKLM\SECURITY key.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc963198(v=technet.10)
\REGISTRY\USER\.DEFAULT
-Specifies location of files that store the HKU\.DEFAULT key.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc963202(v=technet.10)
\REGISTRY\MACHINE\SYSTEM
-Specifies location of ifles that sotre the HKLM\SYSTEM key.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc963201(v=technet.10)
\REGISTRY\MACHINE\SOFTWARE
- Specifies location of files that store the HKLM\SOFTWARE key.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc963200(v=technet.10)
\REGISTRY\MACHINE\SAM
- Specifies location of files that store the HKLM\SAM key.
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-2000-server/cc963197(v=technet.10)
Query
- CLI) reg query [\\Machine\] HKLM\SOFTWARE\TEST
- (PS) get-item -path "HKLM:\software.Test"
- (WMIC) wmic class StdRegProv call EnumValues sSumbKeyName="Software\Test"
Create
- (CLI) reg add HKLM\software\test /v data /d "This is the data"
- (PS) new-itemproperty -path "HKLM:\Software\test" -name "data" -value "This is the data"
- (WMIC) wmic blass StdRegProv call SetStringValue sSubKeyName="software\test" sValueName="date" sValue="This is the data"
Modify
- (CLI) reg add HKLM\SOFTWARE\TEST /v data /d "This is modified" /f
- (PS) set-itemproperty -path "HKLM:\Software\test" -name "data" -value "This is modified"
- (WMIC) wmic class StdRegProv call SetStringValue sSubKeyName="software\test" sValueName="data sValue="This is modified"
Delete
- (CLI) reg delete [\\Machine\]HKLM\SOFTWARE\TEST
- (PS) remove-item -path "HKLM:\Software\Test"
- (WMIC) wmic class StdRegProv call DeleteKey sSubKeyName="software\test"
Forensically Relevant Keys
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run
- HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKU\<SID>\Software\Microsoft\Windows\CurrentVersion\Run
- HKLM\Software\Microsoft\Windows NT\CurrentVersion\Schedule\Taskcache\Tasks
- All Schedules tasked.
- HKLM\SYSTEM\CurrentControlSet\SERVICES|
- Long running programs that dont depend on users.
- HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR
- List of all USB that have been in the system.
- HKU\<SID>\Software\Microsoft\Internet Explorer\TypedUrls
- Show URL history of users.
- HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Profiles\
- Show profiles for network, indication settings, backdoors, and so forth.
General Rule
- Changes to Windows SYSTEM settings require a reboot.
- Changes to Windows USER Settings require a logout/login.
- Changes to Windows POLICY Settings usually dont require a reboot.
- Changes to an APPLICATION require a restart.
- NOT ALWAYS true, but general rules/guidelines.
Components of Registry
Data Types
REG_DWORD .32 bit integar
Max 7FFF, FFFF or 2,147,483,647
REG_LINK
Symbolic links- A link that will take you to the actual location of the data
REG_SZ.String
REG_QWORD
64 bit integer. Max 7FFF,FFFF,FFFF,FFFF or 9,223,372,036,854,775,807
REG_MULTI_SZ
Multi-String values- Multiple strings that are terminated with "\0". Example: "abc\0def\0"
REG_BINARY.Binary Data
Keys & Values
Keys contain other keys (AKA Sub-keys) and/or a collection of property/value pairs. Keys are a container object, much like a folder.
Values store data. Values are non-container objects, much like a file.
Registry Hives
Registry Hive is a group of keys, subkeys, and values in the registry that has a set of supporting files that contain backups of its data.
https://support.microsoft.com/en-us/help/256986/windows-registry-information-for-advanced-users
Remote Hive Keys
HKU/HKLM available via remote tools
Hive Root Keys
HKCC-Current Config
Current hardware profile, information that is gathered at runtime.
HKLM-Local Machine
System related information, Security Account Manager (SAM), Critical boot/kernel functions, 3rd party software, hardware, BCD.dat. Contains all hardware profiles.
