Cloud computing security
Ensuring the security of digital systems involves multiple layers and strategies to protect both data and infrastructure. Authentication and encryption are critical components, verifying user identities and securing information in transit and storage.
開啟
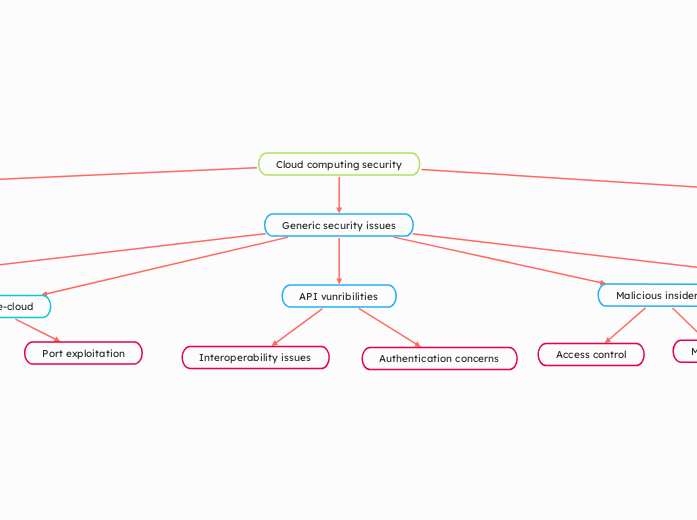
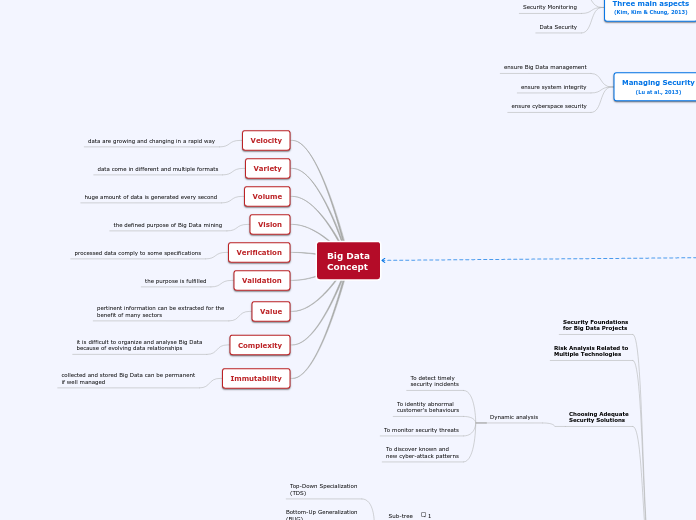
Log analysis IaaS security XML related attacks CLR profiling Service based models Data protection .NET security JVM isolation Session management Java security Programming platforms PaaS security API security Application security TPM protection VM image vulnrabilities VM escape Hyper safe solution Root access risk Virtualization issues Hyper vision vulnerabilities Cache based side channel Information theft Hardware security Memory access Resource sharing risks SOA vulnerabilities Storage security Code injection SaaS security Authentication issues TCB solution Encryption TLS protection Vulnerable objects Data security Storage protection Back up Transit security HTTP examination SSL/TLS Man-in-the-cloud Dos/DDos attacks Port exploitation Information collection Connection limits SYN analysis Counter measures Security policies Account Hijacking SLA compliance Best practices Instrusion detection Authorization credential theft Secure communication Authentication Malicious insiders Monitoring Access control Cloud computing security Generic security issues API vunribilities Authentication concerns Interoperability issues