arabera Артём Беляев 2 years ago
132
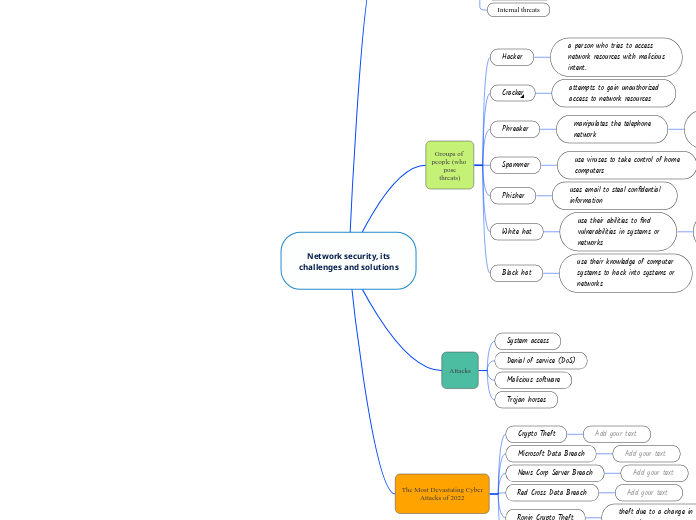
Network security, its challenges and solutions
In recent years, network security has become a critical concern due to the increasing number of cyber attacks targeting sensitive information and financial data. High-profile breaches such as those involving Microsoft, Cash App, and News Corp have highlighted the vulnerabilities in existing security protocols.