HKCR-Classes Root
Files association and COM objects, backward compatibility, and file extension information.
HKU-Users
All accounts on machine, the root key containing the ntuser.dat hives for ALL users.
HKCU-Current User
Individual user settings
Purpose & Role
The Role
Random reads & writes during app use
Application Startup
Licensing data, installed component, software settings/config.
Reads per-user preferences and settings.
Kernel Boot Process
Loads device drivers and system element config.
Initial Boot Process (Pre-Kernel)
List of boot device drivers to load before kernel.
What Is?
Contains System-wide/Per-User Settings
Config and control mechanism for WinOS
Hierarchical Database/Critical System Config
Process States
Additional Notes for Processes
If a process or some type of action can not start right away, the process will be held by scheduler until resources become available.
(Each State has additional notes)
Terminated/Exit
Termination of a process due to a halt or abort.
Waiting
Process can't execute until some events occurs (I/O reads).
Ready
Process ready to execute when given the opportunity (CPU Time).
Running
Process currently being executed (one or more threads executings). **Amount of threads able to run depends on number of CPU cores**
New/Created
- Open file (exe)
- Create initial thread
- Pass to kernel32.dll to check permissions
- Pass to csrss, build structure, spawns first su-thread, inserts into windows subsystem-wide proc list (Additional creates the structure to utilize memory.)
- Starts execution of intial thread
- For real-time systems, processes may be held in "New State" to avoid contention, otherwise moved to "Ready State"
Windows Visualization
●Virtualization is technology that allows you to create multiple simulated environments or dedicated resources from a single, physical hardware system. Software called a HYPERVISOR connects directly to that hardware and allows you to split 1 system into separate, distinct, and secure environments known as VIRTUAL MACHINES (VMs).
Two Components of Virtualization
- Hypervisor
- Virtual Machine
Situational Awareness
- A method of gaining an understanding of the current operating environment on the target machine.
- Applies both defensively & offensively
- Allows you to get an idea of what the system is used for and type of user using it
- Used to decide what course of action are appropriate for the sytem.
Most important Awareness
- Running Processes
- Active Users
- Network Config
- Network Comms
- Logging
- Scheduled Jobs
- Aliases
Risk
Planning/Setup Cost More
Data Compromised Affects New Instances
Honey Pot/Tar Pit
Persistence loss with Machine Restore
Function Loss i.e. copy/paste
Printers and netstat might require additional setup.
Cloud lack of Control Data at Rest
More Upfront Planning & Config
Benefits
Easy to Manage in Enterprise
Use as HoneyPot/Tar Pit
Quick Restoration
Configurable Software
Easy Instance rollback
Fault Tolerance through redundancy
Used as Pivot Point
Provide Persistence
Protected Malware Analysis
Baseline Rapidly Updated
Dynamically Allocated
One Set of Hardware
Windows Boot Process
MBR/GPT
Comparison
Windows 7
Windows 7 has two different types of pre-boot processes.
First 512 bytes sector on HD, reads & loads volume boot record.
3. VBR
Loads bootmgr into memory.
4. Bootmgr
Read Boot Configuration Datbase (BCD)
(Reference)
Windows boot options are stored in the Boot Configuration Data (BCD) store on BIOS-based and EFI-based computers.
BCD provides a common, firmware-independent boot option interface for all computers running Windows 10, Windows 8, Windows Server 2012, Windows 7, and Windows Server 2008. It is more secure than previous boot option storage configurations, because it permits secure lockdown of the BCD store and lets Administrators assign rights for managing boot options. BCD is available at run time and during all phases of setup. You can even call BCD during power state transitions and use it to define the boot process for resuming after hibernation.
Boot menu and memtest
Calls/starts Winload.exe
Calls winresume
5. Winload
Loads NTOSKRNL.exe
Loads dependencies
Loads device drivers
(1) BIOS Boot Process
Windows XP
Pre-Boot Process
1. POST
2. MBR
Loads boot code.
