Related contents
Threats to the integrity and security of data
Events-based threats
Examples
Natural Disasters
Earthquake
Flood
Fire
File corruption
Software crash
Failure of a HDD
Power-surge
foreseeable, meaning measures can be put in place to reduce their impact
Events outside a user's control that cause a loss of data integrity.
Deliberate threats
A purposeful act by someone to cause a loss of data integrity or breach security measures.
DDOS
cause the web server to performance to suffer greatly, or even crash meaning legitimate users cannot access the website or service running on the web server.
The purpose of a DDOS is to have millions of computers infected with a worm or virus (a ‘botnet’) to simultaneously activate a payload which sends data traffic to a web server in order to overload it.
Distributed Denial of Service attack
Phishing
attempts by scammers to trick you into giving out personal information
Malware
Spyware
Adware
Generates ads in pop-up windows or browser tabs
Malware with the purpose of collecting information
Browsing history (for marketing / advertising)
Email addresses (for spam purposes)
Personal details (for identify theft)
Trojans
relies on the user downloading and running what they think is a legitimate program
A virus disguised as a legitimate program.
Worms
purpose is to spread and consume large amounts of bandwidth on a network, making the network unusable.
replicates itself WITHOUT any interaction or assistance from the user (different from a virus).
Viruses
cannot run by itself
replicate itself
Malicious software
may also contain a payload - a part of some malware that damages the computer in a specific way on a certain date or trigger.
Software designed to cause harm to data integrity.
Making data inaccessible to users
Stealing data
Deleting data
Accidental threats
measures that can be put in place to reduce their impact
Mistakes made by the user.
Characteristics
Characteristics of Networks
Maintainability
Reliability
Efficiency
Level of automation
Operational costs
Processing time
Productivity
Characteristics of Information Management Strategy
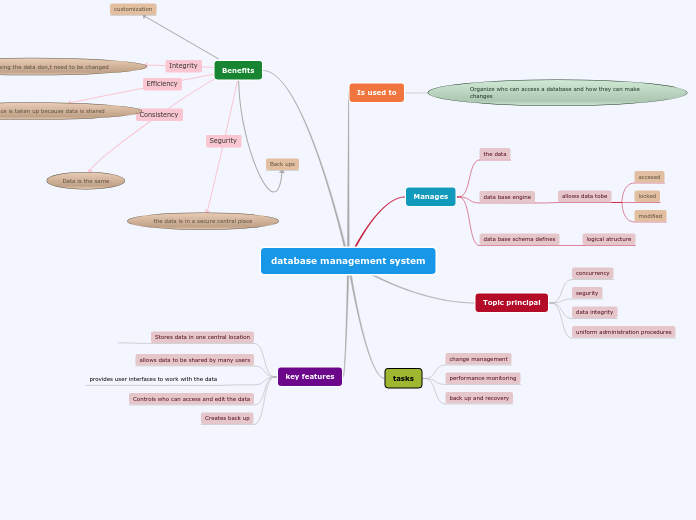
Integrity of data
Security
Ease of retrieval
Currency of files
Characteristics of solutions
Look for effectiveness and efficiency (in evaluation criteria)
Key legislation
Look at the attachment
Networks
Check the slide
Virtual Private Network (VPN)
requires login
connect to a web-server through a different network path then normal to circumvent geo-blocking or make your internet traffic harder to track.
A secure, encrypted connection over the internet using publicly available infrastructure to access an organization's resources or intranet while off-site.
Global system of connected networks (WANs & LANs)
Intranet
accessible from outside the organisation by using a VPN.
stored on servers within the organisation.
An intranet is a collection of private network resources accessible only to an organization's staff.
Wired and wireless networks
Link:
Procedures for handling files/data
Archiving
Archiving frees up space on the primary file server, which in-tern reduces the size of backups
If the files are required, they must be retrieved from the archive system
Storing these files for an indefinite period of time in another, secure system.
Removing files no longer required for immediate access from the main system.
Security
Software
( ensure protection if someone has managed to gain physical access to an information system.)
Software (security protocols)
Transport Layer Security (TLS) and Secure Sockets Layer (SSL)
Asymmetric Key system
Public / Private Keys
Public / Private Key Cryptography
A banking website provides a user’s browser with the bank’s public encryption key.
The user’s username and password (plaintext) is encrypted with the bank’s public key.
