av Jack Barnes 4 måneder siden
60
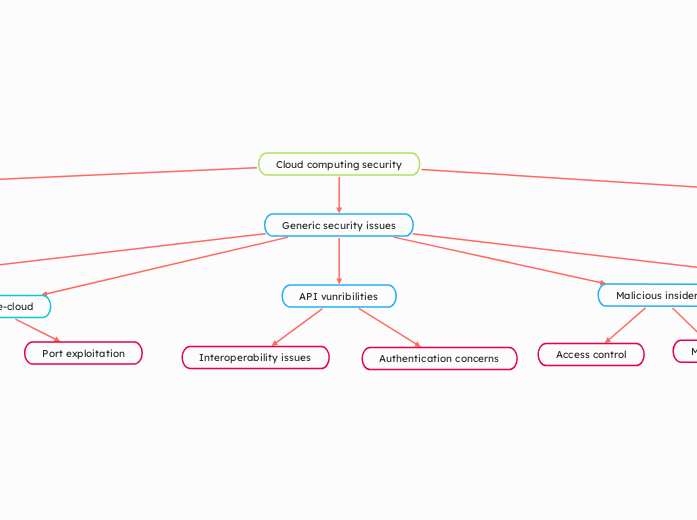
Cloud computing security
Ensuring the security of digital systems involves multiple layers and strategies to protect both data and infrastructure. Authentication and encryption are critical components, verifying user identities and securing information in transit and storage.