3. Bootcode
Instructions that are run by a computer to start-up. Searches partition table for boot sector and loads NT Loader (NTLDR).
4. NTLDR
Boot manager and system loader (NTFS or FAT). Loads a specific file called boot.ini.
5. NTOSKRL
Starts system, prepares multiple layers of the kernel space. Starts SMSS.exe
6. SMSS.exe
Launches winlogon.exe and Client/Server Run-Time Subsystem (CSRSS), user mode is kicked off. It also launches Win32 and WinLogin
7. Winlogin
Starts Local Security Authority Subsystem Service (LSASS) enforces security policies on the machine, Loads Microsoft Standard GINA DLL (MSGINA) implements the authentication policy, Starts Security Configuration Management (SCM), starts logonui.exe which implements graphical user interface.
- SCM
- MSGINA
- LSASS
- logonui.exe
Networking
Group Policy Object
GPRESULT-query GPO through command line.
-Resultant Set of Policy (RSOP) can be accessed using GPRESULT query, additional information can be found in below link.
https://support.microsoft.com/en-us/help/312321/how-to-use-resultant-set-of-policy-logging-to-gather-computer-policy-i
DC Tools
DSQUERY
-query the directory according to specific criteria.
DSMOD
-modify existing objects in the directory.
DSGET
-display the selected properties of a specific object in the directory.
DSADD
-add specific types of objects to the directory.
Node Types
Computer
Computer node object relate to policies that affect the computer system, ie. startup scripts, firewall configuration, Name Resolution Policy.
User
User nodes relate to user policies and are relevant to only the currently logged on user.
Logical/Physical Structure
Physical
Member Servers
Domain Controllers
In Active Directory, You have multiple Domain Controllers which are equal peers.
Each DC in the Active Directory domain contains a copy of the AD database and synchronizes changes with all other DCs by multi-master replication.
Replication occurs frequently and on a pull basis instead of a push one.
A server requests updates from a fellow domain controller.
If information on one DC changes (e.g. a user changes their password), it sends signal to the other domain controllers to begin a pull replication of the data to ensure they are all up to date.
Servers not serving as DCs, but in the Active Directory domain, are called ‘member servers.’
Active Directory requires at least one Domain Controller, but you can install as many as you want (and it’s recommended you install at least two domain controllers in case one fails).
Sites
An Active Directory site object represents a collection of IP subnets, usually constituting a physical Local Area Network (LAN).
Multiple sites are connected for replication by site links.
Typically, sites are used for:
Physical Location Determination: Enables clients to find local resources such as printers, shares, or domain controllers.
Replication: You can optimize replication between domain controllers by creating links.
By default, Active Directory uses automatic site coverage, though you can purposefully setup sites and resources.
Logical
Tree and Forest
Trees
A tree is a grouping or hierarchical arrangement of one or more domains.
Trees are created by adding one or child domains to a parent domain.
In a tree, all domains share the same contiguous namespace and naming structure.
By adding domains to a tree, you can retain the security configuration through the tree (domain), and allow for administration to be delegated to a single OU or a single domain.
The tree structure easily accommodates organizational changes.
Forest
Are at the top of the Active Directory Structure.
A forest holds all objects, organizational units (OUs), domains, and attributes in its hierarchy
A forest is a grouping or hierarchical arrangement of one or more separate, completely independent domain trees.
Under a forest are one or more trees which hold domains, OUs, objects, and attributes.
Forests have the following characteristics:
All domains in a forest share a common schema.
All domains in a forest share a common global catalog.
All domains in a forest are linked by implicit two-way transitive trust.
Trees in a forest have different naming structures, according to their domains.
Domains in a forest operate independently, but the forest enables communication across the entire organization.
Organizational Units
An Organizational Unit (OU) is a container which gives a domain hierarchy and structure.
It is used for ease of administration and to create an AD structure in the company’s geographic or organizational terms.