The encrypted data (ciphertext) is sent to the banking website.
The banking website decrypts the encrypted username and password with the bank’s own private key.
The bank can send out the public key to all its customers for encryption.
The bank MUST keep its private key safe to decrypt the encrypted data.
Creates secure (encrypted) connections over a network (HTTPS).
firewalls and system protection
System Protection
Anti-malware software
Firewalls
stops unwanted traffic from entering a network
The encrypted data is known as ciphertext.
The original data is referred to as plaintext
Encoding information so that is unreadable without the use of the encryption key or ‘cipher’
access restrictions
Stops a user from accessing resources, even if they have managed to login successfully
Blocking users from data and resources on an IS, based on their classification in the system
access logs and audit trails
Audit Trails
Track the user activity once logged in
Access logs
Can detect strange or suspicious login activity
A record of user login attempts into an IS stored on the server.
usernames and passwords
Prevents unauthorised access to the computer system.
Physical
( protect data while it is being stored - restrict unauthorised people)
equipment
Biometrics
Photograph ID
Iris recognition
Face recognition
Fingerprints
Identifying individuals based on unique physical characteristics.
Barrier techniques
Anything put in place to prevent a person from physically accessing servers or computer equipment holding data.
Guards
Doors, locks, gates, bars, fences, walls
Zoned security strategies
Different keys open different locks, creating ‘zones’ or areas that are only accessible by employees with the required key.
Locks, alarms, fences, gates
Procedures
shredding confidential documents (disposal of paper/hdd)
checking authorisation credentials
backing up
Frequency
Highly dependant on the organisation
Full Backup - Weekly / Monthly
Differential - Daily
Incremental - Hourly / Daily
Medium
Medium considerations
Ease-of-use
Speed (Bandwidth for data transfer)
Cost
Capacity
Cloud
Optical Disc
Tape Drives
HDD / SSD
On site / Off site
Off site prevents larger disasters causing data loss
Types
Incremental
can backup more frequently
Harder to restore (must be in correct order)
To restore
Restore full backup
Restore each incremental backup, in order, from earliest to most recent.
backup after the full backup, only contains files changed for that day, or since the last backup.
Full backup is made first
Differential
Uses less space than daily full backups
To restore
Restore full backup
Restore latest differential backup
Each backup after the full backup, only contains files changed since the full backup
Full backup is made first (total copy of selected files or HDD)
Full
Easiest to restore something goes wrong
Access the latest backup, restore files or whole HDD from there.
largest amount of storage
All data copied to backup medium
original files are NOT removed from the main system
storing the duplicates in a secure location.
Creating a copy of files on the main system
Project Management
Factors that influence the effectiveness
Relevance
Are all the parts of the project plan relevant to the project?
Accuracy
How accurate are the time allocations, milestones and the tasks required?
Readability / Clarity
easy to read?
Completeness
contain all the required tasks, milestones, dependances?
Recording progress and influences
Logs
Adjustment to tasks and timeframes
Annotations
Making notes on the project plan were changes were made.
Concepts
Critical Path
The path followed through the project for its longest duration - this will be equal to the SHORTEST time possible to complete the project.
Time allocation
length of the bar.
Dependencies
represented with arrows
a following task cannot be begin until a previous task has been completed.
Milestones
used to judge whether a project is on schedule or not.
diamond shapes
Major points of progress in a project
goals and objectives of organisations and information systems
Example of the differences
More example
Identify the organisational and system goals and objectives in this case study.
Fred’s law firm has 2 computers. He wants his firm to be more successful, so he is updating his information system. He wants his PCs to run 20% faster to help him produce more accurate communications with customers and to increase income by 10% this year. With increased income, he can spend money on extra secretarial support because he wants his firm to get a reputation for professional excellence.
Organisational goal: his firm to be more successful, reputation for professional excellence.
Organisational objective: increase income by 10% this year
System goal: produce more accurate communications with customers
System objective: his PCs to run 20% faster
Organisations
Measurable statements that describe what needs to be achieved in order to reach a goal.
Help to achieve the mission statement
describe something to achieve.
Mission statement
Guides the actions of the organisation
Usually describes why the organisation exists.
A short statement describing the ultimate goal of the organisation.
Varied sizes
_Single person
_Multi-national company
An entity that has a collective purpose
Information system
support the goals and objectives of the organisation.
