作者:Motlohi Ramakatsa 6 年以前
271
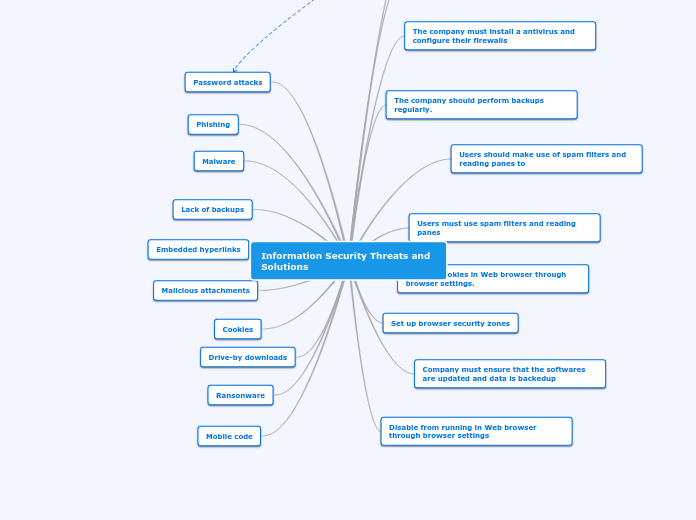
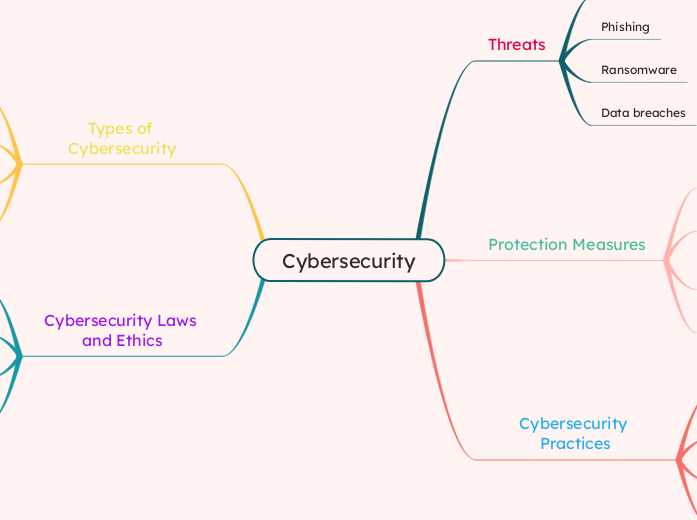
Information Security Threats and Solutions
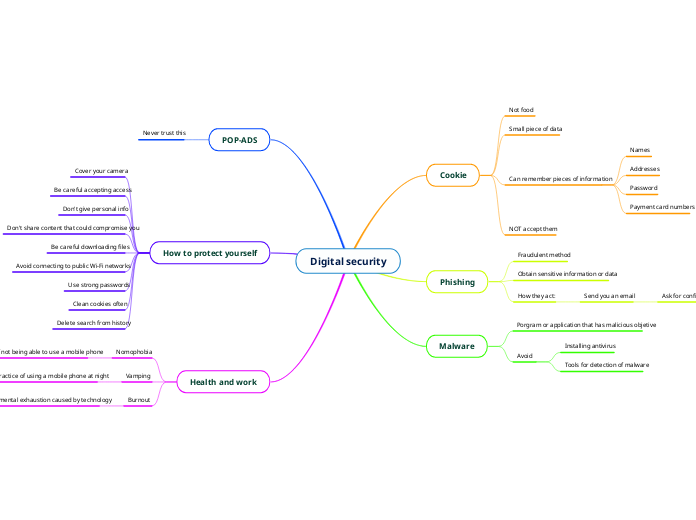
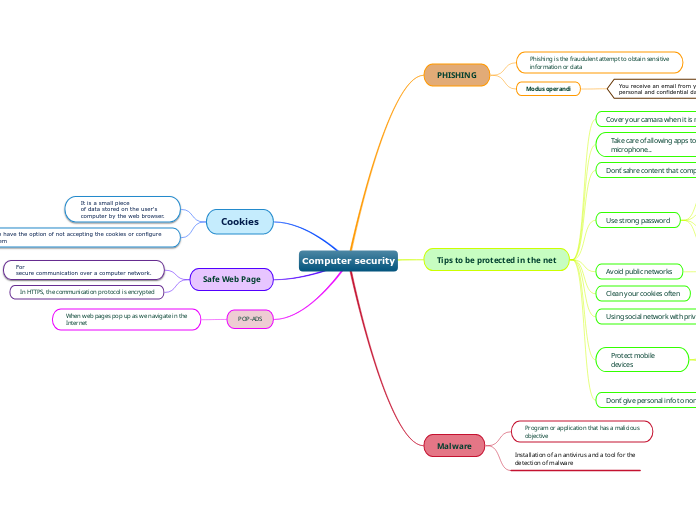
In the realm of information security, various threats such as phishing, ransomware, and malware pose significant risks to both individuals and organizations. To counter these threats effectively, a multi-faceted approach is necessary.