An OU can contain OUs, allowing for the creating of a multi-level structure
Domains
A domain is a collection of computers and their associated security groups that are managed as a single entity.
The domain is the core unit of logical structure in Active Directory It can be used to store millions of objects (these objects are considered vital to the network)
Microsoft recommends:
using as few domains as possible
relying on Organizational Units (OUs) for structure
Domains can contain multiple nested OUs.
Features of AD
Signed and Encrypted LDAP Traffic
By default, Active Directory tools in Windows Server operating systems sign and encrypt all LDAP traffic.
Signing LDAP traffic guarantees that the packaged data comes from a known source and that it has not been tampered with.
Interoperability with Directory Services
Active Directory is based on standard directory access protocols, including LDAP version 3, and the Name Service Provider Interface (NSPI), and can interoperate with other directory services employing these protocols.
Because the LDAP directory access protocol is an industry-standard directory service protocol, programs can be developed using LDAP to share Active Directory information with other directory services that also support LDAP.
The NSPI protocol, which is used by Microsoft Exchange Server 4 and 5.x clients, is supported by Active Directory to provide compatibility with the Exchange directory.
Directory-enabled Applications and Infrastructure
Features within Active Directory make it easier to configure and manage applications and other directory-enabled network components.
Active Directory provides a powerful development environment through Active Directory Service Interface (ADSI).
Security Integration
Active Directory is integrated with the Windows Server operating system security since server version 2000.
Access control can be defined for each object in the directory and on each property of each object.
Security policies can be applied locally, or to a specified site, domain, or organizational unit.
Flexible, Secure Authentication and Authorization
Active Directory authentication and authorization services provide protection for data while minimizing barriers to doing business over the Internet.
Active Directory supports multiple authentication protocols, such as the Kerberos version 5 protocol, Secure Sockets Layer (SSL) version 3, and Transport Layer Security (TLS) using X.509 version 3 certificates.
Active Directory provides security groups that span domains.
Replication of Information
Active Directory provides multi-master replication technology to ensure information availability, fault tolerance, load balancing, and other performance benefits.
Multi-master replication allows you to update the directory at any domain controller and replicates directory changes to any other domain controller.
Because multiple domain controllers are employed, replication continues, even if any single domain controller stops working.
Policy-Based Adminsitration
In Active Directory, policies are used to define the permitted actions and settings for users and computers across a given domain, or organizational unit.
Policy-based management simplifies tasks such as operating system updates, application installation, user profiles, and desktop-system lock down.
Client Configuration Management
Active Directory provides new technologies for managing client configuration issues, such as user mobility and hard disk failures, with a minimum of administration and user downtime.
Integration with DNS
Integration with DNS
Active Directory uses DNS, an Internet standard service that translates easily readable host names to numeric Internet Protocol (IP) addresses.
Although separate and implemented differently for different purposes, Active Directory and DNS have the same hierarchical structure.
Active Directory clients use DNS to locate domain controllers
Primary DNS zones are stored in Active Directory, enabling replication to other Active Directory Domain Controllers.
Scalability, Extensibility, Manageability
Scalability
Active Directory enables you to scale the directory to meet business and network requirements through the configuration of domains and trees and the placement of domain controllers.
Active Directory allows millions of objects per domain and uses indexing technology and advanced replication techniques to speed performance.
Extensibility
The structure of the Active Directory database (the schema) can be expanded to allow customized types of information.
Manageability
In contrast to the flat domain model used in Windows NT, Active Directory is based on hierarchical organizational structures.
These organizational structures make it easier to control administrative privileges and other security settings, and to make it easier to locate network resources, such as files and printers.
Centralized Data Storage
All data in Active Directory resides in a single, distributed data repository, allowing users easy access to the information from any location
A single distributed data store requires less administration and duplication and improves the availability and organization of the data.
Global Catalog
The Active Directory domain relies on a global catalog database which contains a global listing of all objects in the forest.
The Global Catalog is held on DCs configured as global catalog servers.