Interactions and Impacts
Impact of diminished data integrity on dependant systems
(ALWAYS relate your answer back to the system in question)
Impact on Organisations
Jail
Sued
Customer loss
Reputation loss
Profit loss
Impact on SYSTEMS
Increased time taken to service customer
Incorrect information stored about customer address, letter sent to wrong person
Program crashes
Errors on invoices for new books
Garbage in - Garbage out
Factors affect access of data
Organisation of files
Where files are stored is also important
Use an appropriate file structure
Filename convention
(How files are named)
Using a logical file naming convention
easier and quicker to find a file
Storage Medium
Comparison
hardware device where files are physically saved.
Examples
Hard disk drive
Solid State Drive
USB Flash Drive
Optical media (CD / DVD / BD)
Magnetic Tapes
File size
Measured in Bytes
Transfer speed of data in a storage medium is measured in MB per second (MBps), networks use Mbps
1 Byte (B) = 8 bits (b) - a single 0 or 1
The amount of space on a storage medium (HDD, DVD) taken up by a file.
Advantages and Disadvantages for Stakeholders Affected by IS
Disadvantages
customers deal with IS, not a person
24/7 access - work overtime
loss of 'personal touch' or face-to-face contact with the business
deskilling
loss of jobs, people being replaced by IS
users become dependent on IS for work
start-up costs ($)
conversion of data into the new IS
training costs for staff
significant investment in getting the IS running
Advantages
more effective/efficient for customers
can access own data or history in organisation
can order goods and services online --> reduced time/effort
24/7 access
Upskilling
users of IS must learn new IT skills to use IS
increased efficiency in running the business
less employees needed --> reduced cost
automated systems --> reduced time/effort
stakeholders
For businesses, these include: employees, employers, shareholders, customers
person or group with an interest or concern in something, especially a business
Data Management Practices that Cause Conflict
user permissions
could allow export but prevent import
incompatibility
different software
different setups can cause miscommunication
manual data entry
can be valid and reasonable but incorrect due to human error
converting data from different databases
missing data
differences in data types
differences in field names
Data Mining
conflicts:
reasonableness/relevance
some information found don't make sense or are irrelevant
is there consent for data sharing?
is there consent for data mining?
done by dedicated data mining software
the analysis of large sets of data in attempts to extract patterns and knowledge
Factors Affecting Integrity of Data
Factors:
correctness
whether or not data is right or wrong
(always yes or no)
authenticity
primary data most trustworthy, if not find reputable sources
how trustworthy and proven the data's source is
reasonableness
should fall within a range that makes sense
how much the data makes sense with the source material
(is it related to the context?)
timeliness
1999 data vs 2019 data for current trends
data too old will be irrelevant and not provide an accurate representation of source material
how much the data is within its "use-by-date" and can provide meaningful information
length of time for 'timely' data depends on the data
accuracy
In 2017:
there were 24.5 million people living in Australia
(less accurate)
vs.
there were 24,530,282 people living in Australia
(more accurate)
greater accuracy leads to more precision
how much the data is a true representation of the source material
(how well data is measured)
Integrity
internal consistency or lack of corruption in electronic data
raw facts and figures that have not been turned into information
Information Systems
Output
e.g. visual(monitor), sound(speaker), paper(fax or printer) and touch(gamepad)
data that has been stored or processed by the IS and turned to information
Input
e.g. keyboard, touch screen, microphone, etc.
data that is entered into the IS
should support goals and objectives of organisation's IS
(Not related to organisation as a whole)
(see pg. 3 to 4 for more info)
Goals
e.g. Reduce user errors by 50% OR Remain stable and reliable 99.5% of time
statements that describe something the organisation is aiming to achieve
Objectives
e.g Record all students' attendance and report progress OR Produce annual reports for sales
measurable statements that describe what needs to be achieved to reach a goal
allows for:
reduction in time taken to process data
improved services for customers or clients
sharing of hardware between users
sharing of data between users
combination of _________ to create, control and communicate ideas and digital solutions
Data
includes information (attendance, personal details, etc.) and work (assignments, documents, etc.)
documents/files/statistics created and modified using the IS
Processes
includes general actions (saving files, etc.) and restrictions (access permissions, etc.)