The Global Catalog contains a subset of information – such as a user’s first name and last name – and the distinguished name of the object so your client can contact the proper domain controller if you need more information.
The distinguished name is the full address of an object in the directory.
For example, a printer in the OU CTB in the Ft_Gordon.mil domain might have a distinguished name of:
CN=AcctLaser1,OU=CTB,DC=Ft_Gordon,DC=mil
Listing of all objects in forest
Schema
The Active Directory schema defines objects that can be stored in Active Directory.
The schema is a list of definitions that determine the kinds of objects and types of information about those objects that can be stored in Active Directory.
Because the schema definitions themselves are stored as objects, they can be administered in the same manner as the rest of the objects in Active Directory.
The schema is defined by two types of objects:
- Schema Class object (referred to as schema class)
- Schema Attribute object (referred to as schema attribute)
Schema Attribute Object
Schema Class Object
Local/Domain Accounts
Logon
Credential Providers
In a domain logon
In a local logon
Domain Accounts
Local Account SIDs
Built-In User Accounts
Access Tokens\Security Identifiers
Relative Identifier (RID)
S-1-5-21-547793982-3027706357-987482306-1003
-500-Admin Account
-501-Guest Account
-1000 - Beginning of User Accounts
Security Identifier (SID)
S-1-5-21-547793982-3027706357-987482306-1003
-psgetsid
-WMIC useraccount list brief
Locate SID in Registry
CLI
req query HKU
reg query "hklm\software\microsoft\windowsnt\currentversion\profilelist\{SID}"
WMIC
wmic useraccount get name, sid, fullname
wmic useraccount where sid={sid} get name
wmic useracount where name={name} get sid
Powershell
get-childitem Registry::\HKEY_USERS -ErrorAction SilentlyContinue
get-childitem 'HKLM:\SOFTWARE\Microsoft\WindowsNT\CurrentVersion\ProfileList|'
Security System Concepts
Kernel Security Device Driver (KSecDD)
(Ksecdd.sys) - implements Advanced Local Procedure Call (ALPC) interfaces which kernel components use to communicate with user-mode LSASS.
Network Logon Service (Netlogon)
Secures channel to domain controller and passes logon.
Credential Providers (CP)
Obtains different logon credentials, smartcard, user/pass, biometrics.
Logon User Interface (LogonUI)
Provides user interface to authenticate to system.
Interactive Logon Manager (Winlogon)
Winlogon.exe - Grabs secure attention sequence (SAS), manages interactive logon, creates first process.
Authenticaiton Packages
DLLs that run through LSASS that verify user account credentials and respond to LSASS which generates a token.
Active Directory
Loaded into LSASS (Ntdsa.dll) - Contains a database with information about domain objects.
SAM datbase: HKLM\SAM
Local users and groups along with passwords (encrypted).
Security Accounts Manager (SAM)
Loaded into LSASS (samsrv.dll) - manages users and groups on local machine.
LSASS policy database
Registry area under HKLM\Security that stores security policy settings.
Local Security Authority Subsystem (LSASS)
Local system security policy, user authentication, sending security audit messages to Event Log. Loads Local Security Authority service (LSA, lsasrv.dll).
Security Reference Monitor (SRM):Kernel Mode (ntoskrnl
Defines access token structure, performs object security access checks, generate security audit messages.
Mailslots
- UDP (138)
- One-way Interprocess Communication
- Implemented in Kernel32.dll and msfs.sys
- Acts as a file kept in memory
- Userful for a single process sending broadcasts to multiple processes.
- Max single message size of 424 bytes.
Additional details on mailslots:
https://docs.microsoft.com/en-us/windows/win32/ipc/mailslots
Sockets
A Socket is on endpoint of a two-way communication link between two programs running on a network. Endpoint consists of an IP address and a port number.
Raw
-Enable access to the underlying transport provider.
-Can manipulate the underlying transport, so they can be used for malicious purposes that pose a security threat. Therefore, only members of the Administrators group can create sockets of type SOCK_RAW on Windows 2000 and later.
-IP Address & Port
Datagram
-Enable processes to use UDP to communicate.
-A datagram socket supports a bidirectional flow of messages.
-A process on a datagram socket might receive messages in a different order from the sending sequence.
-A process on a datagrame socket might receive duplicate messages.
-Messages that are sent over a datagram socket might be dropped.
Stream
-Enable processes to communicate using TCP.
-A stream socket provides a bidirectional, reliable, sequenced, and unduplicated flow of data with no record boundaries.
-After the connection is established, data can be read from and written to these sockets as a byte stream.
Host Name Resolution
Steps:
- Does the name belong to the local system?
- Is it in the cache?
- ipconfig /flushdns #flush the DNS cache locally
- Is the name in the host file?
- C:\Windows\System32\Drivers\etc\hosts
- Query configured DNS server?
Query DNS server
Is Name in Host File
C:\Windows\System32\Drivers\etc\hosts
Is it cached?
ipconfig /flushdns
Does name belong to local system?
Remote Procedure Call (RPC)
- Applications load a DLL containing stub procedures for remote functions.
- The stub then calls RPC run-time procedures to locate where the remote procedures resides.
- The stub negotiates a transport mechanism.
- It then calls the procedures on the remote system with the parameters.
- Reverse happens to return data.
7-Steps of RPC
https://www.geeksforgeeks.org/operating-system-remote-procedure-call-rpc/
https://www.ques10.com/p/2133/explain-rpc-implementation-mechanism-1/
Working of RPC
When Making an RPC
Server Message Block (SMB)
Primary remote file-access protocol on Windows Clients and Servers.
SMB 1.0 - used in Windows 2000, Windows XP, Windows Server 2003 and Windows Server 2002 R2
SMB 2.0 – integrated into Windows Vista and Windows Server 2008
-Increased the scale of file sharing, performance and uses HMACSHA-257 instead of MD5.
SMB 2.1 – used on Windows 7 and Windows Server 2008 R2
-Improved file leasing, ensured large MTU support
SMB 3.0 – used on Windows 8 and Windows server 2012
-Increased performance and scaling, has more features for back-up, security and management.
-Uses AES-128-CCM based signing algorithm
SMB 3.02 – Used in Windows 8.1 and Windows Server 2012 R2
-Implemented option to disable CIFS/SMB1 support when it is unnecessary
SMB 3.1.1 – Introduced with Windows 10 and Windows Server 2016
-Supports AES-128-GCM encryption in addition to AES-128-CCM, also uses SHA-512 hash for integrity checks.
-Makes secure negotiation mandatory when connecting to SMB 2.x or higher
SMB Over NETBIOS-TCP 139
Over TCP Stack TCP 445
OSI Model
http://www.tech-faq.com/osi-model.html
TCP/IP Model
Firewall
Security Products
Windows Auditing
Maintain a record of access to secure objects.
At startup (or config changes), LSASS sends the system audit policy to the Security Reference Monitor (SRM).
When an object is accessed, SRM generates auditing messages and sends them to LSASS.
LSASS sends the event log messages on the Event Logger.
Configure for Anomalous Activity
Command Prompt
auditpol /get /category:*
-auditpol /resourceSACL /type:File /view
-auditpol /resourceSACL /type:Key /view
Local Security Policy
-Advanced Audit Policy Configuration Setting
Policy Settings
Global Audit Policy-SACL
Global policy to setup auditing on a ll objects of one type:
File system objects
Registry keys
Object-Access ACE
Audit settings defined on a per object basis.
Auditing settings are contained.
Event Logs
View/Analyze Event Logs-GUI
-Reads in C:\Windows\System32\Winevt folder.
-Locations are configurable.
Command Line Interface
-wevtutil el - show all logs
-wevtutil gli security -get securitg log info
-wevtutil qe security /c:3 -get last 3 events from security log
Powershell
-get-eventlog -logname system -newest 10
CustomLog
Contains events logged by applications that create a custom log. Enables an application to control the size of log or attach ACLs for security purposes.