rules to ensure the IS is used properly
Software
includes OS and other websites as well
applications and services used on hardware
Hardware
includes machines and computers used
physical components of IS
People
everyone
the human beings that use the IS
Problem Solving Methodology BBC
Check out slides (have not added all info) - do not delete this list
- U4O2 KK09 - Technical underpinnings of Intranets, Internet and VPN
-----------------------------------------------------
Completed KK
- U3O1 KK01 - Characteristics of Data Types
- U3O1 KK02 - Data Strucutes
- U3O1 KK03 - Design Tools
- U3O1 KK04 - Input / Output and XML
- U3O1 KK06 - Processing features of programming languages
- U3O1 KK07 - Searching - Linear and Binary
- U3O1 KK08 - Trace tables and test data
- U3O1 KK9 - Internal Documentaiton
- U3O2 KK01 - Techniques for collecting data
- U3O1 KK04 - Methods for determining solution requirements, constraints, and scope
- U3O2 KK03 - Analysis - Solution Constraints
- U3O2 KK04 - Analysis - Scope of Solution
- U3O2 KK05 - SRS
- U3O2 KK07 - Evaluation Criteria - Efficiency and Effectiveness of solutions
- U3O2 KK08 - Analysis Tools - Use Case Diagrams
- U3O2 KK09 - Analysis Tools - Context Diagrams and Data Flow Diagrams
- U3O2 KK10 - Design Tools
- U3O2 KK11 - Factors influencing design
- U3O2 KK14 - Project Management
- U3O2 KK15 - Security - Data protection and authentication
- U3O2 KK16 - Styles of modern applicaiton architecture
- U3O2 KK17 - Types of goals and objectives
- U3O2 KK18 - Legal Requirements relating to ownership and privacy of data
- U4O1 KK01 - File size, storage medium and organisation of files affect access of data
- U4O1 KK02 - Data Structures - Associative Arrays
- U4O1 KK03 - Security, archiving, backing up and disposing files
- U4O1 KK04 - Processing features of a programming langauge
- U4O1 KK05 - Sorting Algorithms - Selection and Quick
- U4O1 KK06 - Characteristics of Efficient and Effective solutions
- U4O1 KK07 - Test Data
- U4O1 KK08 - Validation - Existence, Type, Range
- U4O1 KK09 - Usability testing and documenting test results
- U4O1 KK10+11 - Project plans - Recording progress and influences
- U4O1 KK12 - Evaluation of solutions and project plans
- U4O2 KK01 - Reasons why individuals and organisations use information systems
- U4O2 KK02 - Types of goals and objectives
- U4O2 KK03 - Types of interactions (input and output) generated by IS
- U4O2 KK04 - Characteristics of data that has integrity
- U4O2 KK05 - Key legislation that affects how organisations control the storage, communication and disposal of their data and information
- U4O2 KK06 - Data management practices that cause conflict between information systems, including data mining
- U4O2 KK07 - Advantages and Disadvantages for stakeholders affected by the operation of information systems
- U4O2 KK08 - Impact of diminished data integrity on dependant systems
- (too much)grdggdrgdgdthdhfthfthfthfhfhfh kk9
- U4O2 KK10 - Wired and Wireless Networks
- U4O2 KK11 - Threats to the intergrity and security of data
- U4O2 KK12 - Physical and software controls to secure data
- U4O2 KK13 - Hardware, Software, and Technical Protocols used to secure data
3) Development
Documentation
Characteristics of internal documentation
Meaningful names
All controls, variables and arrays in a program should have meaningful names.
This makes it easier to identify their purpose just by reading the name.
Use naming conventions:
=> v, before all variables - vName, vAge
=> CamelCase for controls
_Description of purpose
_Type of Control
_FirstNameLabel, CalcButton
Comments
Purpose
Reminds a programmer what a piece of code was for (its purpose)
Helps team members understand each other's coding
Comments are not executed and have no affect on the performance of an application.
Testing
Types of testing
Trace table
remember to list all the variables given
Store values as they change
Only enter a new value if a change occurs.
Algorithm testing
Example (Question 1 Section B 2018 exam)
testing table
Testing for logic errors (test the program overall)
Example
Useability (Acceptance) Testing
(given to client/user)
Completed by a section of its daily users
Makes sure that solution included all the required functionality
Gives the chance for users to provide feedback before the solution is deployed
Test functional and non-functional requirements from analysis stage.
Once passed the solution is almost ready to be deployed.
Note:
Testing is NOT the same as Evaluation
Testing = does the solution work -->ensure validation is working
Completed BEFORE the solution has been deployed
Conducted by the developer
User Acceptance Test - conducted by the main users of the program to make sure it does what is required.
Test data:
It is extremely important that you choose an appropriate range of test data for each test.
Good test data tests every possible input:
Typical(Values you expect a user to enter)
Edge cases (aka Inside range values - Values at the extreme ends of the allowable range)
Outside allowable range (Values outside the allowed data range)
Garbage input (Invalid data - wrong data type, blank etc.)
Make sure you testing is through but not repetitive - the exam will often ask you to select the best set of test data, don’t select the set that tests the same type of input multiple times!
Focus on testing edge cases.
What should you test?
Effectiveness
Networks - reliability and maintainability
Information Management Strategy - integrity of data, security, ease of retrieval and currency of files
Solution - completeness, readability, attractiveness, clarity, accuracy, accessibility, timeliness, communication of message, relevance and useability
Efficiency - cost, time, effort
Network - productivity, processing time, operational costs and level of automation
Solution - speed of processing, its functionality(?) and the cost of file manipulation
Non-functionality - useability, reliability, portability, robustness, maintainability.
Functionality - Does the solution do what is is supposed to?
Does the solution run?
Validation techniques
Range
(data in an acceptable range?)
Type
(correct data type?)
Existence
(Does any data exist?)
Validation:
ensure users are only allowed to input REASONABLE data.
It DOES NOT check the ACCURACY of input data.
Proper validation ensures that:
Your program does not crash if the user enters unreasonable or unexpected data.
Users are given a prompt if unreasonable data has been entered.
Users are able to re-input data.
Manipulation
(Coding)
Searching algorithms
Binary searching
Algorithm:
Binary searches can only be applied to sorted data.
A Binary search divides a list of values in half and makes a comparison on whether the value searched for is above or below the divided value.
Find the value mid-way through the data and ask:
Is this the value we are searching for?
If so, search is finished.
If not, is the value less than or greater than the mid-way value?
Search the half that should contain the data, ignore the other half.
Repeat until the value is found, or is proved to be not present.
______________________________________________
Very fast to run
More complex algorithm to write..
Great for large data sets, bad for small ones (use linear instead)
--------------------------------------------------------------
A binary search algorithm requires the following:
The array of values
Low - lowest index of list being searched (0)
High - highest index of list being searched (array.Length - 1)
Mid - middle index of list being searched (0)
Found - indicates if the value was found (false)
SearchValue - value being searched for
A loop to run through the search
-If statements
Linear searching
Algorithm:
Similar to a human looking through a list of values.
Look at the first index in an array and check if it contains the data we are looking for.
If not, move to the next index.
Repeat this until the item is found, or you have reached the end of the array.
A Linear search is the only way to search unsorted data.
easy to code
slow (on average it will have check half the data set to find if the value is in an array)
efficient for small data sizes
Sorting algorithms
Quick sort
Uses Recursion - A function or procedure that calls itself.
Divide and Conquer algorithm - data broken down into smaller pieces to be worked on.
Sort Time - Faster and more efficient than selection sort.
Algorithmic Complexity - More complex to write then a selection sort.
Time taken to run the sort changes depending on the “unsortedness” of the data
No. of Comparisons (N the number of items in the array)
Best Case - N * log(N)
Worst Case (rare) - N2
Algorithm:
Pick an element from the array to act as the pivot value. There are many ways to pick the pivot value, but it is often best to select it randomly.
Re-order all the values that are smaller than the pivot value to come before it, all the ones higher to go after it.
The pivot will now be in its proper position
Recursively (run the method again) apply the above steps to the sub-array of elements with smaller values and separately to the sub-array of elements with greater values. Keep applying the algorithm until the array is sorted.
Selection sort
Pseudocode
Easier to code than other sorts
Good enough for small amounts of data
Performs the same, no matter how the data is unsorted.
No. of Passes (how many times it looks at the whole array)
n-1 (n is the number of indexes in the array.)
No. of Swaps (how many times data is moved in the array)
n-1
No. of Comparisons (checking if a value is smaller or larger)
N²
Selection sorts are overall not very good for most situations.