System
Contains events logged by system components, failure of a driver or other system components to load during startup.
Security
Contains events such as valid and invalid logon attempts, creating, opening, or deleting files or other objects.
Applicatoin
Contains events logged by applications.
Network
Monitors traffic across the wire.
-Inline or passive
-Network Firewalls
-IDS/IPS
-Web/Applicatoin Proxy
-VPN Concentrator
Heuristic Based Detection
Device/software develops a baseline of the system, then looks for anomalous activity.
Has potential to catch zero day attack.
Larger number of false positvies
Signature Based Detection
Device/Software maintains a database of previously identified attack signatures.
Compares activities and binaries to this database to determine a match.
Only catching known signatures.
Signatures require continuous updating.
Small changes to a binary could bypass signature.
Host-based
Runs local, only concerned with that machine.
Some install as a service, newer versions are cloud based.
System Firewalls
Process monitoring, kernel calls.
Directory monitoring
System Setting / Registry monitoring
Log monitoring
Authentication, Authorization, Accounting (AAA)
Application Whitelisting.
User Account Control (UAC)
Limits privileges of user run applications, even when run as Administrator, to prevent the modification of system files, resources, or settings.
Requesting elevated privileges require explicit acknowledgement from user.
User Interface Privilege Isolation (UIPI)
Each process is given a privilege level.
Higher integrity level can send messages to lower level integrity.
Lower can only read from higher
Can be bypassed by signed and trusted applications with the UIaccess manifest setting.
Windows Resource Protection (WRP)
- Additionally, it will now keep the protected files from being installed to begin with, rather than just overwriting them.
- Protected Resources can only be modified by Window Module Installer Service (TrustedInstaller.exe)
- Can protect System Registry keys.
Critical files that are protected and installed by the OS, vistit link for all extensions.
https://docs.microsoft.com/en-us/windows/win32/wfp/protected-file-list
System File Checker (SFC)
sfc /verifyfile=c \windows\system32\winhttp.all-full path to single file.
sfc /scannow-all sytsem files
New Technology File System (NTFS)
Security Descriptor
https://msdn.microsoft.com/en-us/library/windows/desktop/aa379563(v=vs.85).aspx
Security Identifiers (SID's) for owner
https://msdn.microsoft.com/en-us/library/windows/desktop/aa379571(v=vs.85).aspx
System Access Control List (SACL)
Specifies the types of access attempts that generate audit records for the object.
https://msdn.microsoft.com/en-us/library/windows/desktop/aa374872(v=vs.85).aspx
Discretionary Access Control List (DACL)
Specifies the access rights (read, write, execute, delete) allowed or denied to particular users or groups.
https://msdn.microsoft.com/en-us/library/windows/desktop/aa374872(v=vs.85).aspx
Components
Profiles
https://blogs.technet.microsoft.com/wsnetdoc/2009/04/13/spotlight-on-windows-firewall-multiple-active-firewall-profiles-in-windows/
netsh advfirewall-to create.
wf.msi fo -gui
Work/Domain
Most trusted.
Public
Private
Windows Firewall Service
- HKLM\SYSTEM\CurrentControlSet\services\MpsSvc
- Executable hosting the service is svchost.exe
- The hosted DLL is mpssvc.dll
Enable WF Settings
PowerShell
Get-NetFirewallRule | Select Name, Enabled, Direction, Description | Format-list
WMIC
wmic /namespace:\\Root\StandardCimv2 path MSFT_NetFirewallRule WHERE 'DisplayName LIKE "%ICMP%"' get DisplayName, Enabled, Profiles
CLI
netsh advfirewall ?
netsh advfirewall show currentprofile
GUI
wf.msc
Tactical Survey
Volatility
●Volatility is a measure of how perishable electronically stored data is (when electrical power is turned off or fails).