Algorithm:
Look at each item in the array, starting at first value (index 0)
Find smallest value (if sorting small to highest values)
Swap with the value at index (0)
Look at each item in array, starting from the next index (index 1)
Find smallest value
Swap with the value at index (1)
etc.

Term:
Pass
Counted each time an array is cycled through
Comparison
Two array elements are compared to each other
Swap
When two array elements are moved within the array.
Sorting data in an array is effected by
The complexity of the sorting algorithm
How many items there are to sort
How unsorted the data is
Processing features of a programing language
Control Structures (a block of code that controls which lines of code executed)
Iteration / Repetition (Loops)
Differences between for, do, while
Selection (If)
Sequence (Code running line by line in order)
Subtopic
Functions (A procedure that returns a value that can be used elsewhere)
return a result
perform some instructions
can be passed
Method ( an action that DOES something to a variable, object, class)
Procedures (Multiple lines of code that do something (method in C#))
-a set of instructions
modular programming - breaking codes into procedurea
can be called at anytime
prevent duplication
debugging easier
Instruction (a line of code)
Data structures
(a way to store multiple pieces of data)
data element: variables(one variable is not a structure), arrays, records
variables
(one variable is not a structure)
records
why use records instead of arrays?
=>Each array does not make much sense on its own
-need to access the ‘name’ and ‘MobNo’ array to see who the number belongs to.
=>Sorting arrays like this becomes hard
-How do you keep the indexes and values lined up between arrays?
example
contain variables of different data types
group variables together for a particular purpose or to describe a particular object.
associative arrays
includes
_Hash tables
_Dictionaries
Dictionaries
Hash tables
A hash function generates an index to store data, based on a key
Collisions can occur if a hash function produces the same index from different keys.
Searching would return the index value of where the data is stored each time - no linear or binary searching required.
data stored as: key : value pairs
purpose:
organise data -> retrieval easier, esp for large data
One dimensional arrays
-only store values of the same data type, that are referenced with an index.
-usually start at 0 (beware: can start at 1 if the question says so )
4) Evaluation
Note:
Evaluation = did the solution meet its goal?
Completed AFTER the solution has been deployed
Conducted by the users and organisation
Relate back to system goals, objectives
Can use measured in terms of Efficiency and Effectiveness
Report
findings must be presented in the form of a written report.
Strategy
Using evaluation criteria in the Design stage --> evaluate efficiency and effectiveness during design
Collect information using Surveys, Interviews, Observations - just like collecting data for the solution requirements activity.
Technique for collecting data
Observations
Watching and recording how a system is used, or how it performed.
Unobtrusive
Time consuming
Must choose appropriate time to observe
Users may behave differently if they know they are being observed.
Surveys
Structured questions
Multiple-choice
Scale
Short answer, long answer text
Easier to process, not as detailed
Short time taken for multiple responses
Some people don't like filling in surveys
People sometimes write down what they THINK they do, not what they ACTUALLY do.
Online (Google Forms)
Interview
Qualitative data
Prepared questions, but can elaborate or move onto other topics
Harder to process
Takes more time, especially for multiple interviews.
Voice recorder, camera etc.
information to collect
Information about the current system:
What is the current system used for?
What works?
What doesn’t work?
What does the new solution need / require? (Solution Requirements)
How well has the solution met its goals?
2) Design
Evaluation criteria
effectiveness
usability
(is software easy to use?)
relevance
(is output relevant to required functions?)
communication of message
(is it easy to understand info?)
timeliness
(is it up-to-date?)
accessibility
(does solution cater to people with disabilities?)
accuracy
(is output correct and precise enough?)
attractiveness
(does solution look good?)
readability/clarity
(is it easy to read the output?)
completeness
(does required info get produced?)
efficiency
(cost/time/effort)
less cost/time/effort = better
cost of file manipulation
use more efficient algorithm
minimise time taken by solution to change files
functionality
does app address the tasks it was designed for?
output generated at reasonable time?
can data be entered quickly?
Solution design
Styles of application architecture
Internet
Example: Google Docs
Most processing occurs on the server, rather than the user computer.
require the use of the internet to function.
Peer to Peer
No connection to a central server
processing and data are shared between peers (users).
Rich Client
Example
Microsoft Word
requires some connection to a central server.
does most of the processing of data on the client (users) computer.