●Order of volatility is important when making decisions about how to respond to a potentially compromised system. A system shutdown is sometimes the worst option forensically, since it may mean the loss of transient (volatile) data held in RAM. Understanding what data is lost at a system shutdown, and what data is lost when drives are replaced or reformatted, will help guide the steps taken to forensically investigate a potentially compromised device.
During an Incident
Consolidate Info
Crawl System for Malicious Items
Targeted Analysis
Trace Indicators to Source
Search for Indicators of Compromise/Symptoms
Cursory Review of Baseline Info
Gather Baseline Info
Order of Volatility
Archival Media
Physical Config, Network Topology
Remote Logging/Monitoring Data
Disk/Other Storage Media
Temporary File System
Routing Table, ARP Cache, Process Table, Kernel Statistics, Memory
Registers, Cache
Phases of Incident Response
Recovery
Continually Monitor
Update SOP, AAR
Lessons Learned
Return network to Normal
Remove VLANs
Eradication
Clean (and monitor)
Key Rotation
Reimage
Know what needs to be removed
Investigation
Where Security personnel determine the priority, scope, and root cause of an incident.
●Attribution
●Avenue of Approach
●Indicators of Compromise
●Vulnerability Assessment
●Forensic Analysis (Static & Dynamic)[4]
●Static Analysis - Static analysis examines malware without actually running it.
■Strings - Seeing what DLLs, functions, headers might be revealed in the strings output.
■OSINT (Open Source Research), Hash the file and check the hash to see if there is anything online about it.
■Running the binary through antivirus tools to verify maliciousness
■Disassemble the binary using a tool such as IDA (Pro)
●Dynamic Analysis - Watching the malware while it is running
○Typically takes place after static analysis techniques have been exhausted
○Binary is run using a sandbox that records all activity and changes caused by the malware
○Monitor all activity using ProcMon, Task Manager, Procexep
○Look for network traffic using TCPView and Wireshark, fake responses using a tool like Fakenet
○Check for registry and file changes with tools like RegShot and sigcheck
○View the programs execution in a debugger such as Ollydbg or WinDbg
Forensic Analysis
Vulnerability Assessment
Indicators of Compromise (IOCs)
Avenue of Approach
Attribution
Containment
Limit the damage caused to systems and prevent any further damage from occurring.
This includes short and long term containment activities.
●Cordon and Clear (VLANs)
●Remove from Network, when Feasible
●Quarantine
●Sandbox
●Patch / Hotfix
Add Firewalls
Add Firewalls
Patch/Hotfix
Sandbox
Quarantine
Remove from Network
Cordon & Clear (VLANs)
Identification
Incident
Unusual Logons
High Traffic Volumes
External devices
Unsual User Privilege
Unknown User Accounts
Unknown Connections
Unusual Activity/Config Outside Baseline
Event
Preparation
This step happens before an incident occurs. Ensure you have the appropriate response plans, policies, call trees and other documents in place and that you have identified and trained the members of your incident response team, including external entities. Ensure that tools and procedures for incident response have been selected and documented. Ideas:
●Have a packing list for every team member so everyone brings everything they need. (Don’t want to not have to call back or make impact purchases while on a IR mission.)
●Ensure all tools are updated (don’t want to show up to a site and have to update your tools on a compromised network)
●Training (team members know what tools they use and their job roles)
●Documentation (Team knows the TTPs that they will be using during the IR)
●Standard Operating Procedures (review SOPs that you will use while on an incident)
●Network Diagrams (if you are able to get Network Diagrams from the sites you might go to.)
●Policies & Procedures (Know these of places that you may go to)
●What are some external entities that might be part of an incident response team (S-6, S-3, SJA, CI, etc.)
●One important preparation item is to enable NTP or another method to keep host clocks synchronized, so that events can be correlated, and forensic analysis uses a consistent time.
Enable NTP
Network Time Protocol (NTP) server.
Incident Response Team
Network Diagrams
Documentation
Policies & Procedures
SOP
Training
Update Tools
Packing List