Mobile
Usually, will not require internet connection to function (apart from the initial download).
Interface needs to be designed to work with touch input.
Larger icons, less text on interface
Mobiles devices, such as smartphones and tablets.
factors influencing design
marketability
(easy to sell?)
improve marketability by improving above factors + effiviency and effectiveness
how easy will software be to sell?
measure of how much can be sold
interoperability
(work with other systems? aka portability)
must be compatible with other software packages
(e.g. data in XML works with other programs)
security
(also affects coding)
authentication
Single-Sign-On (SSO)
Login - Username and Password
data protection
must comply with Privacy Act
needs to protect sensitive data
encryption
affordability
(cost/development budget enough? reasonable price for user?)
usability
(easy to use? target audience?)
design tools
mock-ups
Hand drawn visual representation of the solution.
Provides the layout and relative positioning of all controls on a form.
Labelled to indicate how the solution is used.
data dictionaries
Data dictionary example
defines all data elements (variables and arrays) in program
size
(no. of characters)
data type
(characterised by the kind of operations)
Note:
Correct data type benefits:
-efficient use of storage (e.g integers use less memory)
-speed up performance
-calculations can be performed?
boolean
True/False only
character
(cannot use for calculations)
string
Examples:
John
Computer
ID785342
mark@telstra.com.au
0407897235 - a 0 at the front cannot use a numeric data type!
a collection of individual characters
(Any single alphanumeric characters and symbols)
numeric
(can use for calculations)
date
Stores date and time values
DD/MM/YYYY, HH:MM:SS.MS
double
Any number, including decimals up to 15-16 digits
greater precision than a float
floating point
Any number, including decimals of up to 7 digits
greater precision in stored values
integer
Whole numbers (+/-)
purpose of data
name of variable
pseudocode
(before coding)
Note:
EXPECTED outcome is based on the description of the algorithm in the question stem
The ACTUAL outcome is based on the pseudocode algorithm.
Structured English
Write down the methods for your program to describe it
Language independent
You should be able to read an algorithm in pseudocode, then write the algorithm in any programming language you are familiar with.
iteration (loops)
loop through an array
For i = 0 to len(arr)
For/EndFor
(for loop)
While/EndWhile
(while loop)
Repeat/Until
(do loop)
selection (if statements)
Must Endif
indent code
If/Then/ElseIf/Else/EndIf
assigning values to variable
name ← user input
age ← 16
to access file contents
Until End of File
(do loop)
While Not End of file
(while loop)
keywords are bold
Pseudocode summary
object descriptions
describes objects/controls in solution
formatting info
(font, size, colour, alignment)
attached procedures/functions
purpose
type
name of control
Reasons for using design tools
_Represent solution before development begins
_Generate, brainstorm faster
_Ensure meeting the requirement of the client
1) Analysis
SRS
(Software requirements
specification)
Content of an SRS
SRS is done during analysis
_breaking down a problem into component parts
_providing input to the design stage
_serving as a reference point for further stages of the problem-solving methodology.
Scope of solution
(describes the boundaries or parameters of the solution)
list of what the program cannot do
list of what the program can do
Solution constraints
usability
ease of use
usefulness
legal
privacy
copyright
social
users' level of expertise
technical
security
compatibility
availability of equipment
capacity (storage)
speed of processing
economic
time (how much time do we have?)
cost (how much money do we have?)
Solution requirements
Analysis Tools
use case diagram
UCD symbols
Data flow diagram
(shows movement of data)
DFD symbols
Context diagram
interaction between the organisation and external entities
non-functional
attributes
reliability
(same output every time?)
portability
(work in/ move to different environment?)
robustness
(no crashing?)
maintainability
(easy to update/add?)
usability
(easy to use?)
functional
functions
Validation
Data manipulation (process)
output
input
xml file formats
Easy to edit and read by humans and software.
XML is CASE sensitive.
XML is an open-source file format.
XML files can be directly edited with a Text Editor (Notepad), or by instructions written in an application.
XML tags cannot start with a number, xml, or have spaces.
XML = eXtensible Markup Language
XML files are used to store and transport data between software.
provides a common structure for sharing data between applications.
Uses tags to describe data, similar to HTML.
CSV (comma separated value) files are similar, but only contain raw data, whereas XML files have field names and structure.
XML files give structure - they show which pieces of data relate to each other through indentation.